Beginning of this year, GlobalSign and Armorize established a joint platform to scan for compromised websites serving malware to visitors.
On July 1st (Friday), we noticed that some of the compromised websites had iframes pointing to www.camcert.gov.kh, which is Website of National Cambodia Computer Emergency Response Team (CamCERT) .
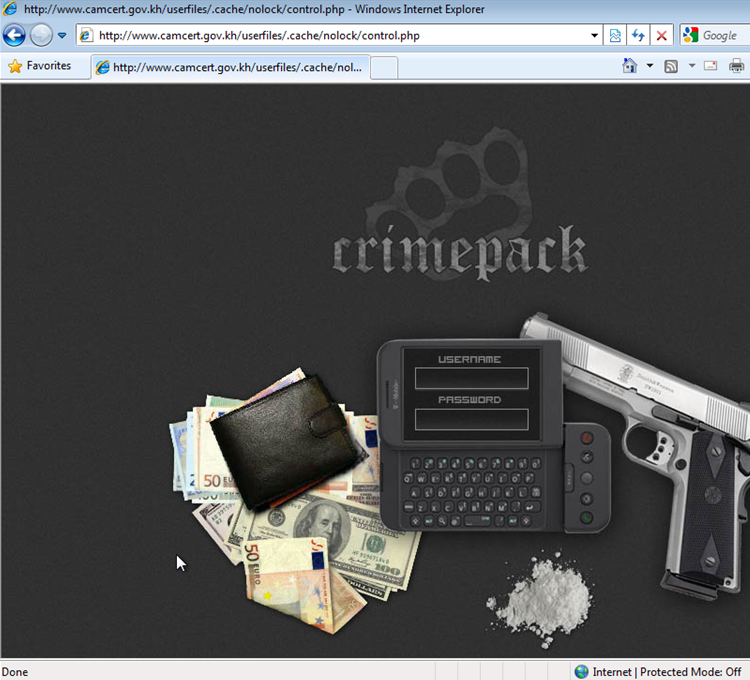
We quickly check out CamCERT's website and confirmed that it's been hacked into and injected with CramePack, which is an Web malware (drive-by download) exploit pack that supports exploits for CVE-2006-0003, CVE-2010-0806
, CVE-2009-3867, CVE-2010-0806, CVE-2007-5659, CVE-2009-0927, CVE-2008-2992, and CVE-2009-3269.
The compromised websites contained an injected piece of javascript that generated an iframe pointing to www.camcert.gov.kh:
The iframe generated was:
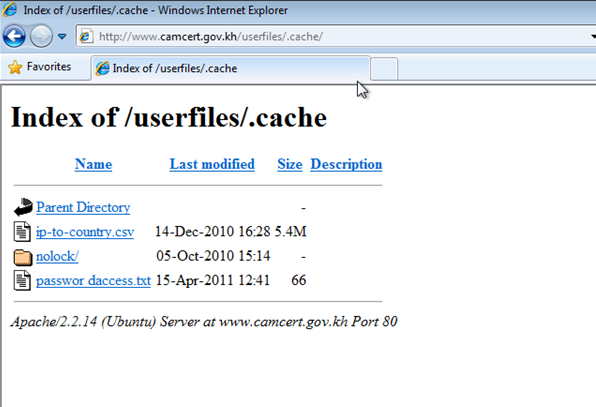
http://www.camcert.gov.kh/userfiles/.cache/nolock/index.phpCrimepack was injected into the "nolock" directory under http://www.camcert.gov.kh/userfiles/.cache :
And pointing one's browser to http://www.camcert.gov.kh/userfiles/.cache/nolock/control.php and using Crimepack's default username "crimepack" and an empty password logged us into Crimepack's UI, as shown on the first screenshot of this post.
We quickly notified CamCERT, and a few hours later we received an email indicating that they have handled the matter.
Here's GlobalSign's account of this incident.
Read more (rest of article)...